Anthem is a beginner’s Windows box on TryHackMe. Below is a detailed walkthrough of the steps to follow to attain the root flag on this box.
Task 1
The first step, as usual, is to run nmap with nmap -sC -sV -T4 [machine ip] after a few minutes, this will display what ports are open.
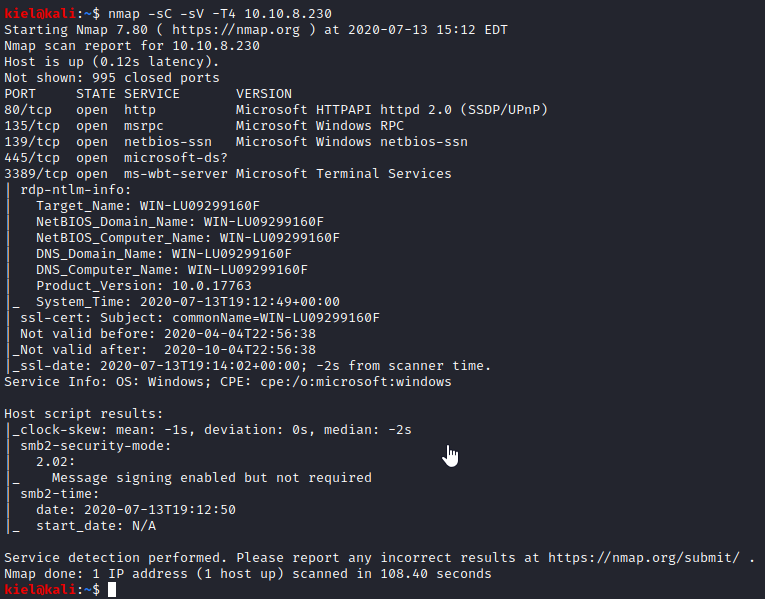
It appears that HTTP, SMB, and RDP are open. The port for HTTP is the answer for Question 2 (question 1 does not require an answer) and the port for Microsoft Terminal Services is the answer to Question 3. Let’s start by visiting the website in our browser. It appears to be a blog of some sort.
This challenge said no brute force is required, and everything can be done via browser or RDP. Let’s look at what the next few questions are asking for.
Question 4 gives a very big hint in the question itself, as it asks for a page web crawlers check for. The most common one is robots.txt, which is the answer to this question. Visiting that page at http://[machine ip]/robots.txt shows you a few directories that are disallowed, but the first line appears to be a potential password, which is the answer to this question.
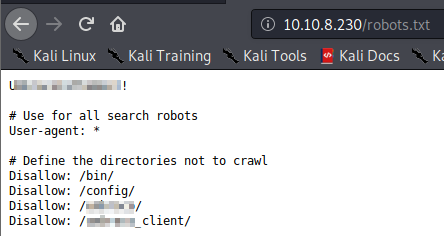
Question 5 asks what the CMS is that is being used. In robots.txt there are some directories that have been disallowed that have been obfuscated above. This is the answer to that question.
Question 6 asks what the domain is. The main page, as shown near the top of this walkthrough, mentions Anthem.com, this successfully solves this question.
Question 7 asks for the administrator of the blog. Clicking on the A cheers to our IT department post presents you with a poem as shown below.
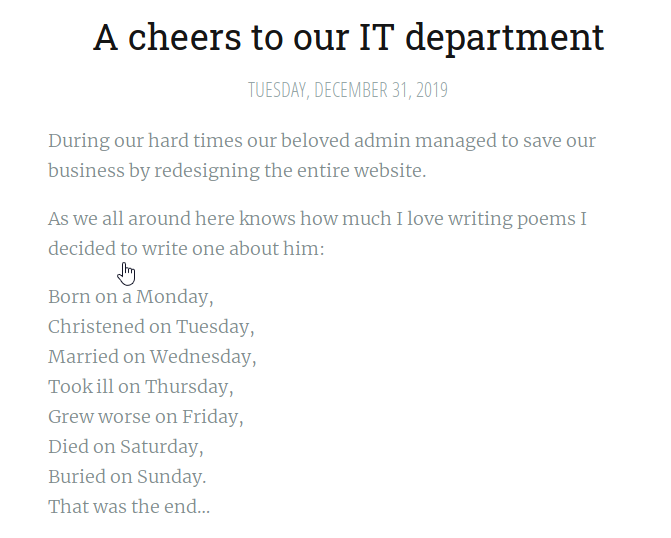
Searching this poem on Google gives you the author of the poem, who is the administrator.
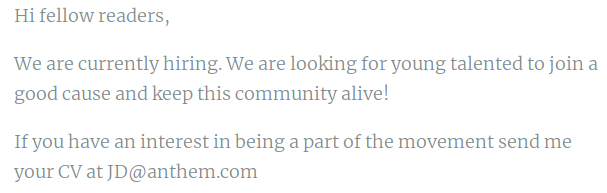
Question 8 asks you for the administrator’s email address. On the first post on the blog, there is an email address present, jd@anthem.com. It appears that the email addresses are the employee’s initials. The answer to this question is the initials of the administrator uncovered in Question 7 followed by @anthem.com.
Task 2
Task 2 asks for help spotting flags. Let’s see what we can uncover. Question 1 provides a hint asking if we have inspected any of the pages yet. Let’s inspect each of the pages, starting with the main home page.
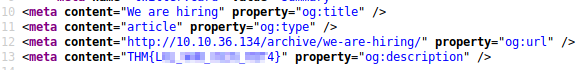
Near the top in the meta content section is the 1st Flag.
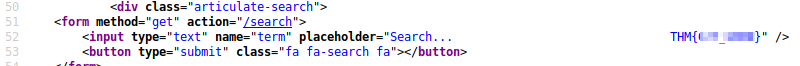
Further down on the source of this page is the 2nd Flag.
The 3rd Flag gives a hint of Profile. You are able to click on Jane Doe on the bottom of the first post (We are hiring), which takes you to her profile page, which contains the flag.

The 4th Flag asks if you have enumerated all of the pages. There are only a few present on this site, so let’s look at each of them. The 2nd post (A cheers to our IT department) meta tags contain this flag.

Task 3
The 1st Question here does not ask you to answer a question, but asks that you log into the box using the info you have gathered. While reviewing the above questions, I attempted to use the username uncovered for the administrator’s email address along with the password in the robots.txt file. I was able to successfully login with these credentials. I logged in with Remmina using the IP of the box along with these uncovered credentials.
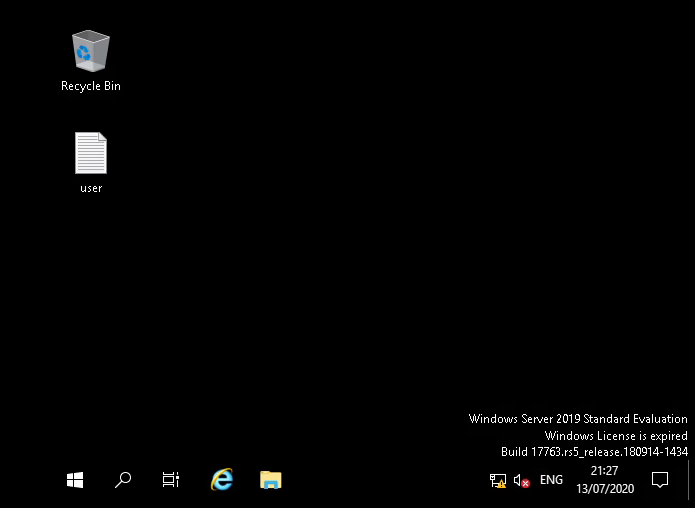
The 2nd Question wants you to get the contents of the user.txt file on the desktop.
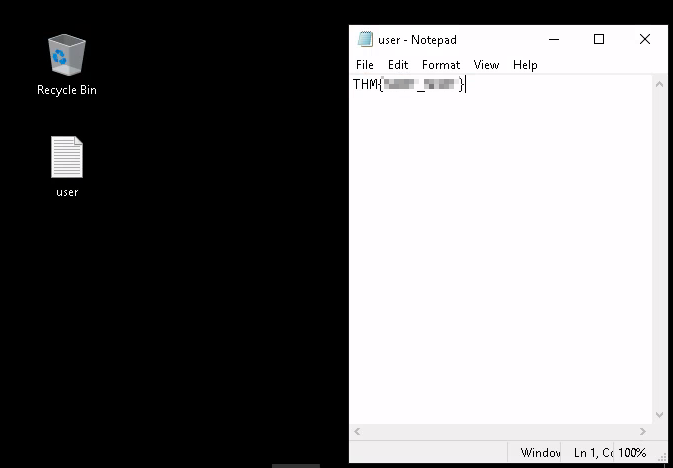
The 3rd Question wants you to find a hidden file based on the hint. Let’s open file explorer and enable viewing hidden items.
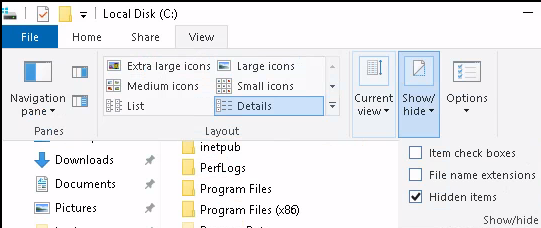
Now, navigate to the root of C:, and there is a hidden folder called backups.
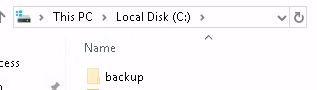
Inside that folder is a file named restore.txt, but we are not able to open it.
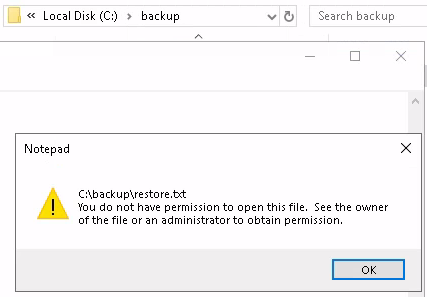
Let’s right click on this file and select Properties. From here, select Security and then click on Edit. Next, click on Add… and the below box should pop up. Type in username you are logged in as and press Check Names. Press OK once the name has been checked.
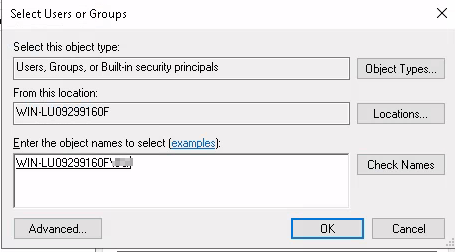
Next select Full Control and then click on OK.
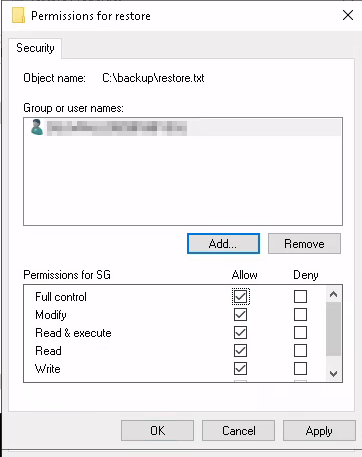
Click the X in the upper right hand corner of the Properties screen and then double click on restore.txt to open the file. There is a phrase in here which is potentially the administrator password.
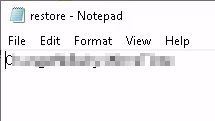
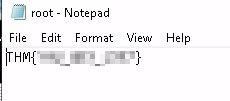
Let’s log off and connect as Administrator via RDP with Remmina with the password you just uncovered. On the desktop is root.txt. Open the file to get your final flag (Question 4) for this challenge.