A few months ago, Joe Helle made a post about how he found some CVEs in open source software one night. I highly recommend reading his article, as it has a wealth of information on what to do if you find a vulnerability in a piece of software. While there is a shortage of people working in cybersecurity, it seems that employers are still very picky about filling these types of roles. Finding a CVE of your own can definitely help you stand out. Here’s the two CVEs I was able to find:
CVE-2021-38602
A stored cross site scripting vulnerability is present on the Article editing page in version 5.8.7 of PluXML. User input is not properly sanitized in multiple fields.
Vulnerable Fields:
- Headline (optional):
- Content:
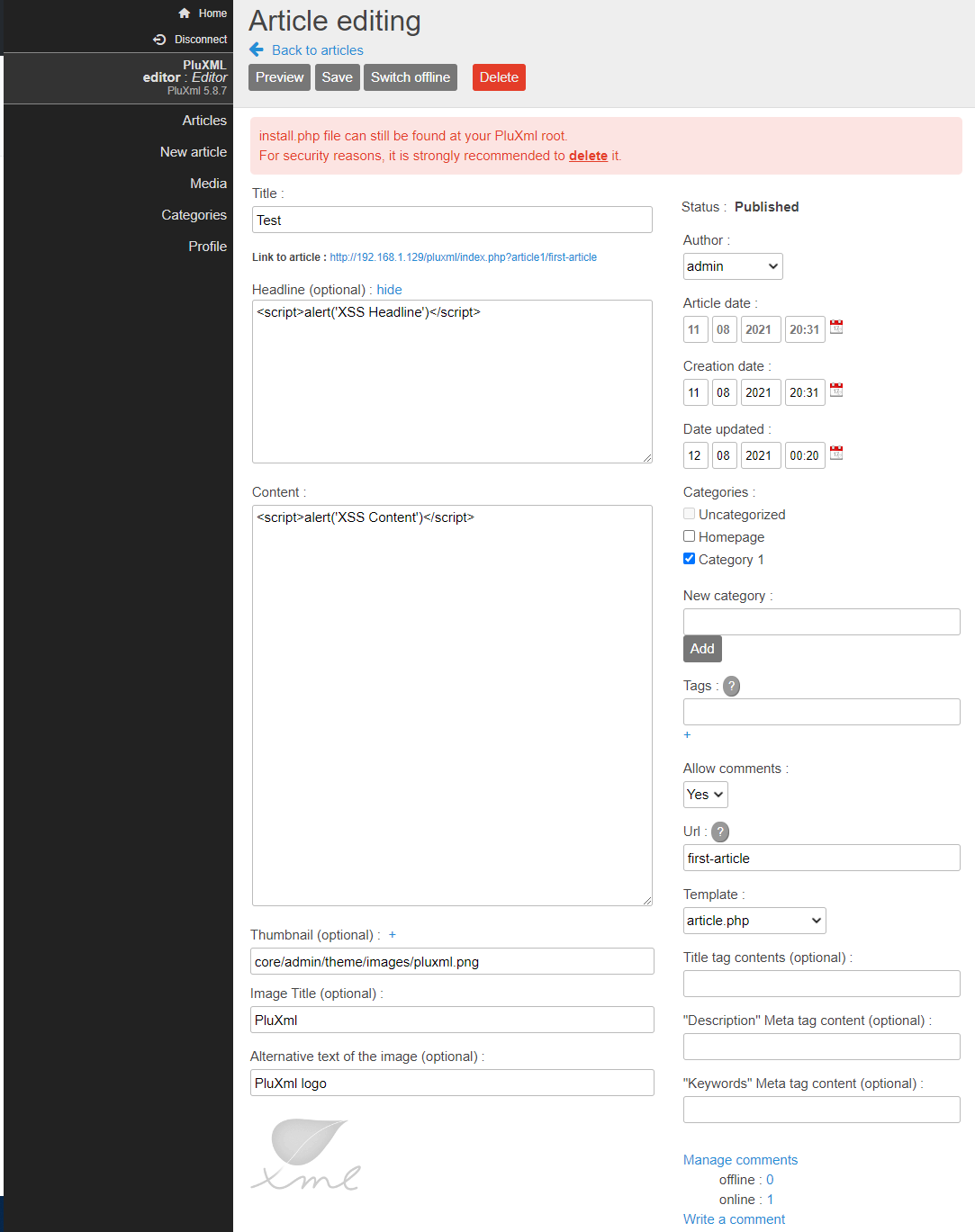
Once inserted, XSS can be triggered by visiting the posted article at the link mentioned under Link to article: near the top of the page.
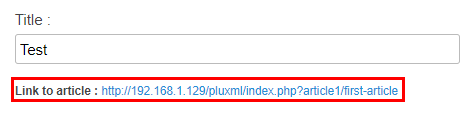
Headline Stored XSS Example
Content Stored XSS Example

CVE-2021-38603
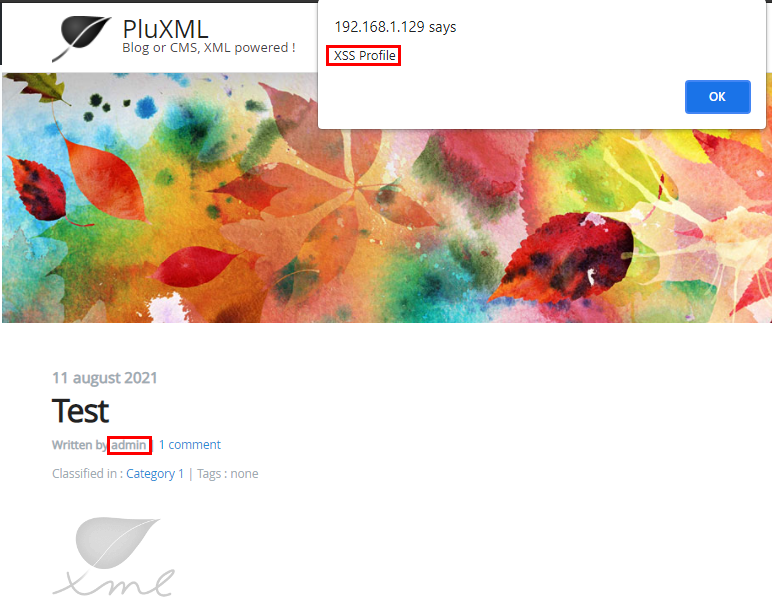
A stored cross site scripting vulnerability is present on the Profile edit page in the Information: field for each user.
http://<hostname/server ip>/core/admin/profil.php
Vulnerable Fields:
- Information:
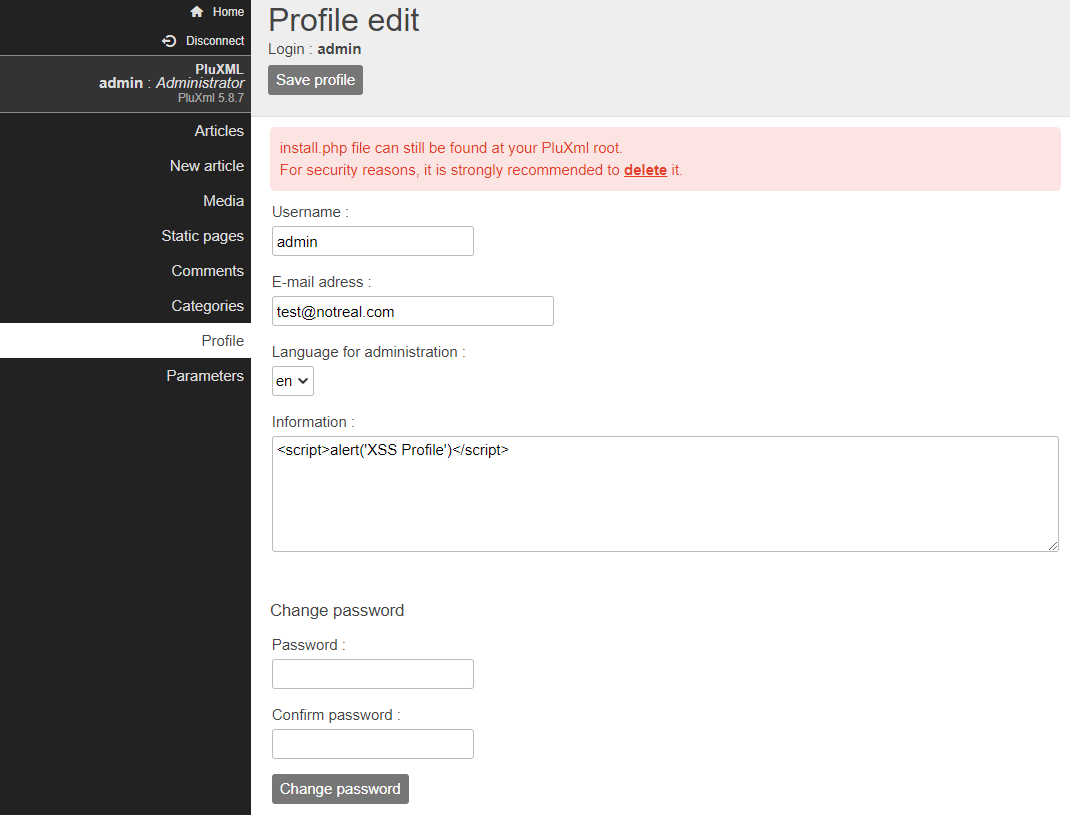
Once inserted, XSS can be triggered by visiting any page/article created by that particular user.
There is a wealth of open source software out there that can be tested upon. Here’s a few lists to get you started!
https://github.com/awesome-selfhosted/awesome-selfhosted
https://github.com/johnjago/awesome-free-software